Control Center Security Best Practices
HYPR Control Center Standard
This page describes the best security practices to follow in the Control Center when configuring HYPR Passwordless and the HYPR Mobile App for your organization.
The Big Picture
For the best results, don't forget to implement HYPR Passwordless Security Best Practices and HYPR Mobile App Security Best Practices.
Offline PINs
PIN Length
The PIN Length setting controls how many alphanumeric characters users will need to enter on the workstation login screen when their mobile device or the workstation itself is offline.
To balance security concerns with user convenience, the Offline PIN length is set to eight characters by default. However, longer PINs are recommended for additional security. You can set the length to between six and thirteen characters as your organization requires.
To change the default length, enter a new value under Workstation Settings > PIN Length in the HYPR Control Center.

Number of Offline PINs
The Number of Offline PINs setting limits the number of times a user can access their machine while offline before they need to do an online login to refresh their PIN count.
The default is 25 but you can set the number anywhere from ten to 100.
To change the default number, enter a new value under Workstation Settings > Number of Offline PINs.

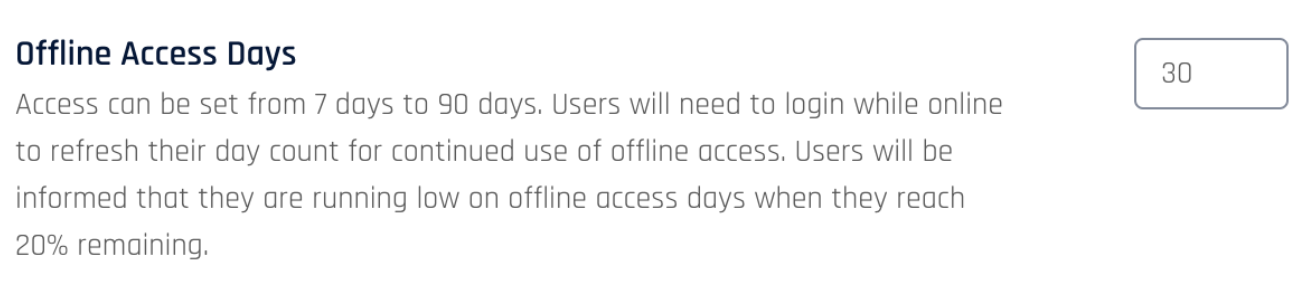
Offline Access Days
The Offline Access Days setting establishes the validity period for Offline PINs. Users have to perform at least one Online Authentication within the configured time period to refresh their already received PINs.
The default is thirty days but you can set it anywhere between seven and 90 days.
To change the default access days, enter a new value under Workstation Settings > Offline Access Days.
Keep It Fresh
By setting Offline Access Days and the Number of Offline PINs higher, you risk partially compromising security because an Online Authentication won't be required for a longer period of time. Online Authentication is inherently more secure since it always uses the latest authentication policy and ensures the user is still authorized to access the workstation based on your Active Directory and HYPR Control Center settings.
Recovery PINs
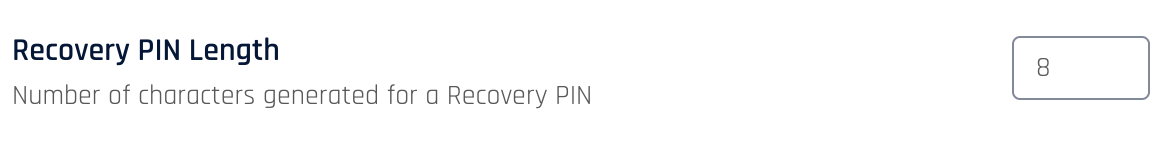
PIN Length
The Recovery PIN Length setting controls how many alphanumeric characters users will need to enter on the workstation login screen when they request a Recovery PIN. To balance security concerns with user convenience, the Recovery PIN length is set to eight characters by default. However, longer PINs are recommended for additional security. You can set the length to between six and thirteen characters as your organization requires.
To change the default length, enter a new value under Workstation Settings > Recovery PIN Length in the HYPR Control Center.
Recovery PIN Counter
The Recovery PIN Counter setting limits the number of Recovery PINs generated during the pairing process and subsequently available in the Control Center for an Admin to provide to the user. The default is five but you can set the count anywhere between one and ten.
Setting the count higher potentially allows users to access the computer without the Mobile App or a security key for a longer period.

To change the default count, enter a new value under Workstation Settings > Recovery PIN Counter in the HYPR Control Center.
Recovery PIN Lifespan
The Recovery PIN Lifespan setting establishes the validity period for the PIN. The timer starts when the user logs in with the PIN for the first time and when it expires the user will either need to contact an Admin to receive a new PIN or use the Mobile App to log in. The default is 72 hours but you can set the lifespan anywhere between 24 and 72 hours.
Setting the lifespan higher potentially allows users to access the computer without the Mobile App or a security key for a longer period.
To change the default lifespan, enter a new value under Workstation Settings > Recovery PIN Lifespan in the HYPR Control Center.

Limit Magic Links to a Single Use
When this feature is enabled, Magic Links are accessible for up to 24 hours and are not expired by simply clicking on them. This function prevents email security software from expiring Magic Links when providing analysis. The first successful access to a Magic Link nullifies further attempts using that link.
Contact HYPR Support if you wish to enable this feature in your environment.
Integration Security
Microsoft AD FS Configuration
The HYPR for AD FS integration works as a plugin for AD FS. AD FS is in charge of handling the initial steps of the login process and HYPR provides the passwordless authentication capabilities. As such, configuration related to HTTP headers and security mechanisms is performed within the AD FS server.
We recommend following Microsoft’s guidance to customize the HTTP headers in AD FS and enable the available security measures, including but not limited to:
- X-Frame-Options, to avoid potential clickjacking scenarios involving the login process;
see Microsoft's article: Customize HTTP security response headers with AD FS 2019 - X-XSS-Protection, to prevent Cross-Site Scripting attacks
- HTTP Strict-Transport-Security (HSTS), to force the use of HTTPS connections
Updated 5 months ago
