Entra/Azure AD: HYPR Enterprise Passkey
Control Center Standard: Integrations
HYPR Enterprise Passkey (a.k.a. the FIDO2 Mobile Authenticator pattern) enables your HYPR Mobile App-enabled device to act as a FIDO2 security key when authenticating through Microsoft Entra/Azure AD. Once implemented, Entra will see any affected mobile devices as hard token passkeys.
HYPR Enterprise Passkey can be integrated with several different workstation setups, depending on your environment:
- Non-domain-joined: Windows workstation is not joined to any domain and is owned by the user; the user can login via a Microsoft account or an account local to the machine
- On-premises Active Directory: Windows workstation is joined to an on-premises Active Directory and is owned by the user; the user can login to any workstation which is joined to same domain using the user credentials on the domain controller
- Azure Domain-joined: Windows workstation is joined directly to the Azure AD cloud; the user can login to any workstation joined to Azure AD using the user account in Azure AD
- Hybrid Azure Domain-joined: Windows workstation is joined to both the on-premises Active Directory and to the Azure AD cloud; the user can login using the user credentials on the domain controller.
What's Your Status?
Use the following command to check the status of a Windows workstation:
dsregcmd /status
What You’ll Need
Server/Tenant
- Make sure you have the Entra/Azure tenant available and an account that exists on the
\*.onmicrosoft.comdomain with Global Admin Access - You should have an Intune account on the
\*.onmicrosoft.comdomain with Global Admin Access with Intune licenses- Enable the FIDO2 Security Key Credential Provider in Intune:
Workstation
- Currently the workstation/VM OS must be Windows, as macOS is not yet supported
- Entra/Azure domain-joined or hybrid-joined VMs or physical laptops with which to test
- Ensure the Windows Workstation OS patch level requirements are met
- HYPR Passwordless client must be installed on the affected workstation(s)
- Workstation support for FIDO2 security keys will vary depending on how the workstation is joined:
- Microsoft does not support FIDO2 security keys for authentication to Active Directory workstations
- Microsoft does support FIDO2 security keys for authentication to Hybrid Azure AD joined workstations
- Microsoft does support FIDO2 security keys for authentication to Azure AD joined workstations
- Hybrid workstations only:
- Ensure Domain Controller patch level requirements are met
- Ensure AES256_HMAC_SHA1 is enabled [not optional]
- Configure Active Directory and Azure to support Azure AD Kerberos
- Additional steps to support administrative accounts.
- By default, these accounts can’t use security keys
Known Issues
- We recommend making yourself aware of known issues and FAQs
- The most impactful is “Signing in or unlocking a Windows 10 device with a security key containing multiple Microsoft Entra accounts”
Setting Up the Entra/Azure AD Tenant
Register Application
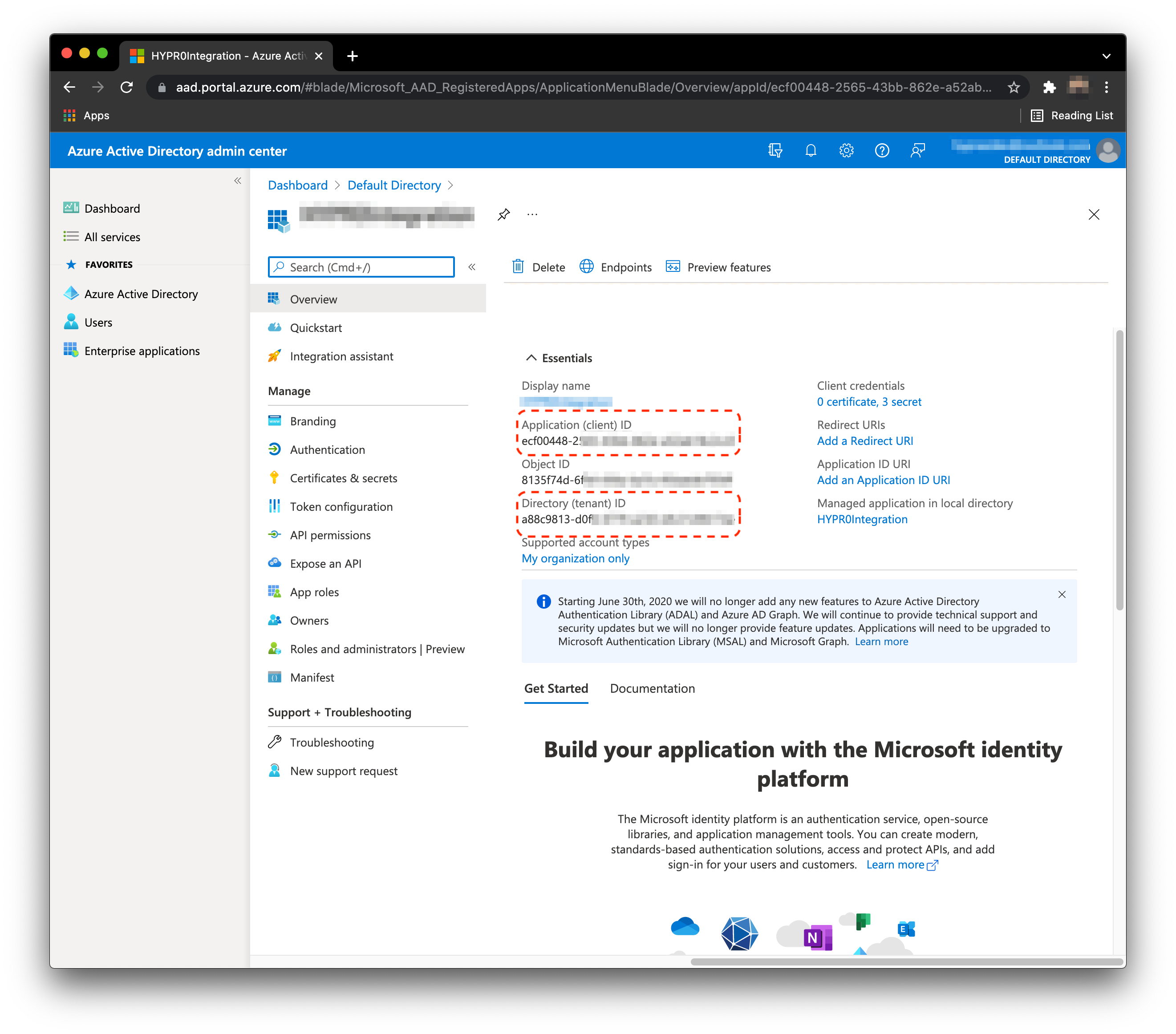
- From the Home screen, select Azure Active Directory > App registrations > New registration.
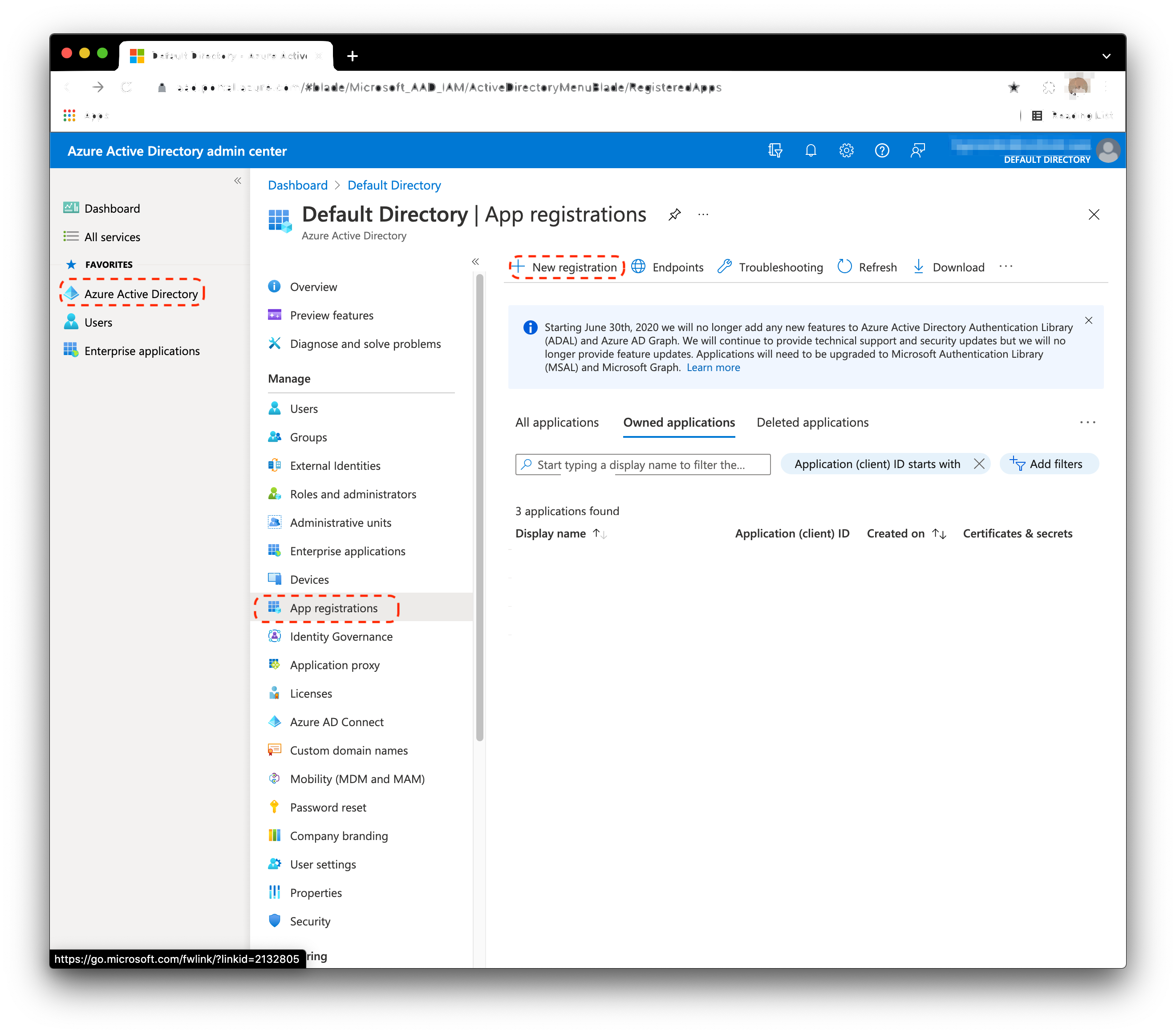
- Enter the application name: HYPRAuthApp.
Select Accounts in this organizational directory only.
Click Register when done.
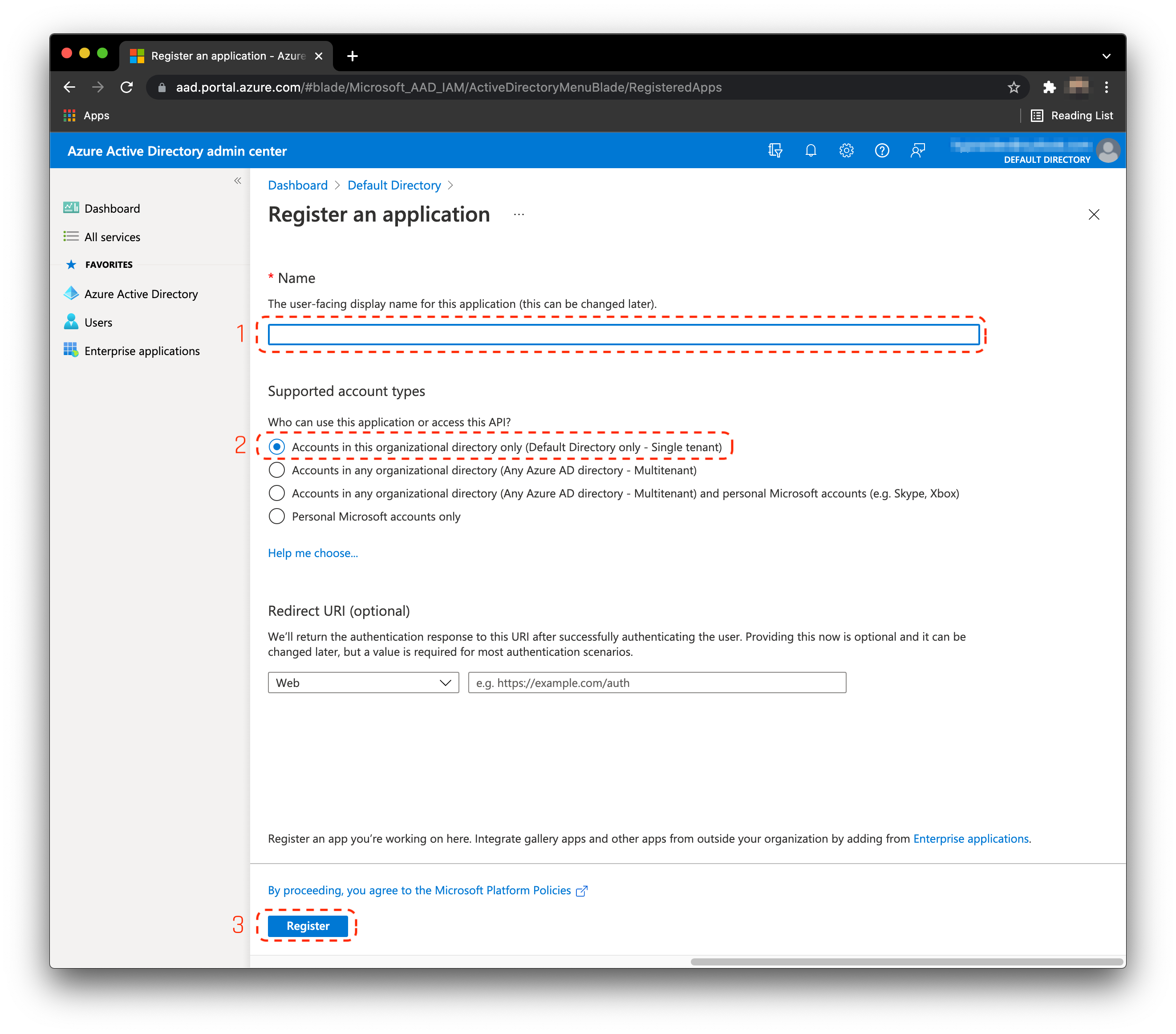
- Save the
clientIdandtenantId. You will need these later for PowerShell and HYPR's UX configuration.
Grant Application Required API Permissions
- From the home screen, select App registrations and select the app you just made.
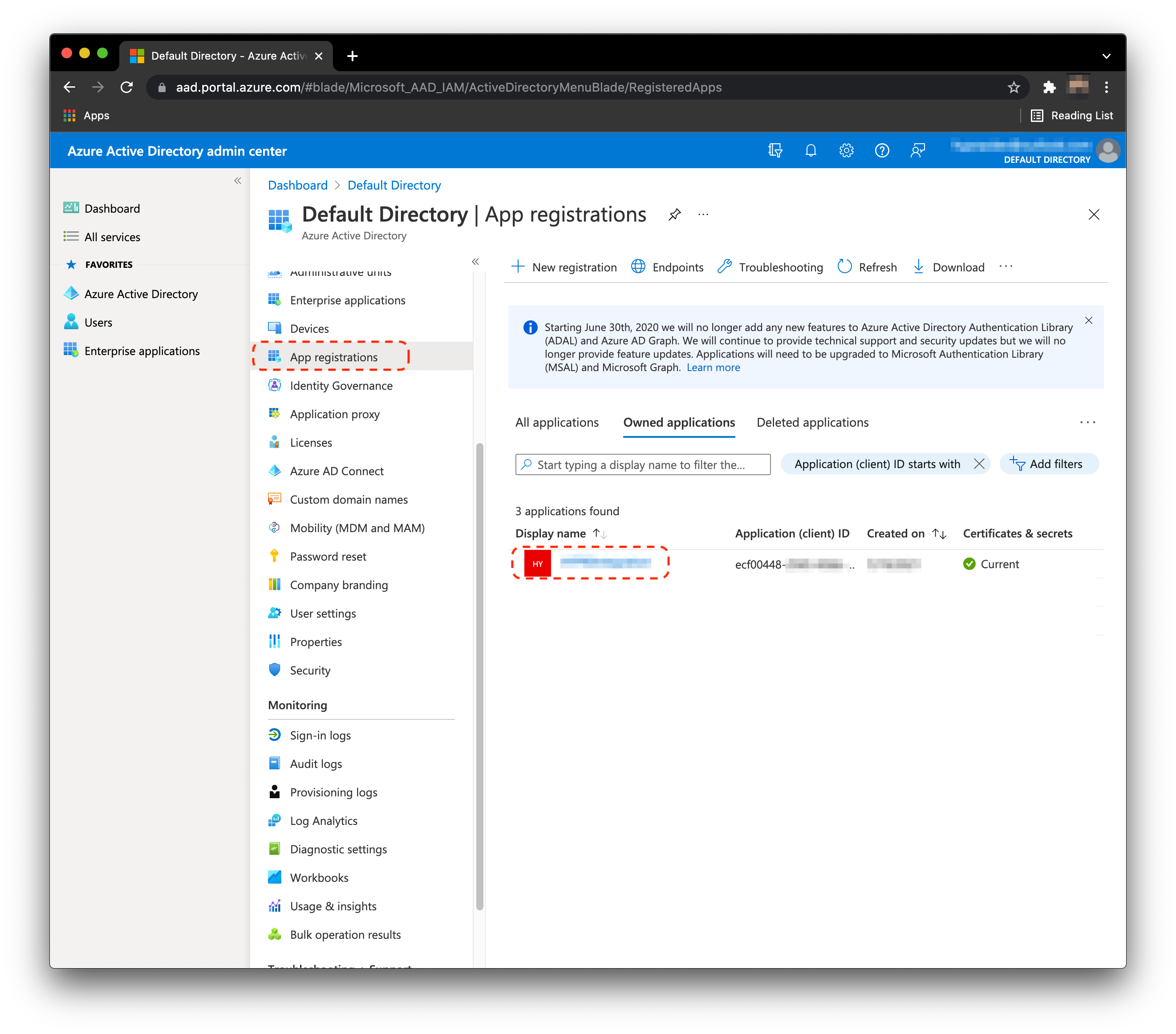
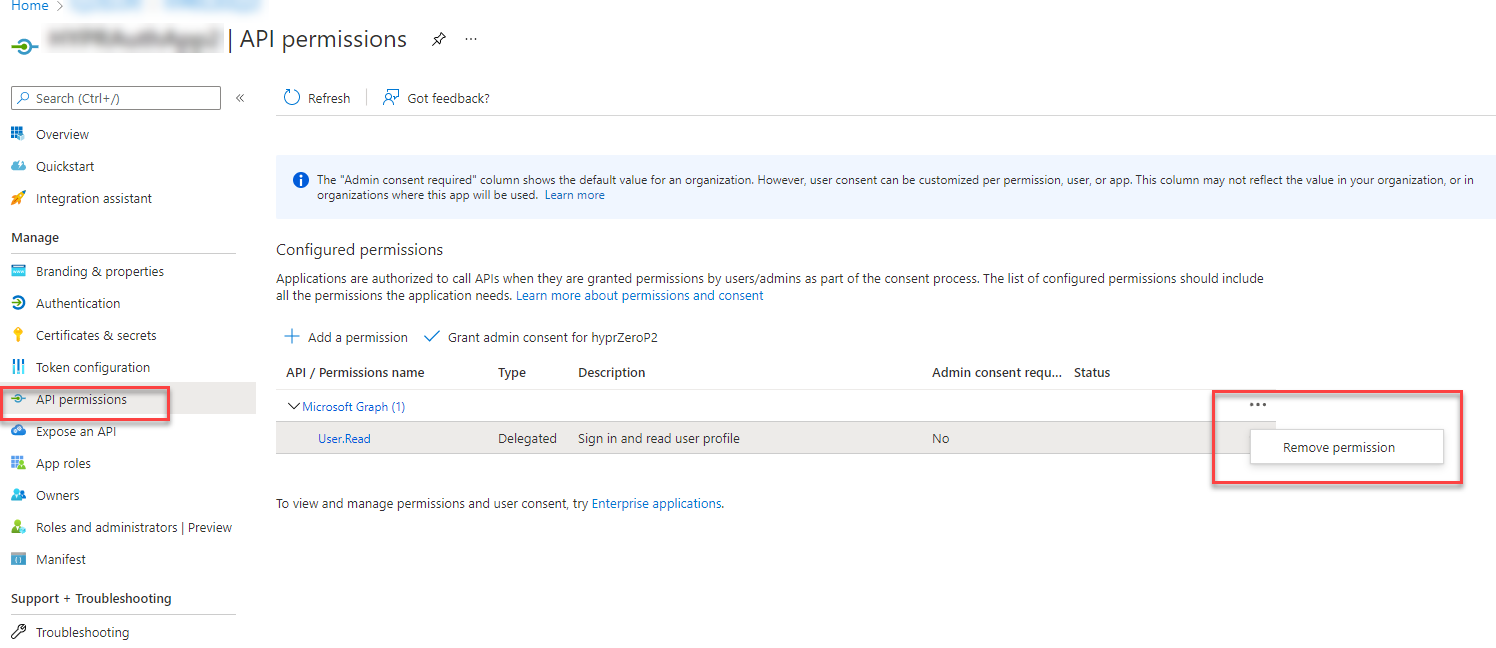
- While that app is selected, click API permissions. You will see that by default this application already has Microsoft Graph’s
User.Read. This is not required, so remove it by clicking ... next to the entitlement and selecting Remove Permission. Click Yes during the confirmation prompt.
- Select API permissions, then Add a permission.
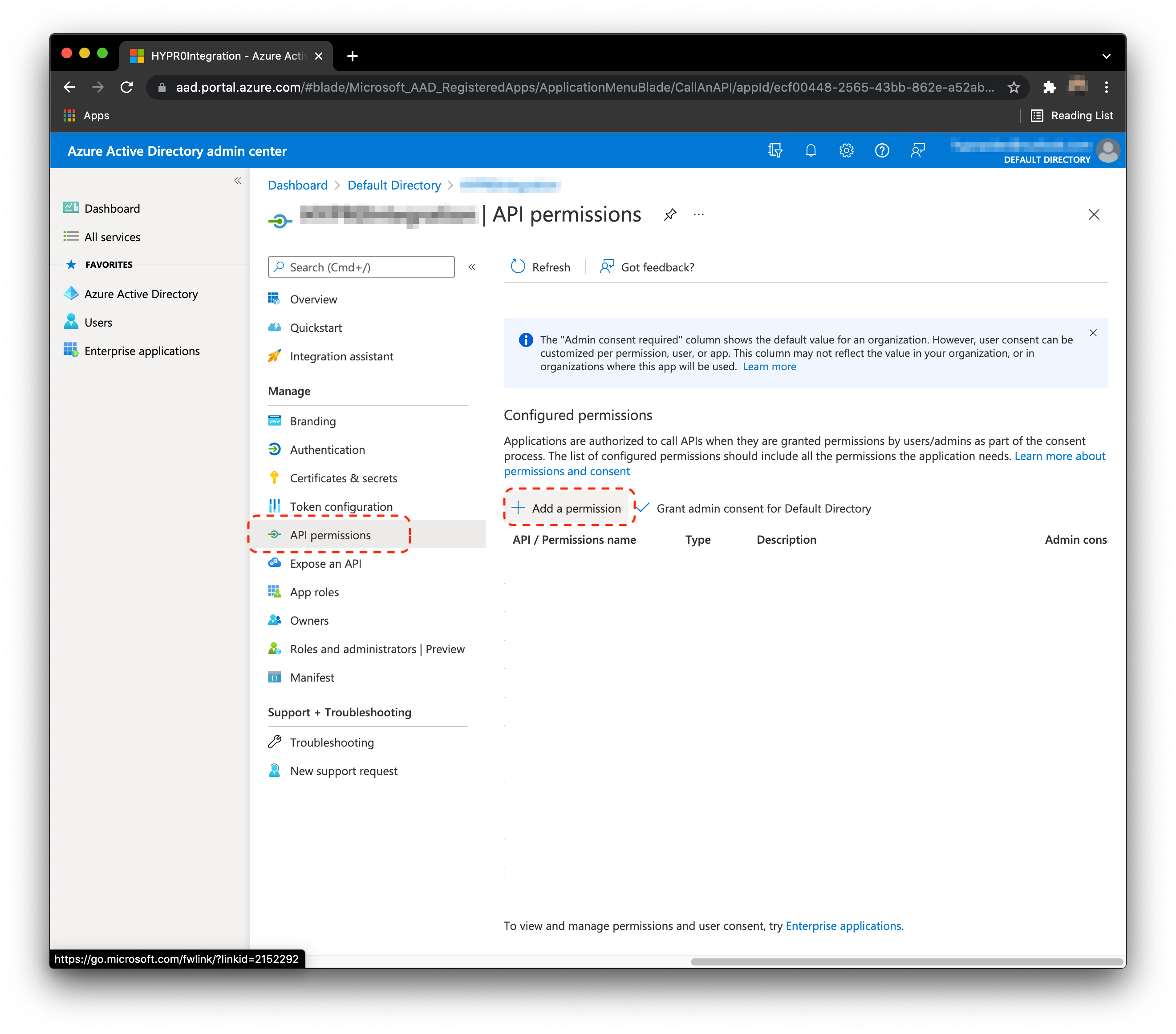
- Select Microsoft Graph.
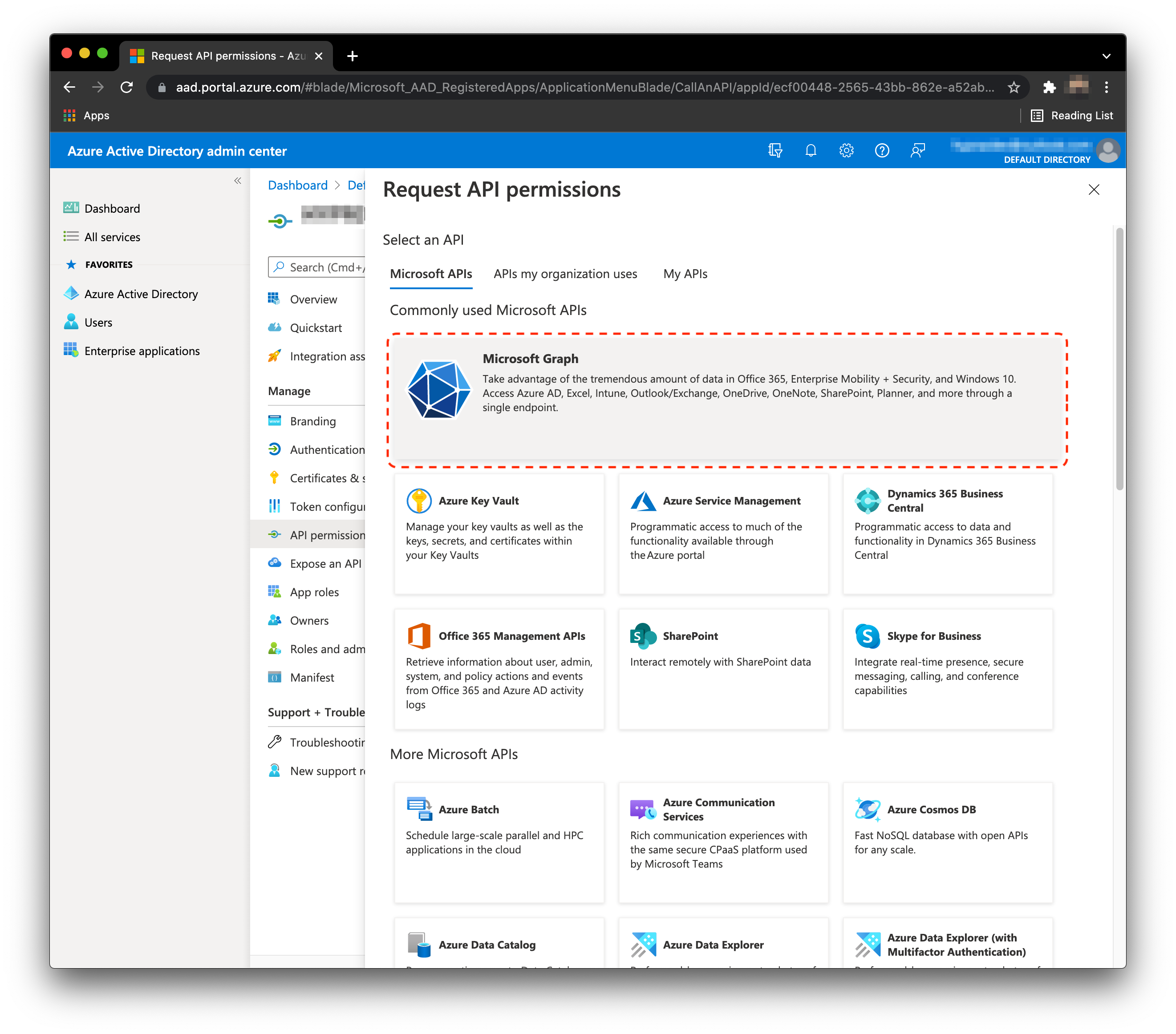
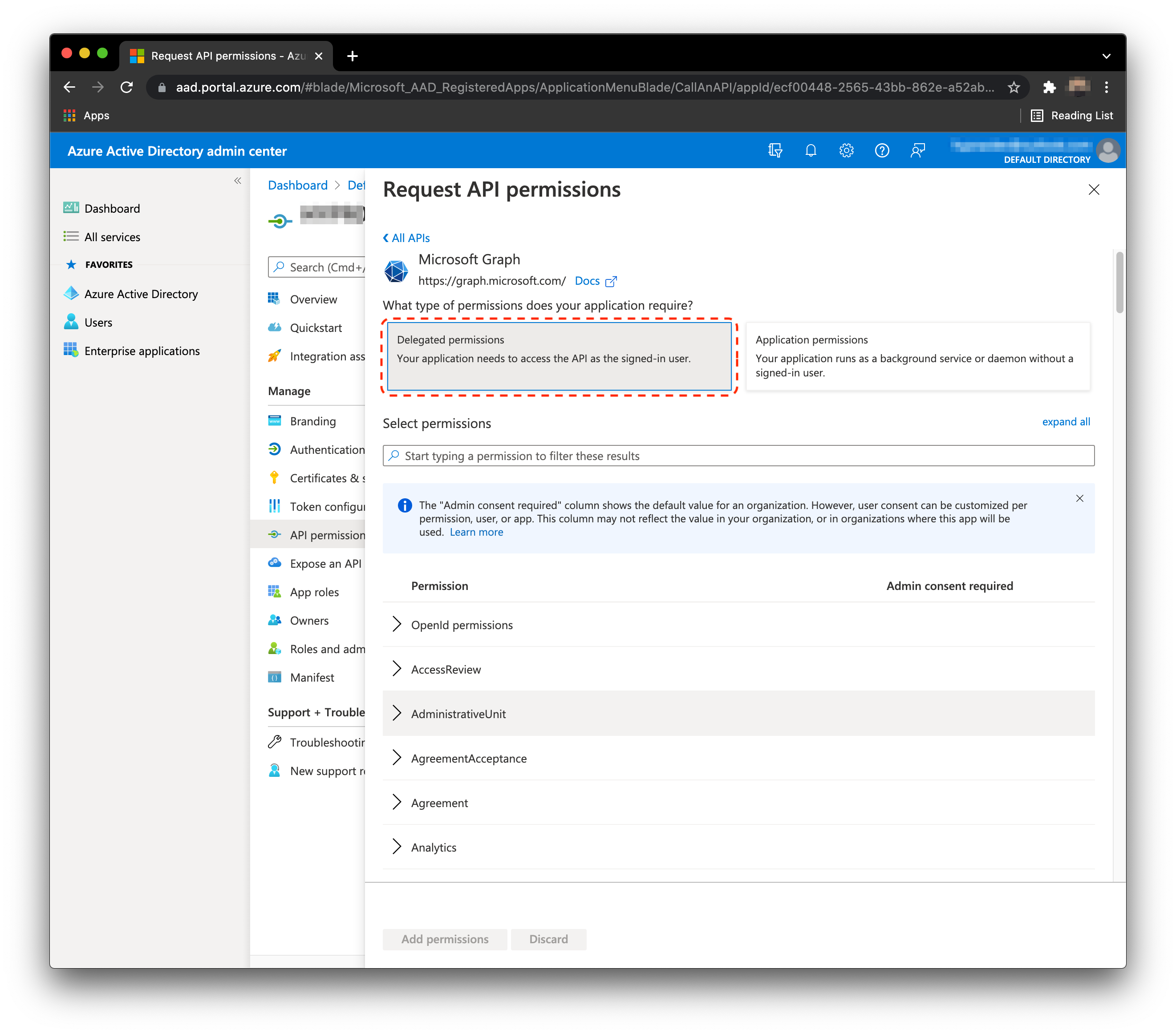
- Select Delegated permissions.
Delegated by Default
Sometimes Entra/Azure will not display the option for Delegated or Application permissions, and will immediately assume Delegated as the choice. As no Application permissions are required, this works in your favor. However, after you grant Admin Consent later in the process, you will be able to confirm/see which type of permission they are.
- Add the permissions Directory.AccessAsUser.All and UserAuthenticationMethod.ReadWrite.All.
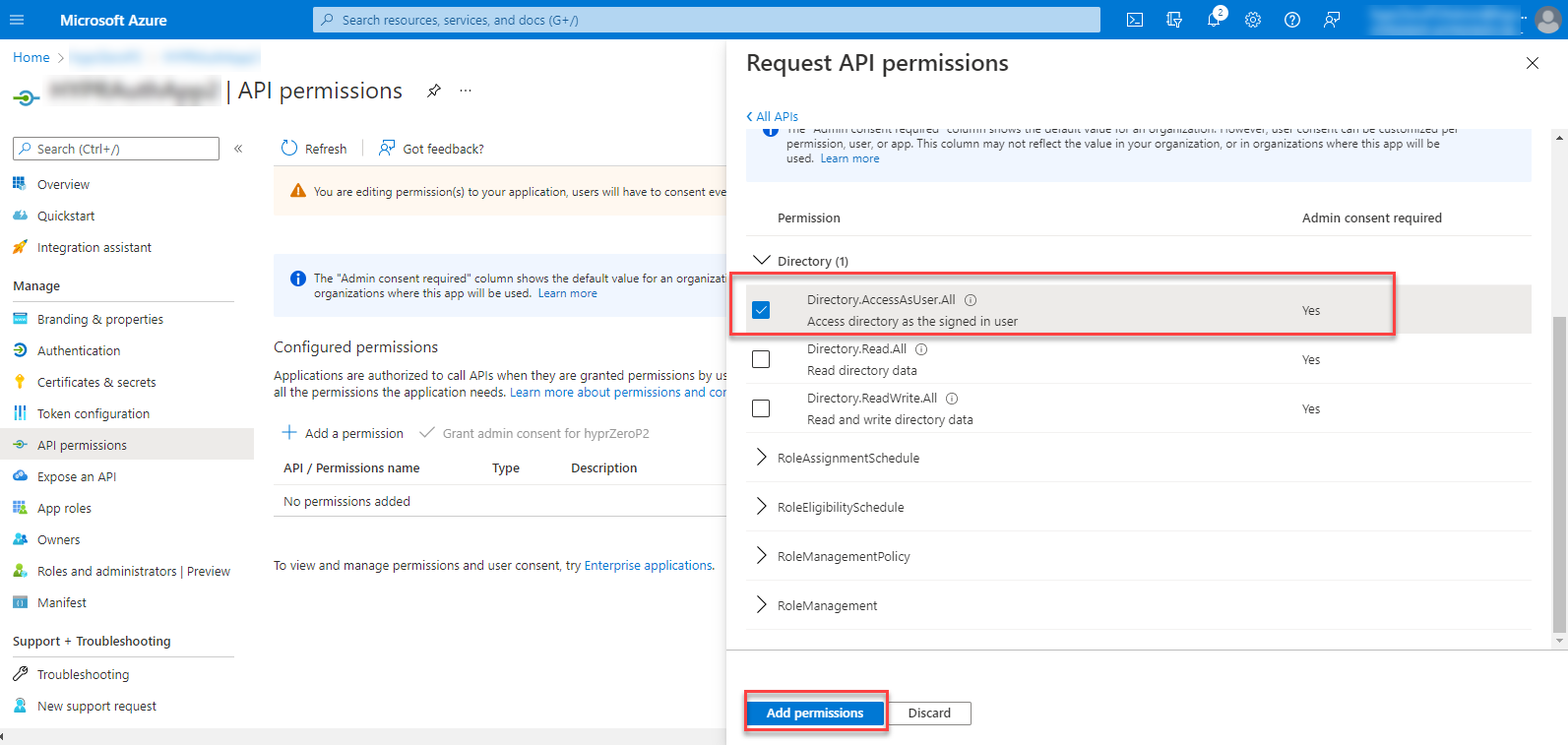
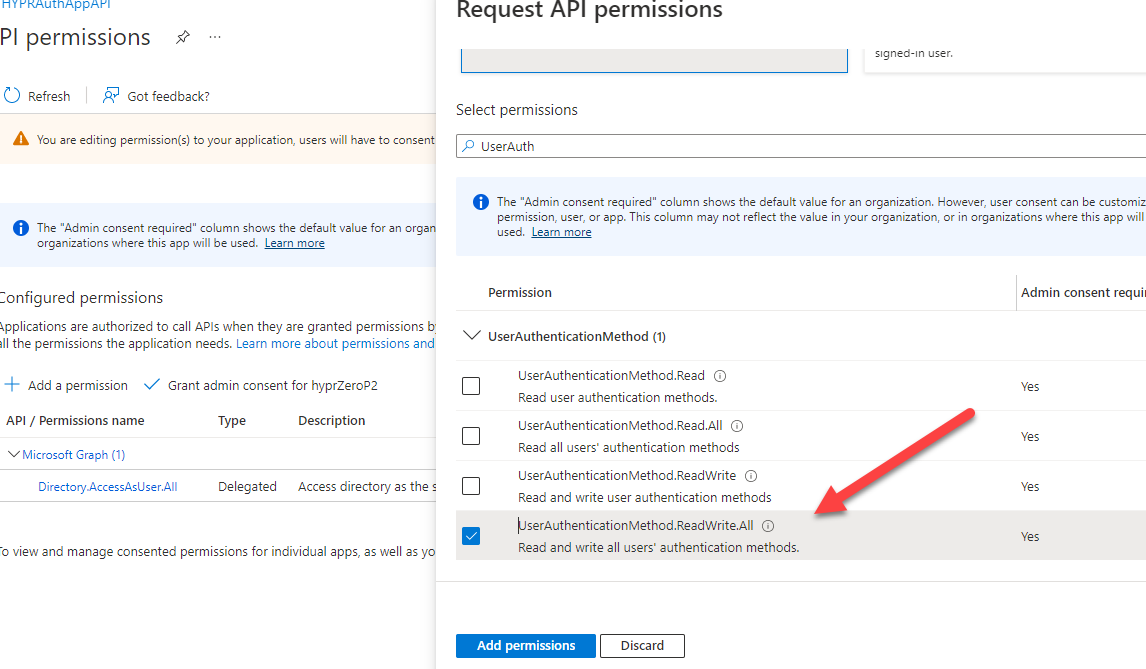
- Click Add Permissions when done.
- You must now Grant admin consent for the permissions to take effect.
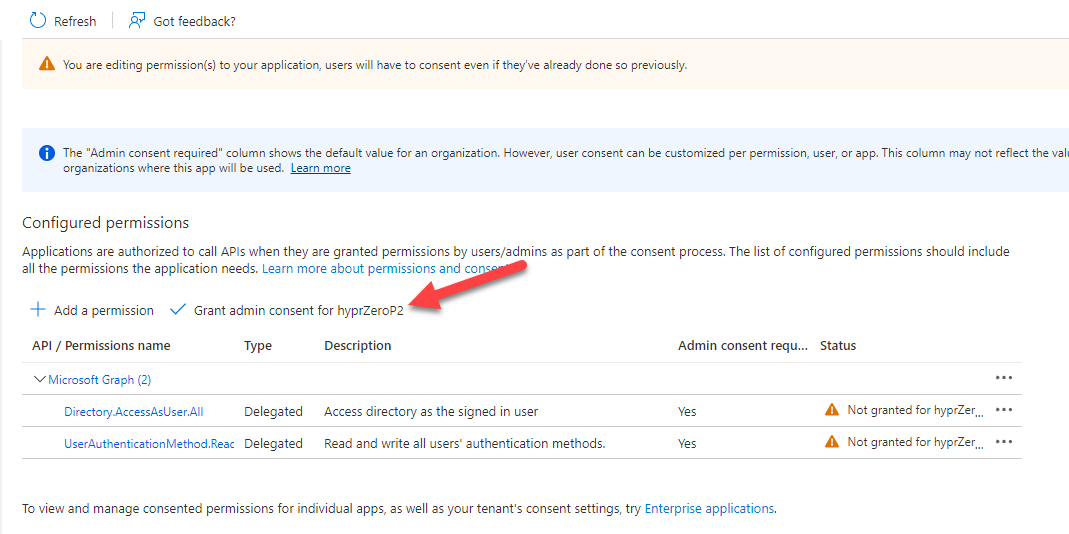
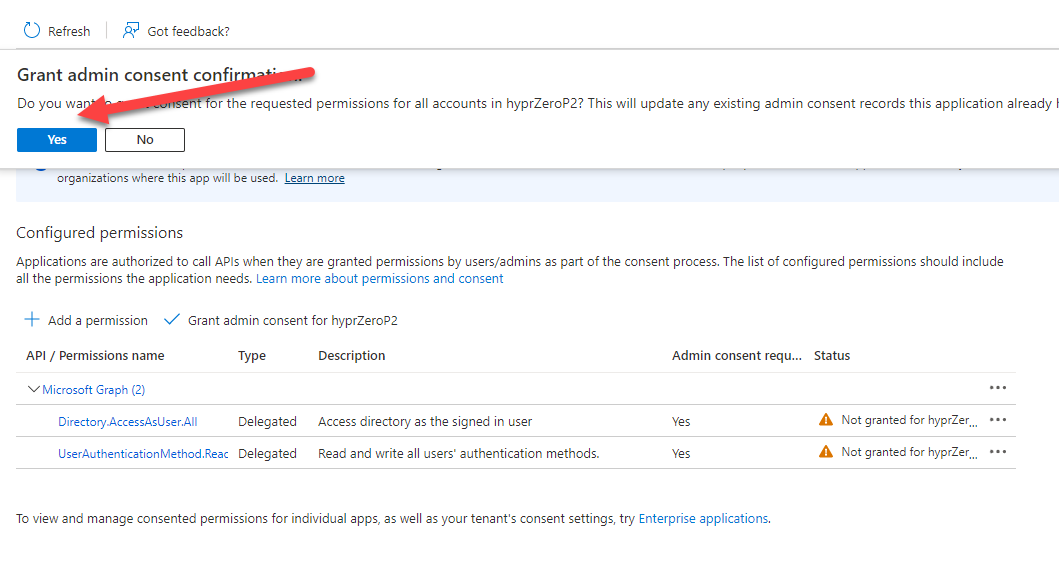
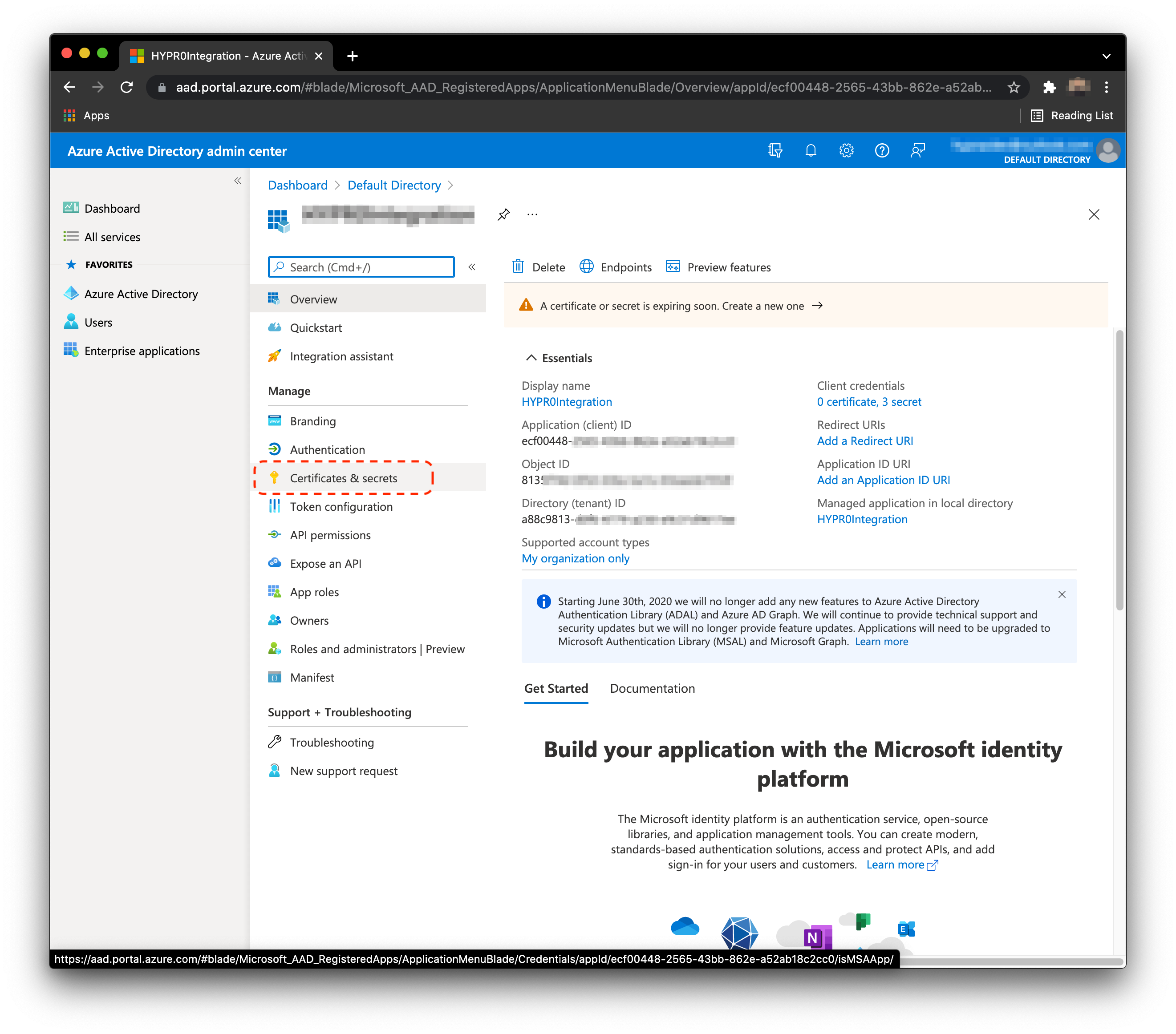
Create Client Secret
- In the Application menu, select Certificates & secrets.
- Click New client secret.
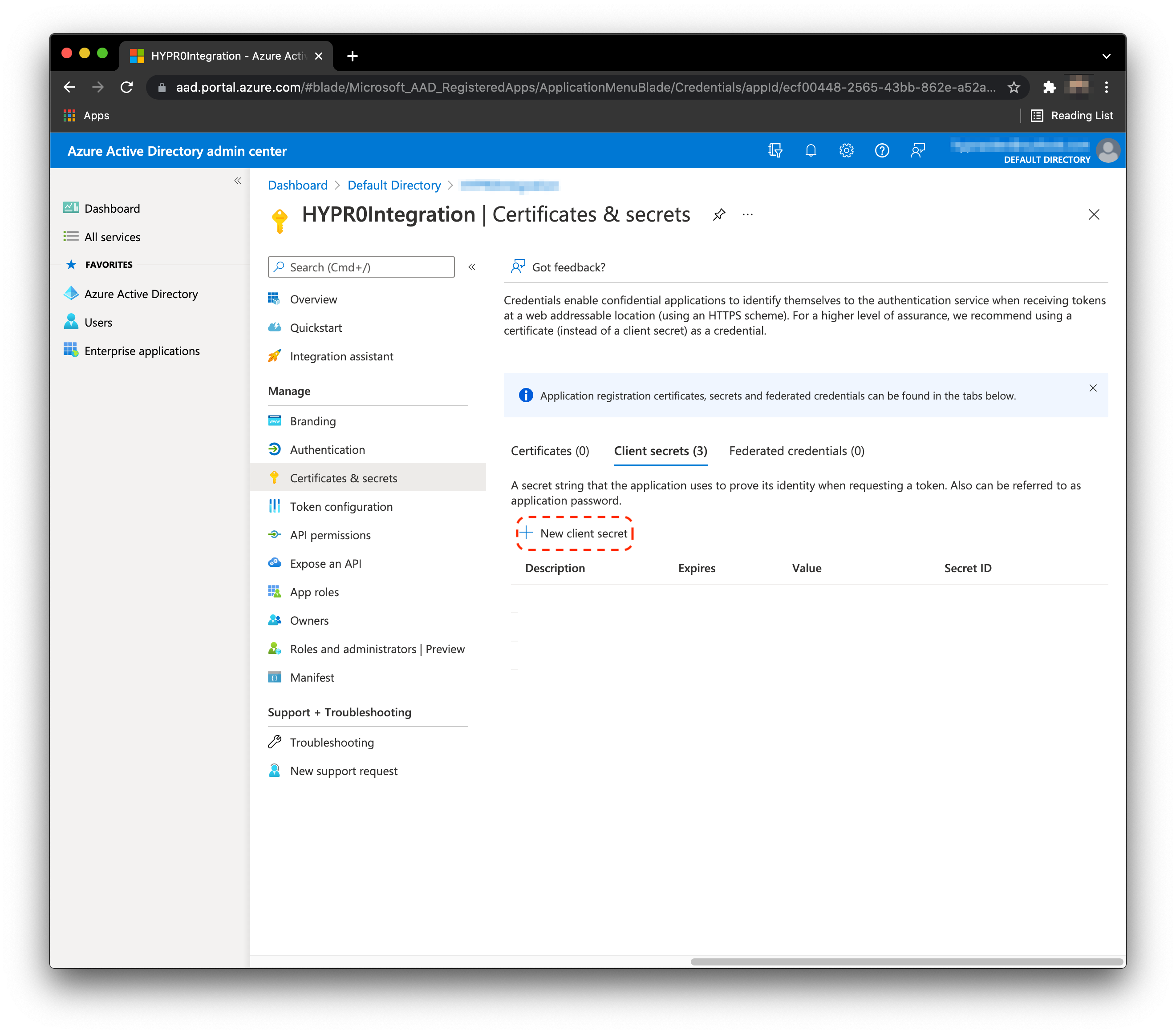
- Enter a Description and an Expires date. Click Add when finished.
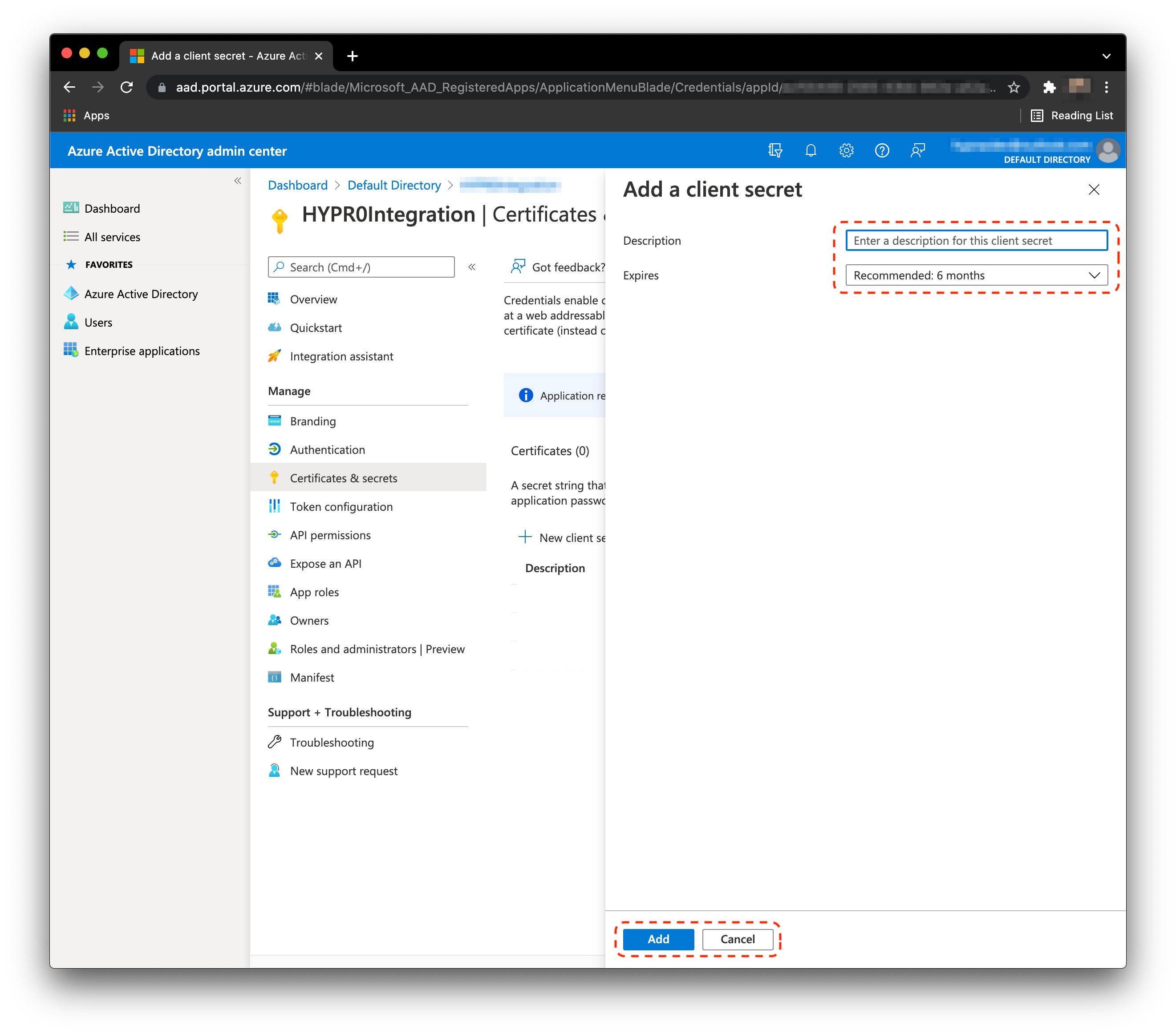
- HYPR will require the value of the secret during the integration flow. Save the value of the secret during this step, as it is not visible after. See the image below for an example.
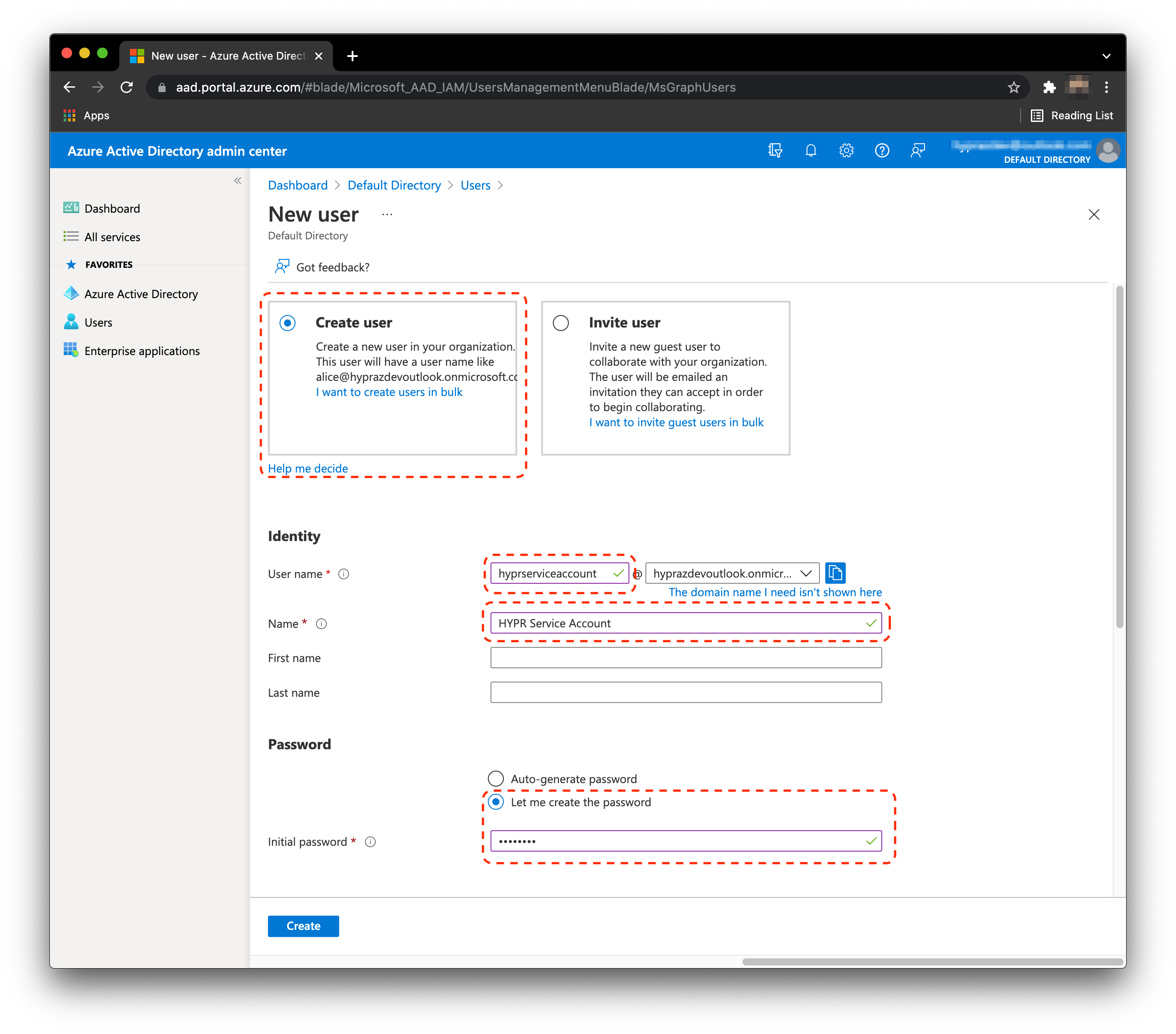
Create Service Account
- From the Home page, Click Azure Active Directory, then Users.
- Click New user.
-
Click Create user.
-
In the User name area, type hyprserviceaccount.
-
In the Name area, type HYPR Service Account.
-
Click Let me create the password, then set and save the password.
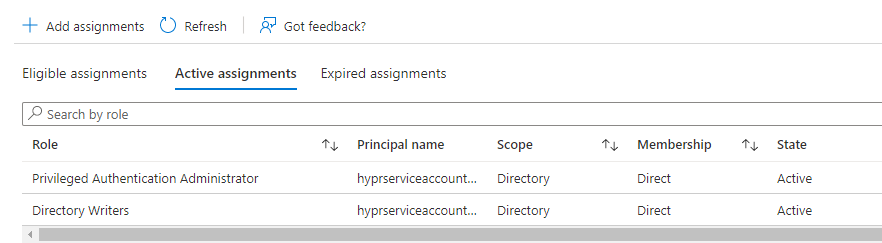
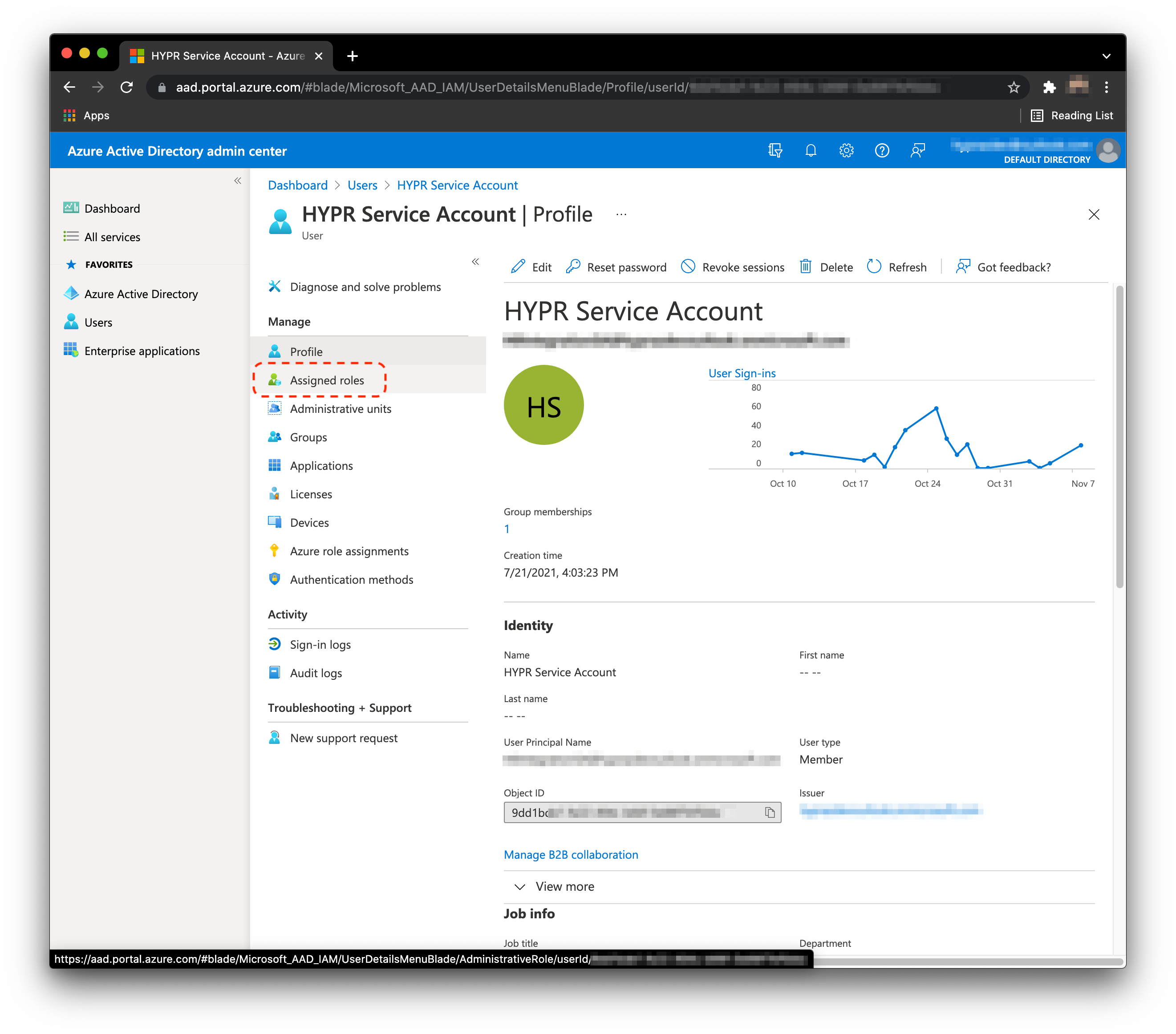
- Next we must assign roles to the service account. Click Assigned roles.
-
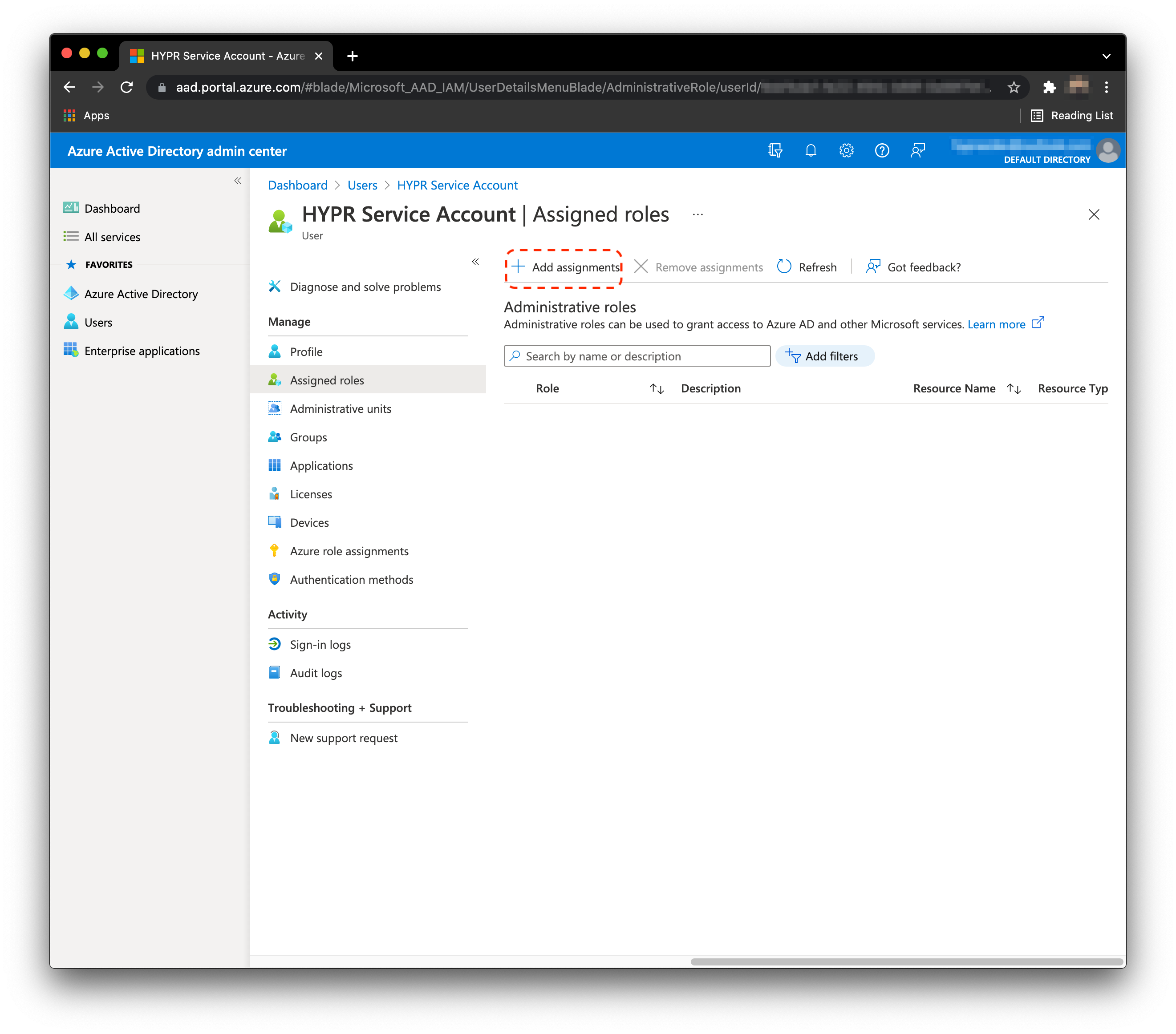
Click Add Assignments.
-
Search for and add the following roles:
- Directory Writers
Allows the necessary group creation/update and also handles getting the user data for syncing entries to HYPR; needed throughout the entire lifecycle of the HYPR-Entra/Azure integration - Privileged Authentication Administrator
Allows HYPR to manage the HYPR Enterprise Passkey on Entra/Azure; will be able to delete it when removed via phone or CC, and to have accurate data on the HYPR User Management list in the event it is deleted directly in Entra/Azure
- Directory Writers
-
Click Add when done.
Expect the Unexpected
This is the area in which Entra/Azure is very slow to replicate the changes. The Entra/Azure administrator may need to refresh the page many times for all to show up. Sometimes, they may need to add it twice. This is expected behavior.
Service Account
At this time, the prospect must open up an incognito browser and log into
portal.azure.com, as this service account. This is required to set the permanent password of the account.
One Condition
If during this login, the account gets prompted for MFA, it means that a Conditional Access Policy must be updated to exclude the
hyprserviceaccount.
Enable Security Keys in the Entra/Azure Tenant
- Login to
portal.azure.comas a global admin account. - Navigate to Entra/Azure Active Directory > Security > Authentication methods. Click FIDO2 security key.
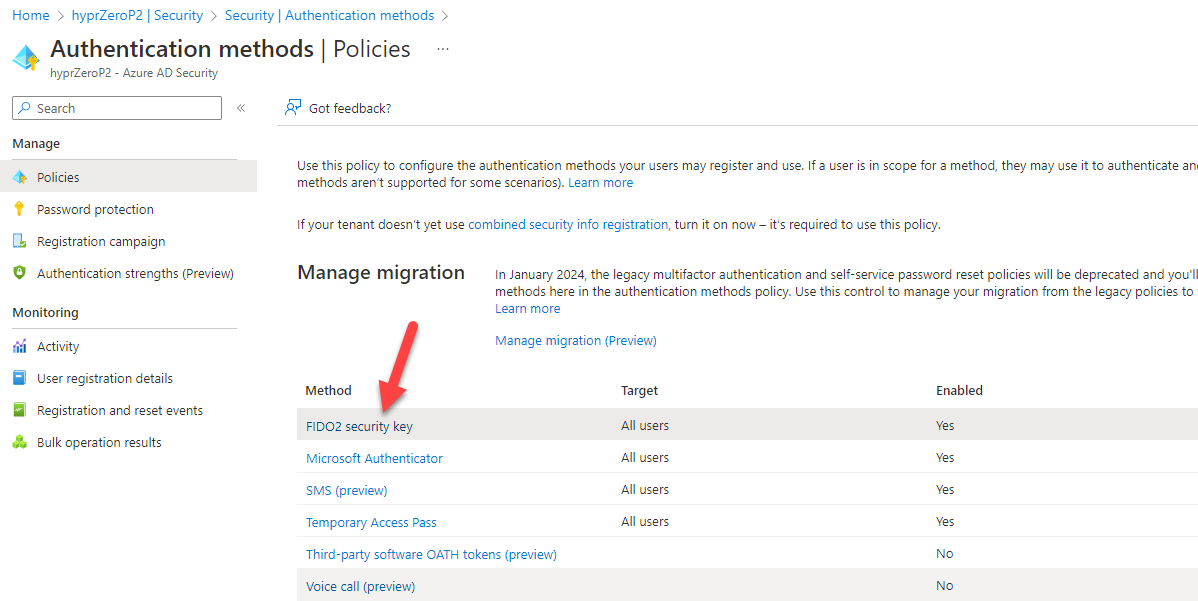
- Here you can enable security keys and define allowed users. Include All users and leave the registration as Optional.
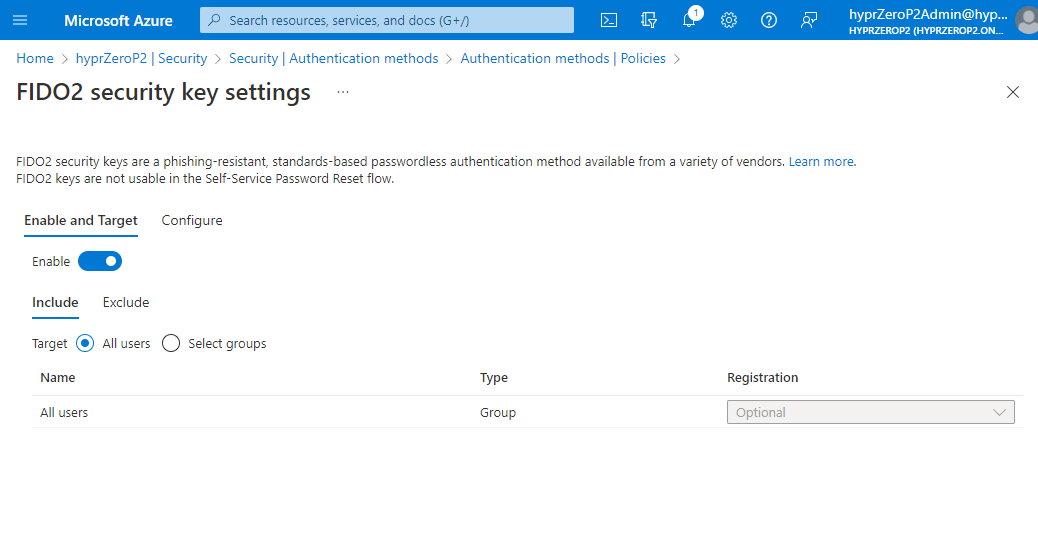
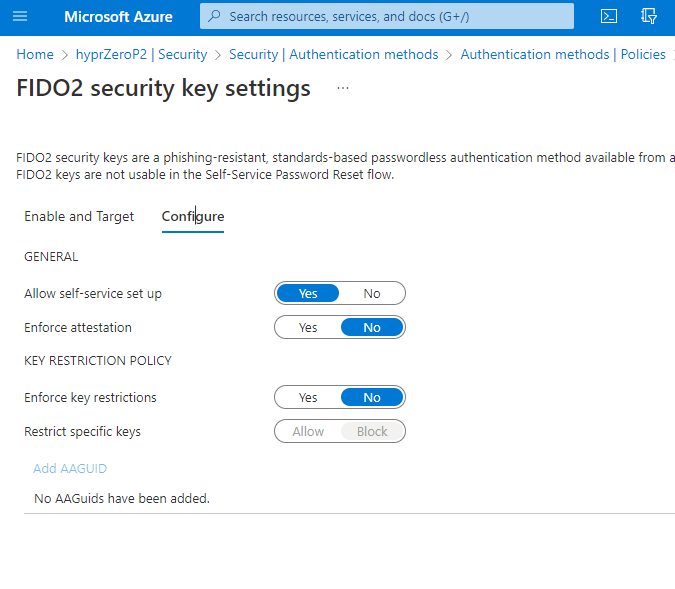
- On the Configure tab, make sure the settings are as depicted below. This is the only configuration we will support at this time.
Enforced Attestation
Microsoft uses the Enforce attestation feature to ensure the FIDO2 authenticator is certified by the FIDO Alliance and approved by Microsoft's team. HYPR's AAGUID was added as an approved FIDO2 Authenticator on March 2023. HYPR supports this setting as either True or False.
Enable Security Keys in Intune
Once security keys are enabled in Entra/Azure, you must set a policy in Intune (i.e., Endpoint Manger) which will allow for security key login on Windows OS. Follow Microsoft’s instructions on setting up Intune policies for security key-enabled logins.
Setting Up the HYPR Tenant
When up and running, make sure HYPR has enabled the necessary features to support HYPR Enterprise Passkeys.
To install a new Enterprise Passkeys integration in Control Center:
-
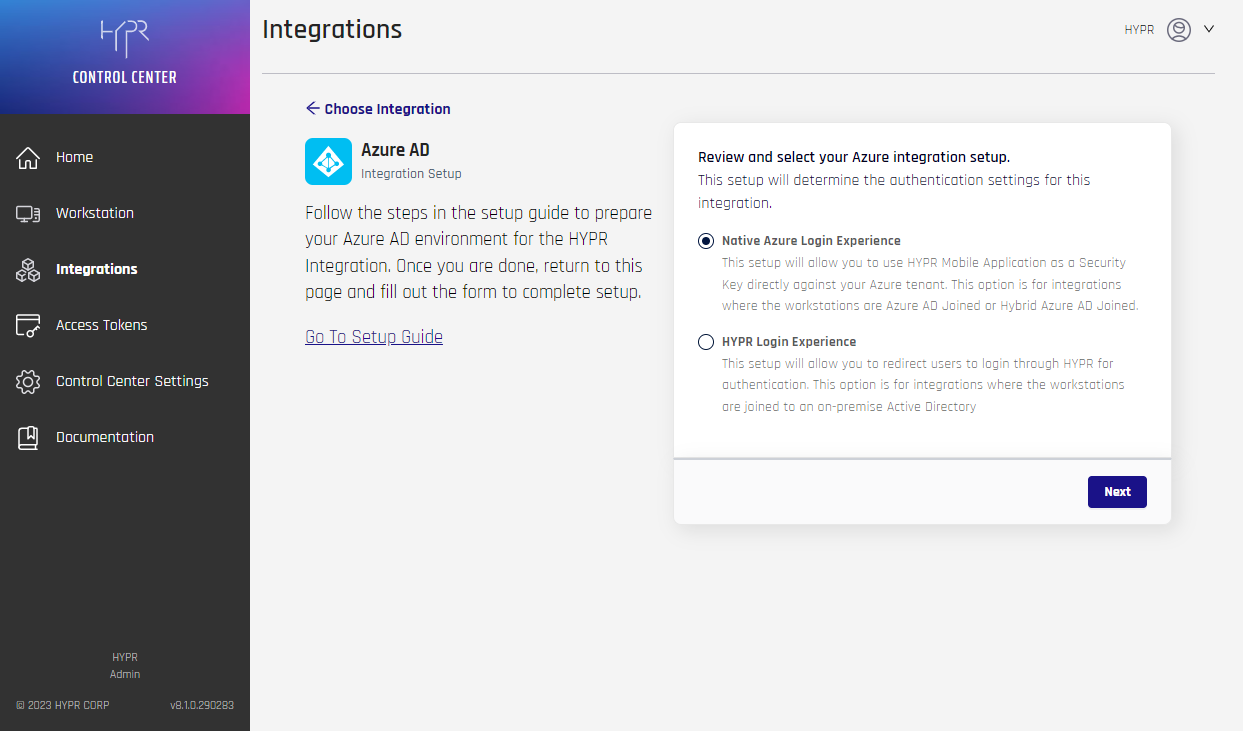
On a new tenant, navigate to Integrations > Add New Integrations > Azure AD.
-
You will be prompted to select your login experience. For the FIDO2 Mobile Authenticator, select Native Azure Login Experience, and click Next.
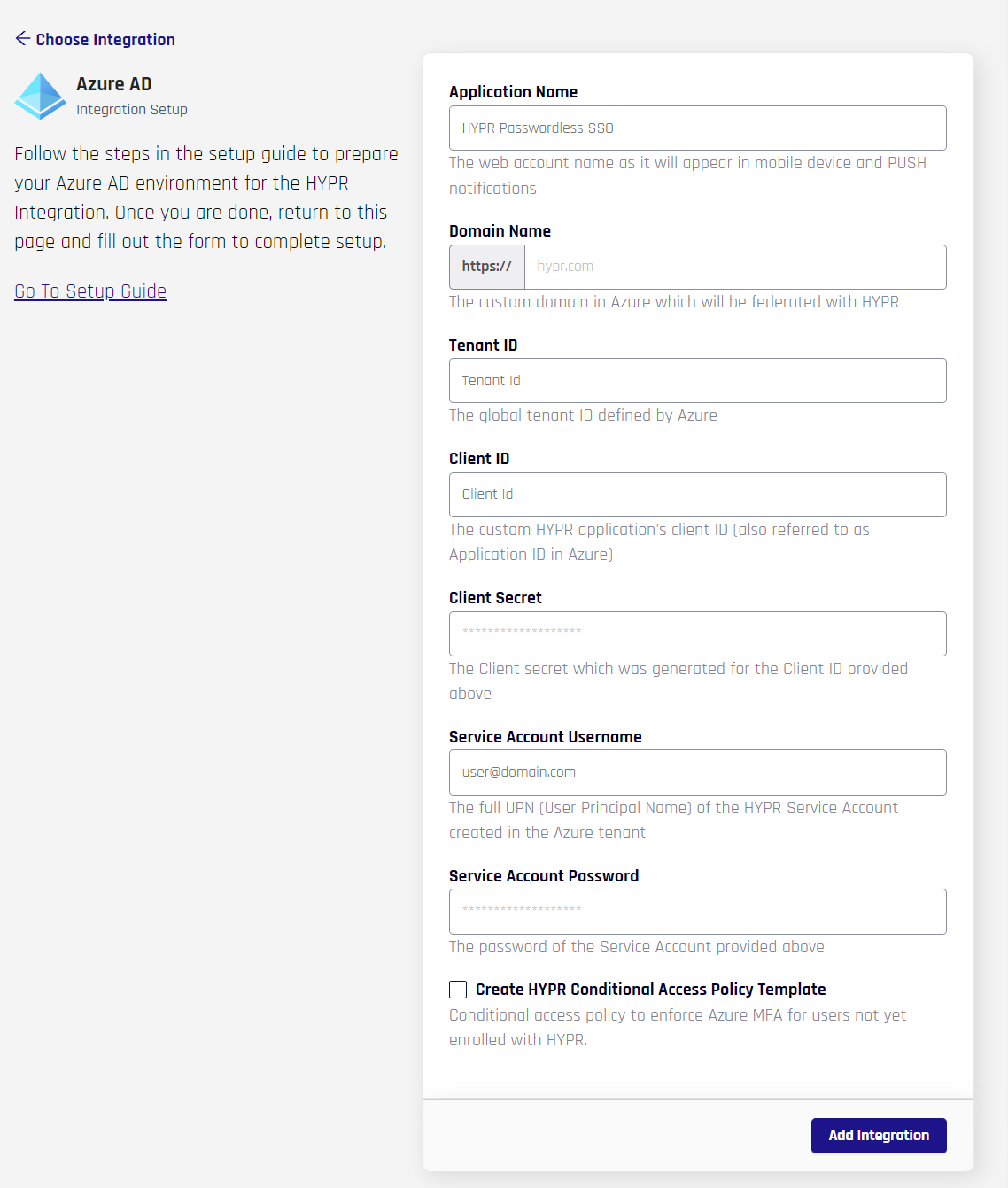
- You are presented a form which contains the HYPR Application Name and all of the Entra/Azure-related data needed for HYPR to connect to the Entra/Azure tenant. These are the items created/captured above; complete the fields as follows:
- Application Name: Only alphanumeric, spaces, dash, underscores, or trailing
-or_are allowed; this is the same validation rule for all HYPR RP Application names (rpAppId); the namespace is limited to 23 characters - Domain Name: The Azure/Entra domain name to be federated with HYPR
- Client ID: The ID of the client/application in Entra/Azure AD
- Tenant ID: The ID of the tenant
- Client Secret: The secret associated with the client/application
- Service Account Username: The user account with permissions which allow API calls
- Service Account Password: The Service Account password
When you are finished, click Add Integration; if Add Integration is successful, it confirms all of the parameters provided were validated and HYPR can now connect to Entra/Azure - Create HYPR Conditional Access Policy Template: If checked, HYPR creates a policy template enforcing Entra MFA when affected users are not already enrolled with HYPR
- Application Name: Only alphanumeric, spaces, dash, underscores, or trailing
- You will be presented a popup box. Click Maybe Later.
HYPR Groups in Entra/AzureAD
When a new Enterprise Passkey integration is successfully created, HYPR automatically creates three groups in Entra/AzureAD. You do not need to take any action to maintain these, but may wish to apply policies specific to the HYPR Enterprise Passkey. They correspond to the different phases of pairing an Enterprise Passkey:
- HYPR Group (Eligible for Pairing) - Users who have only been invited
- HYPR Group (Client Paired with HYPR) - Users paired with HYPR authentication (but not Entra/Azure)
- HYPR Group (Client Paired with Azure) - Users with Enterprise Passkey authentication
-
With a new application in HYPR, you must make sure HYPR has enabled the necessary features; contact HYPR Support if you have not done so already to ensure full functionality.
-
CC takes you to the Integration User Management page.
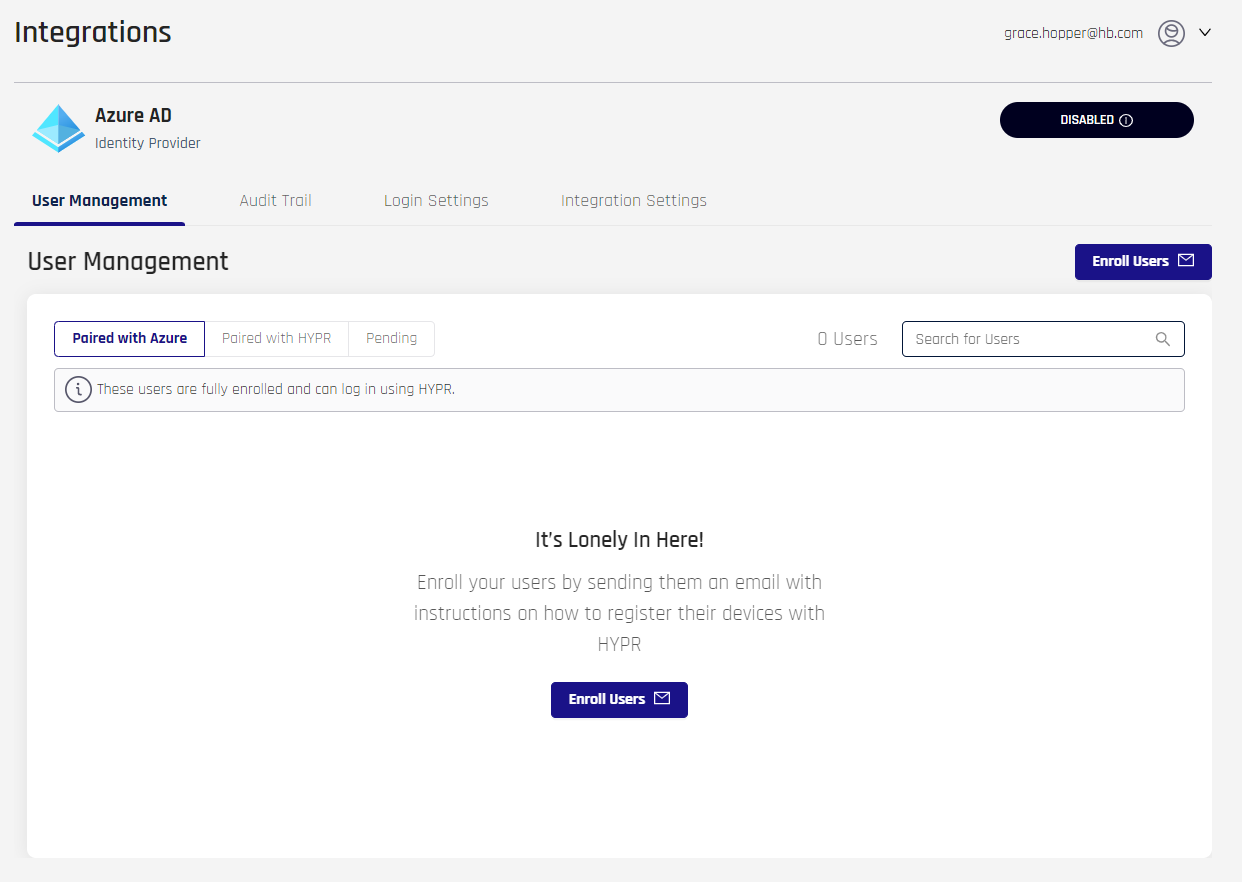
- Select the Integrations Settings tab. You will see a brief description of the Native Azure Login Experience. Note it is DISABLED. When DISABLED, the expectation is the end-user can pair with HYPR using a QR code, but cannot register or authenticate to Entra/Azure.
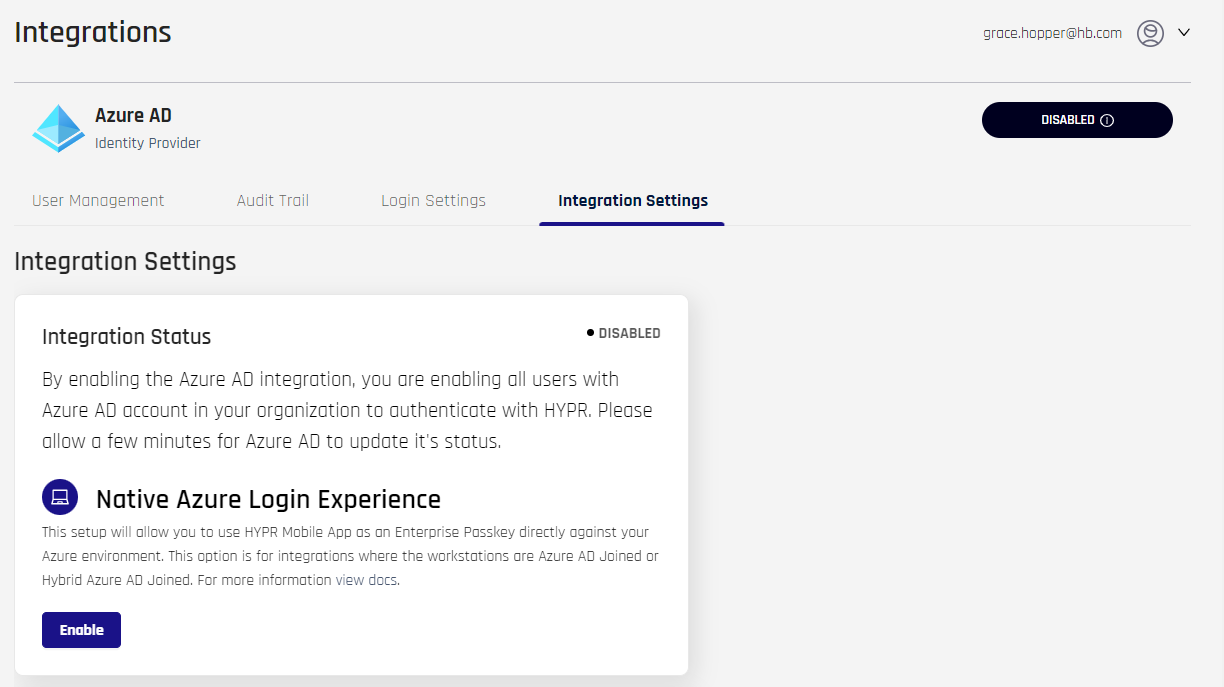
- Click Enable and a confirmation appears.
- Let the confetti fly, then click Close.
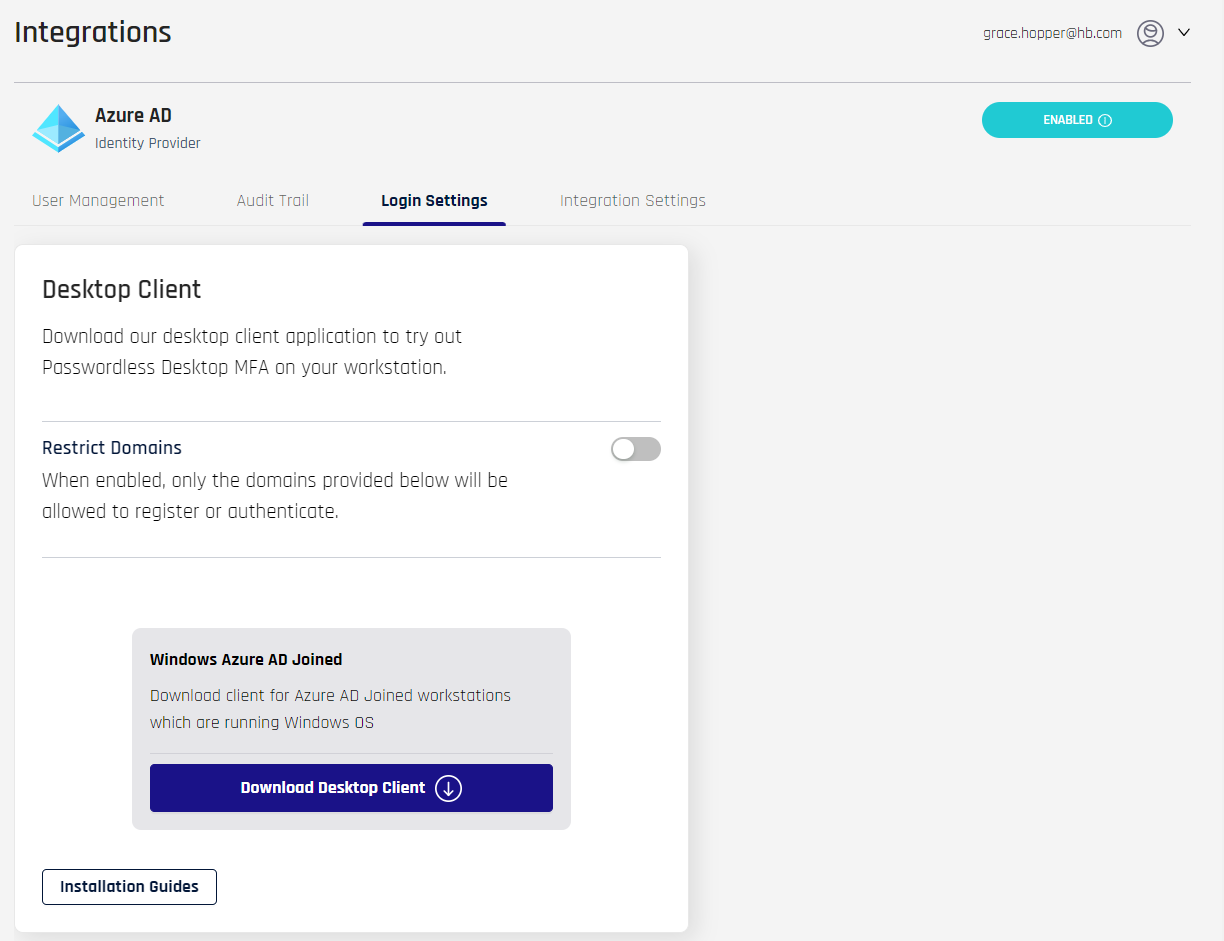
Configure and Download the Desktop Client
- Navigate to Login Settings. Here you can restrict domains and download the HYPR Passwordless client. Installation Guides and Access Control are currently being built.
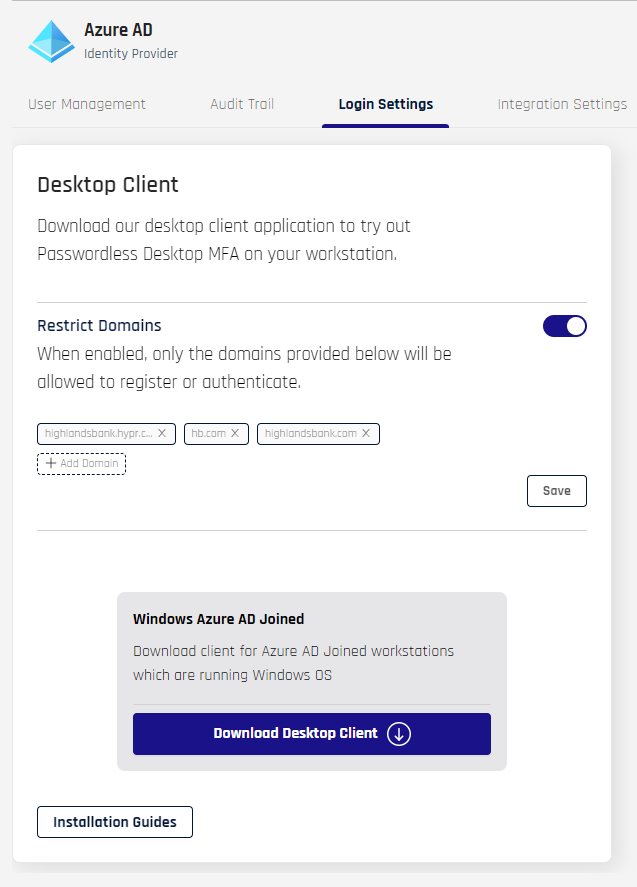
- To accept any domain name, leave the toggle off for Restrict Domains. To limit acceptable domains, toggle the switch to the On position. The dialog expands.
- Click +Add Domain and type the domain name (without
https://) in the resulting field. Press Tab or Enter to add another - To remove a domain from the list, click the x next to it
- Click Save when you are finished adding accepted domains; a confirmation message appears: "Restrict Domains saved successfully"
- Click +Add Domain and type the domain name (without
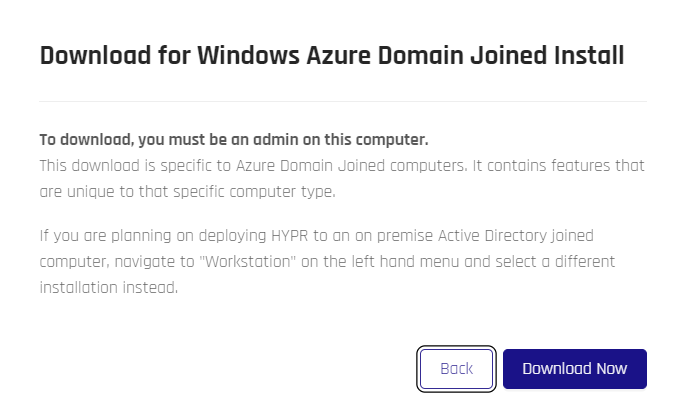
- Select Download Desktop Client and a confirmation popup displays.
- If you are unsure whether or not you should be downloading the HYPR Passwordless client in your environment, click Back and contact your support. Otherwise, click Download Now, and your browser will download a
.ziparchive containing the client installation file and ahypr.jsonfile.
- Unpack the archive. It contains two files:
hypr.json- JSON containing installation parametersWorkforceAccess-8.3.0_x64.msi- Microsoft installation file
- Install the HYPR Passwordless client on an Entra/Azure domain-joined workstation by double-clicking
WorkforceAccess-8.3.0_x64.msi. Complete the instructions in Installing on Windows.
Pairing a HYPR Enterprise Passkey
Pairing a workstation to a HYPR Enterprise Passkey will add the user to an Entra/Azure group (HYPR Group (Client Paired with HYPR)) that indicates they still need to pair their passkeys with Entra/Azure. Administrators may wish to use this group for policy changes or email reminders to complete pairing. To help users through the Azure pairing afterward, notifications will show up in the HYPR Mobile App and HYPR Passwordless Device Manager screens with instructions and links.
Take Only One
The HYPR Mobile App supports only one Entra/Azure passkey credential per device. You may still register other FIDO2 passkeys to the account; just not another Entra/Azure Passkey.
Roaming on Wireless
HYPR Enterprise Passkey supports roaming logins via Wi-Fi on domain-joined workstations. Enable roaming logins for the integration's Control Center RP Application by selecting the RP application in Control Center Advanced Mode, then toggling it On in the Workstation Settings pane.
Helpful Cues
When pairing with a FIDO-enabled Azure pairing, HYPR Mobile App offers a banner link to this article if users need instructions to continue. It appears only once and can be cleared; it goes away after pairing is completed. This banner also shows at the bottom of the HYPR Mobile App Security Keys page, and will always be there for those who want more information.
When pairing an Azure domain-joined account, for partially paired accounts HYPR will display a warning icon to remind users they have steps yet to complete before pairing is done.
Pairing with HYPR on a Domain-joined Workstation
Do This First
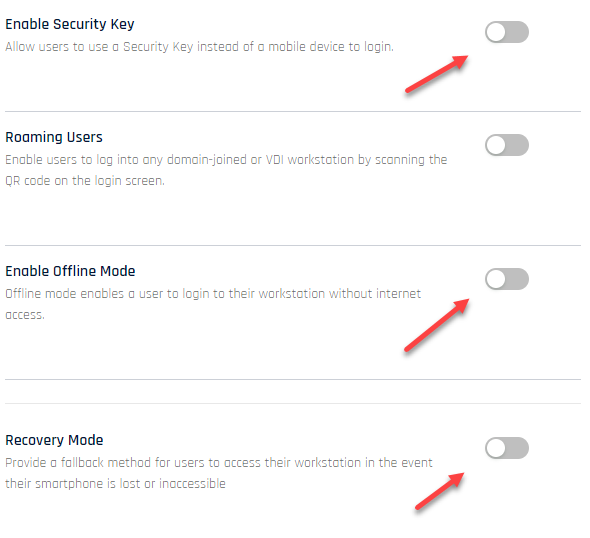
Change the CC UX to Advanced and navigate to the rpApp you created, then Workstation Settings. Disable the following:
- Enable Security Key
- Enable Offline Mode
- Recovery Mode
You will not need these settings. If they remain in their default state, you will see a security key option when you pair with HYPR (which will not work) and the Audit trail will report failures regarding the other two settings. Make sure to Save at the bottom of the page before continuing.
- Login to Windows as an Entra/Azure cloud-only or hybrid account (i.e.,
carol.shaw@highlands_azure.com). - Launch the HYPR Passwordless client.
- Click Start Pairing.
- The HYPR Passwordless client reminds you to open Microsoft Azure AD and pair your phone as a security key after pairing with HYPR. Click Continue.
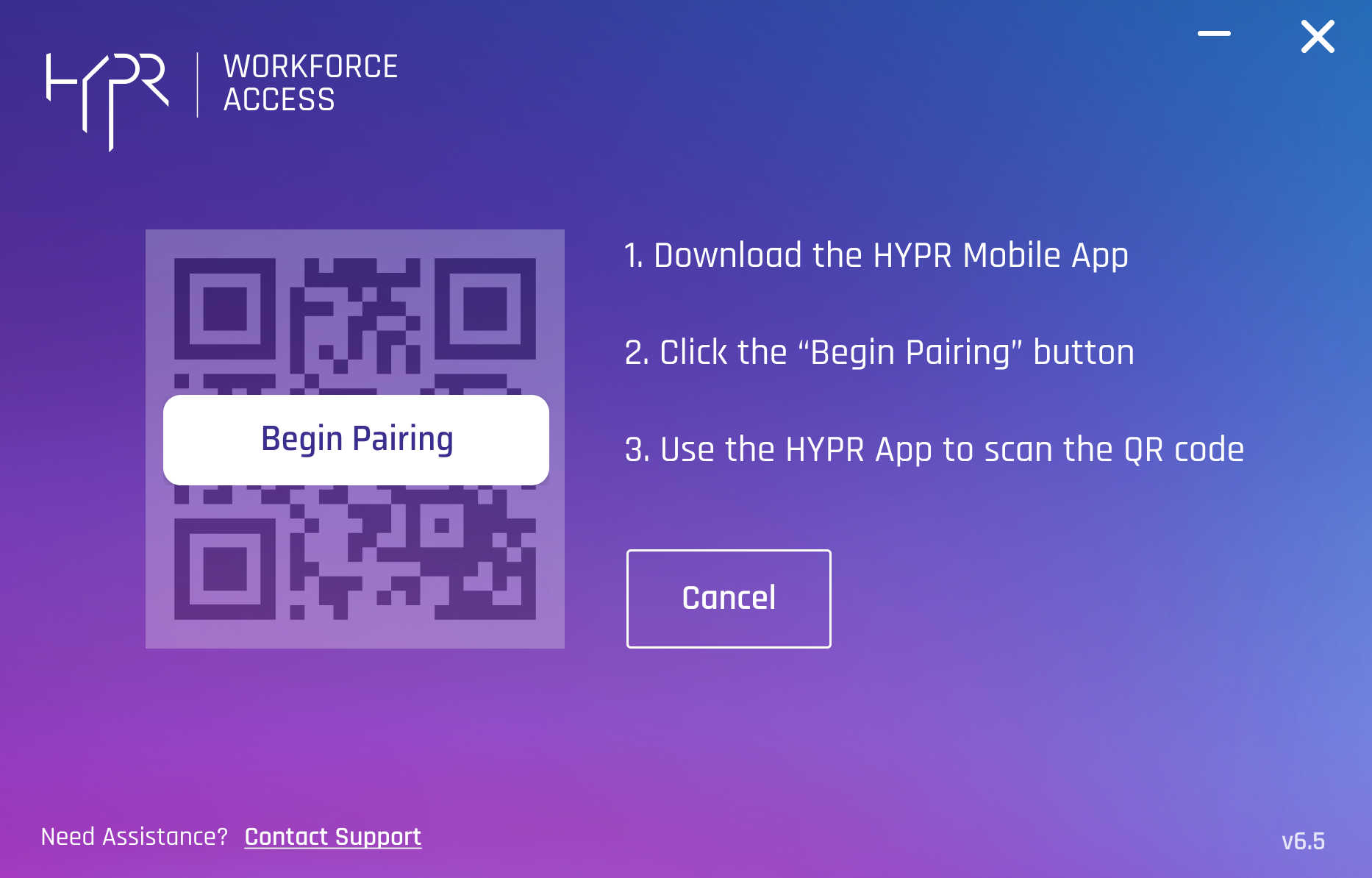
- The HYPR Passwordless client presents a QR code. Using a device with the HYPR Mobile App installed and ready to scan a QR code, click Begin Pairing.
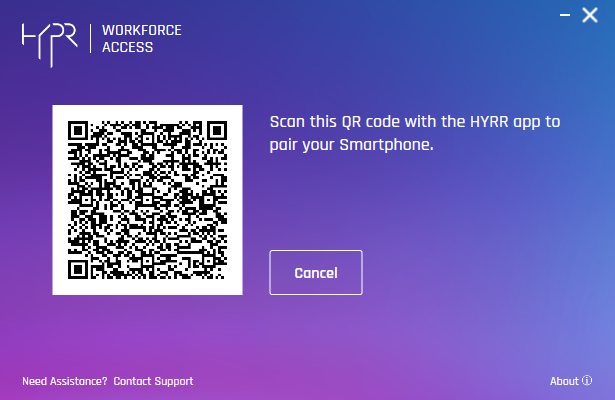
- Scan the QR code on the screen. You will be prompted to authenticate on your device.
- Once you are paired successfully, click Continue.
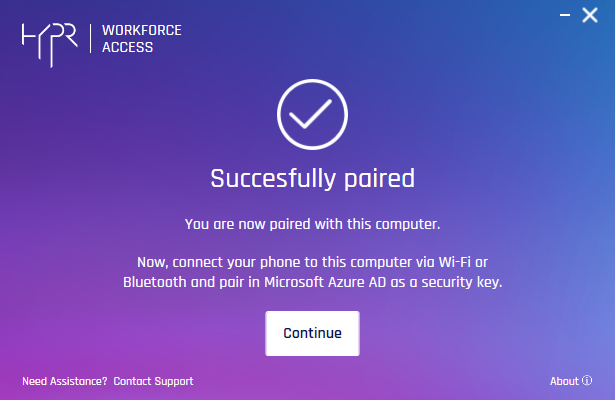
- Choose the method by which you will connect this machine to the HYPR Mobile App device.
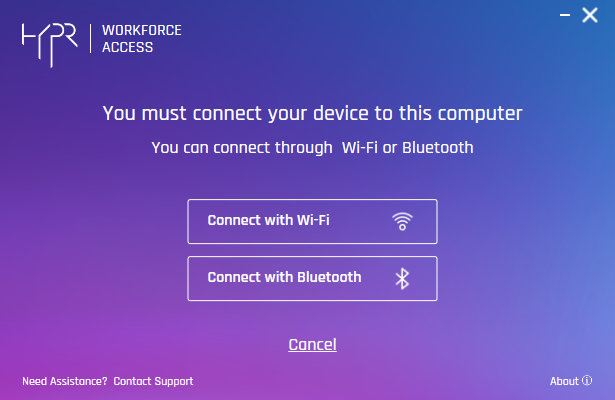
- Verify your connection (see Pairing Using Windows Bluetooth) is paired and the HYPR Mobile App is open. The web connection confirmation dialog remains unchanged, verifying that you are connected to the same wireless network as the workstation. This example uses the Bluetooth connection confirmation dialog.
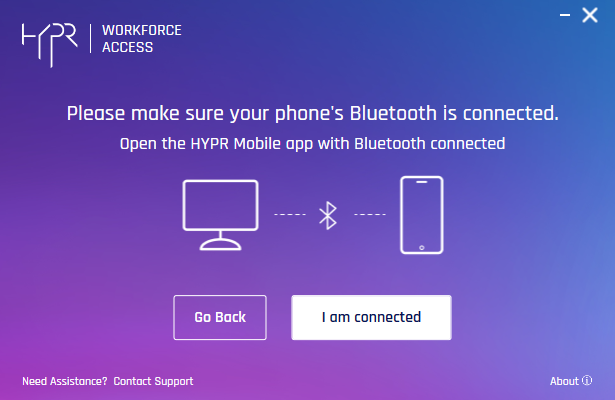
- A prompt appears to remind you to continue the process in Azure. Click Continue in AD to open https://mysignins.microsoft.com/security-info (see Pairing with Azure, below) licking View More Instructions opens this article).
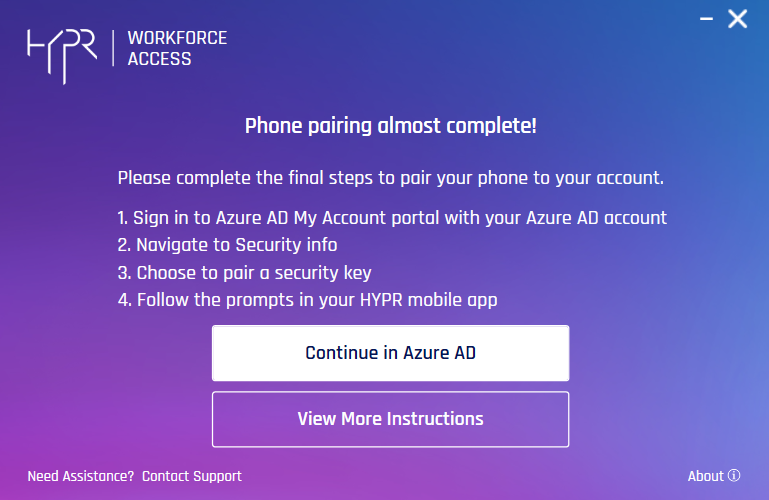
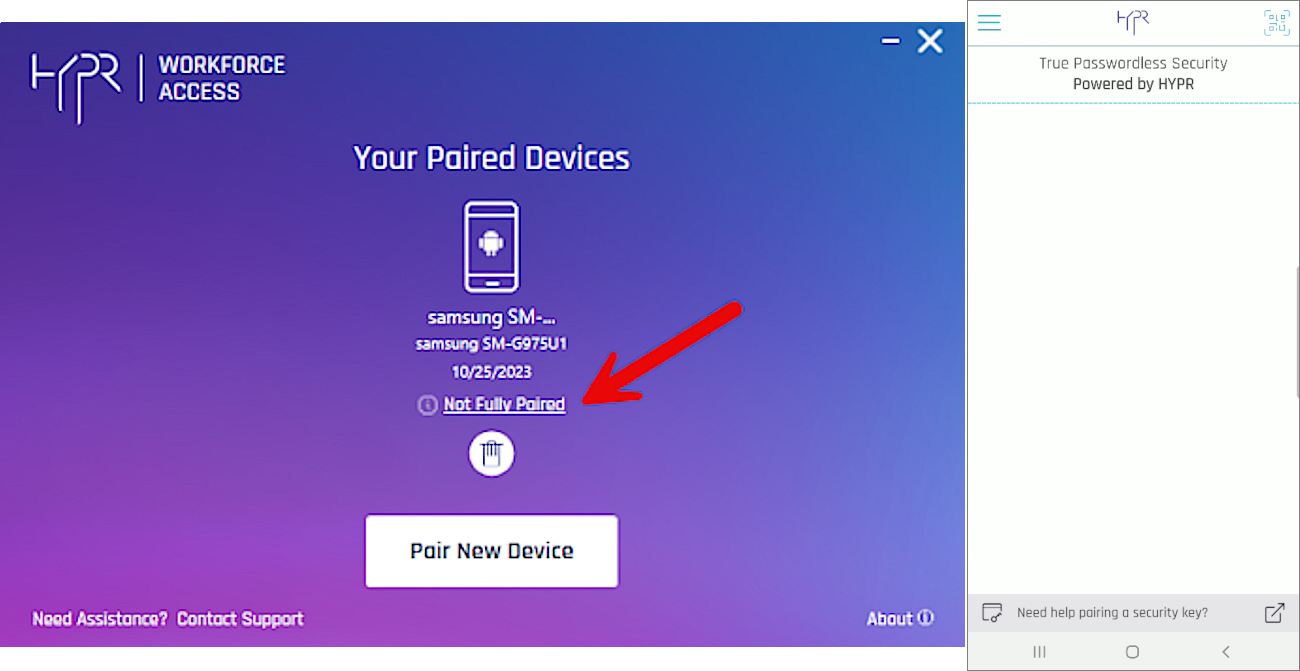
- HYPR Passwordless client returns to the main screen , now displaying your paired device. The device’s HYPR Mobile App menu now includes a section for My Security Keys. Open it. Here you will see the same Azure cloud-only account with which you logged into Windows.
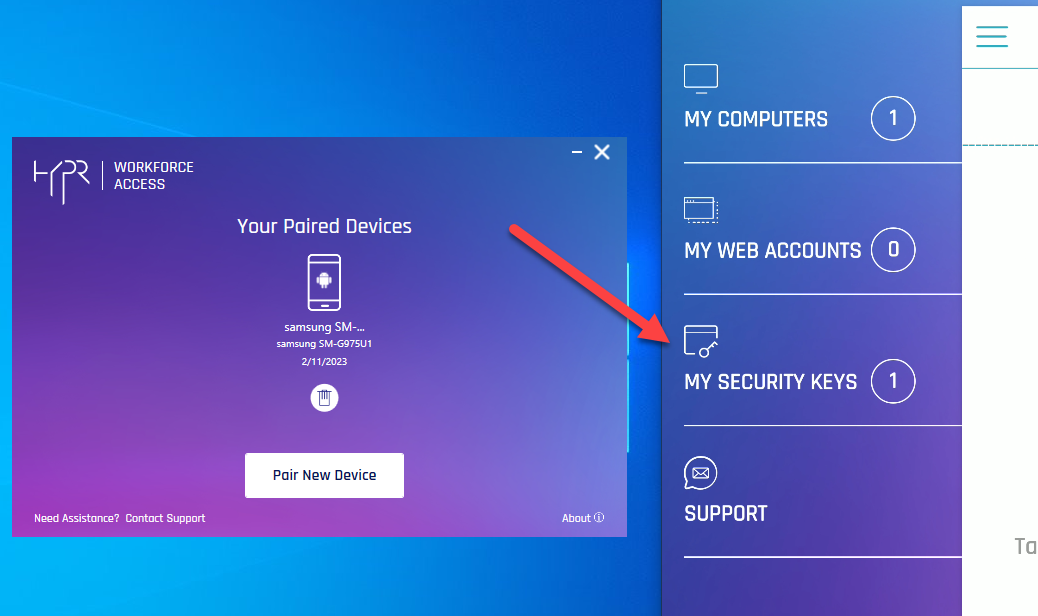
- The warning icon next to it indicates the user has not yet completed the pairing. Until pairing is completed, a Pairing incomplete warning will display in the HYPR Passwordless client for the mobile device, and the account shown in the HYPR Mobile App will bear a Pairing incomplete icon. The indicates the user is Paired with HYPR but not yet Paired with Azure. Clicking the red warning icon will re-open the Phone pairing almost complete! dialog.
Cache Returns
HYPR Passwordless client may not display a completed pairing right away. It may be necessary to close and restart the HYPR Passwordless client for the warnings to disappear.
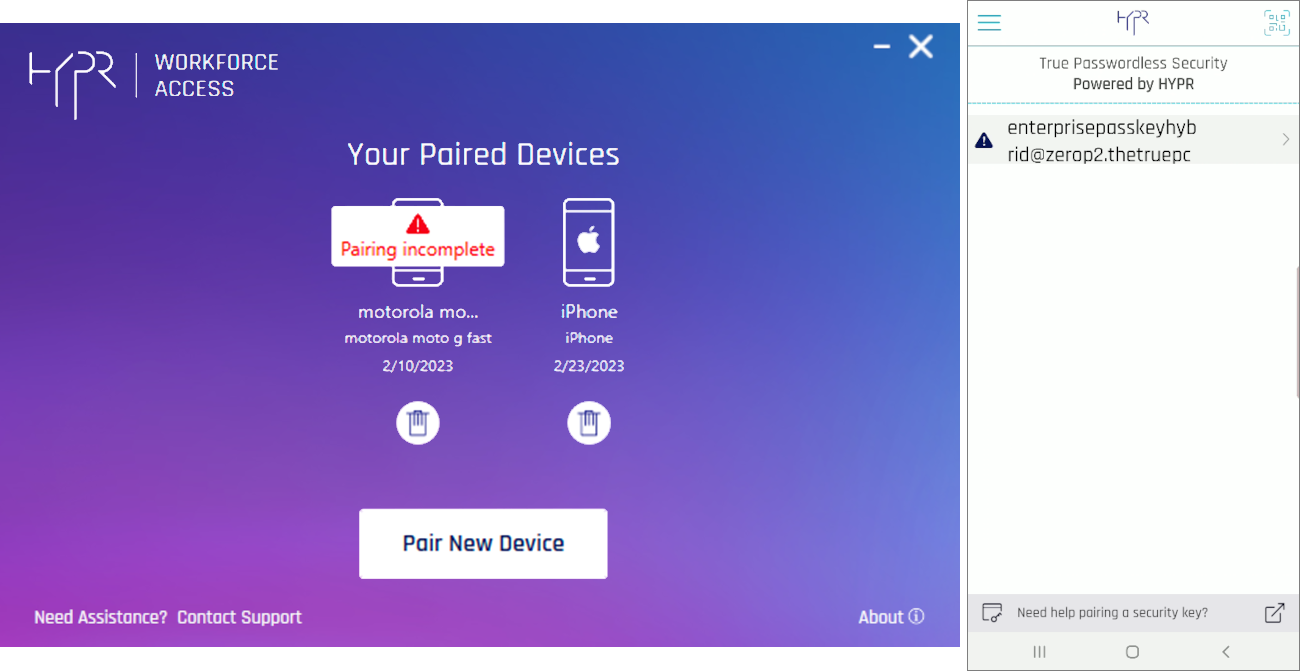
- On the HYPR Mobile App, tap the arrow next to the
userIdfor instructions on how to finish the pairing.
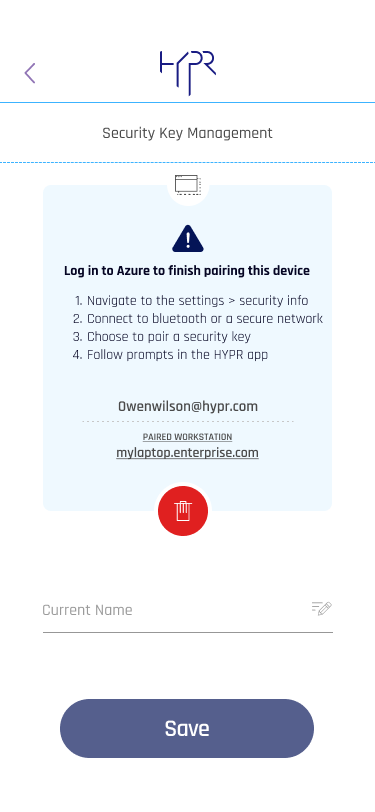
The user will now appear in the integration under User Management's Paired with HYPR tab. Continue to Pairing with Azure to complete your passkey registration.
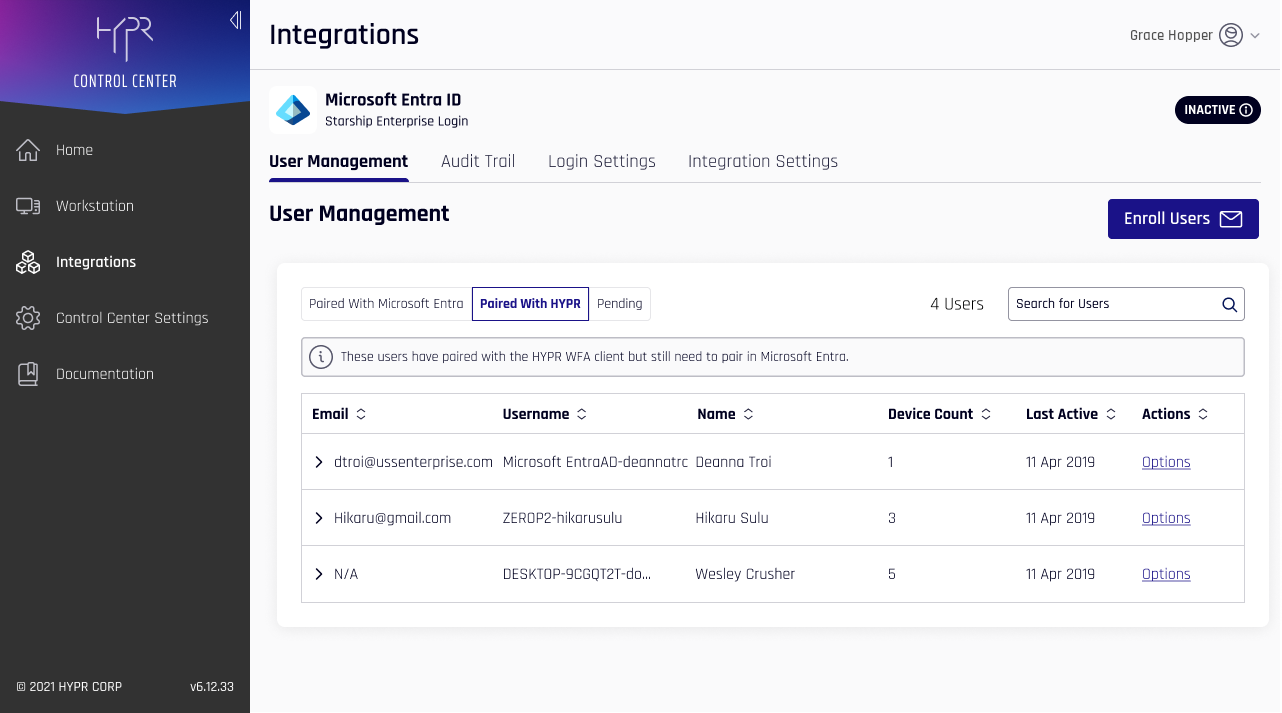
See Integration User Management in the main Integrations article for how to navigate User Management.
Pairing With HYPR on a Hybrid Azure/Entra Workstation
- Login to Windows using a hybrid account (i.e.,
carol.shaw@highlands_azure.com). - Launch the HYPR Passwordless client.
- Click Start Pairing.

- If your workstation has FIDO keys enabled, you will be prompted to Select Your Device to Continue. Choose Smartphone. Otherwise, proceed to the next step.
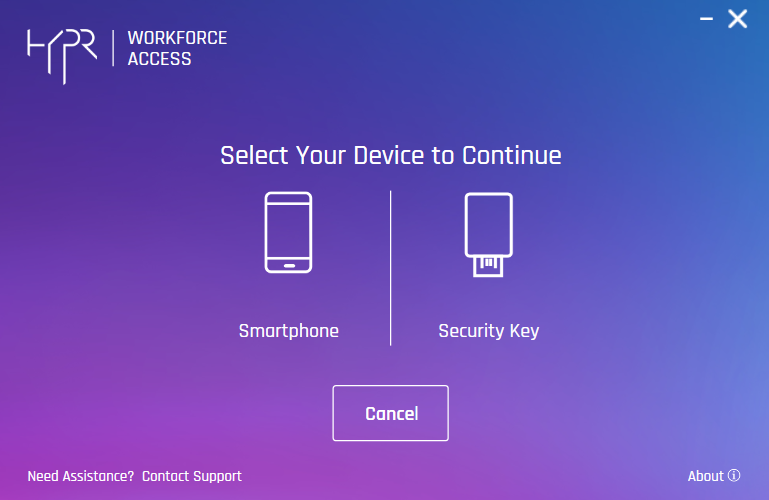
- The HYPR Passwordless client presents a QR code. Using a device with the HYPR Mobile App installed and ready to scan a QR code, click Begin Pairing.

- Scan the QR code on the screen. You will be prompted to authenticate on your device.

- You are Successfully paired. Click Maybe Later if you want to complete pairing at another time. Clicking Maybe Later will return you to the HYPR Passwordless client home dialog. To complete the pairing using Entra/Azure, click Continue.
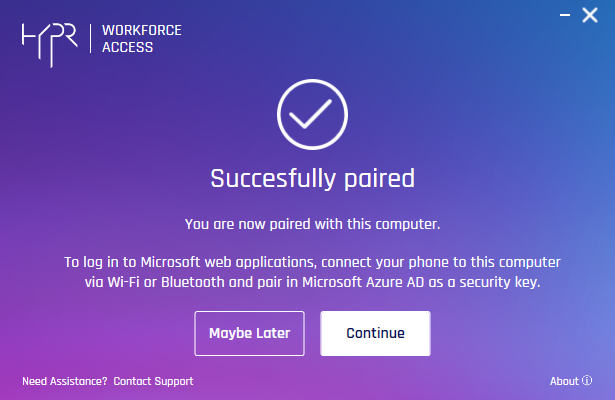
- Choose the method by which you will connect this machine to the HYPR Mobile App device.

- Verify your connection (see Pairing Using Windows Bluetooth) is paired and the HYPR Mobile App is open. The web connection confirmation dialog remains unchanged, verifying that you are connected to the same wireless network as the workstation. This example uses the Bluetooth connection confirmation dialog.

- A prompt appears to remind you to continue the process in Azure. Click Continue in AD to open https://mysignins.microsoft.com/security-info (see Pairing with Azure, below) licking View More Instructions opens this article).

- HYPR Passwordless client returns to the main screen , now displaying your paired device. The device’s HYPR Mobile App menu now includes a section for My Security Keys. Open it. Here you will see the same Azure cloud-only account with which you logged into Windows.

-
The warning icon next to it indicates the user has not yet completed the pairing. Until pairing is completed, a Pairing incomplete warning will display in the HYPR Passwordless client for the mobile device, and the account shown in the HYPR Mobile App will bear a Pairing incomplete icon. The indicates the user is Paired with HYPR but not yet Paired with Azure. Clicking the warning will re-open the Phone pairing almost complete! dialog.
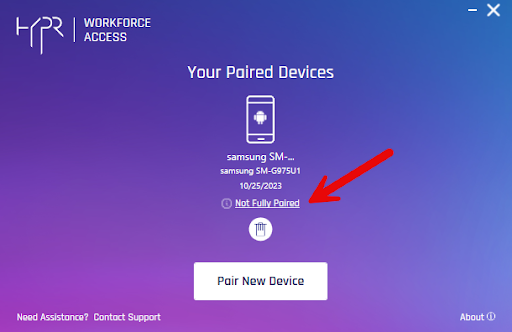
Cache Returns
HYPR Passwordless client may not display a completed pairing right away. It may be necessary to close and restart the HYPR Passwordless client for the warnings to disappear. In a hybrid pairing, HYPR Mobile App's My Security Keys page does not show a security key for this pairing.
The user will now appear in the integration under User Management's Paired with HYPR tab. Continue to Pairing with Azure to complete your passkey registration.
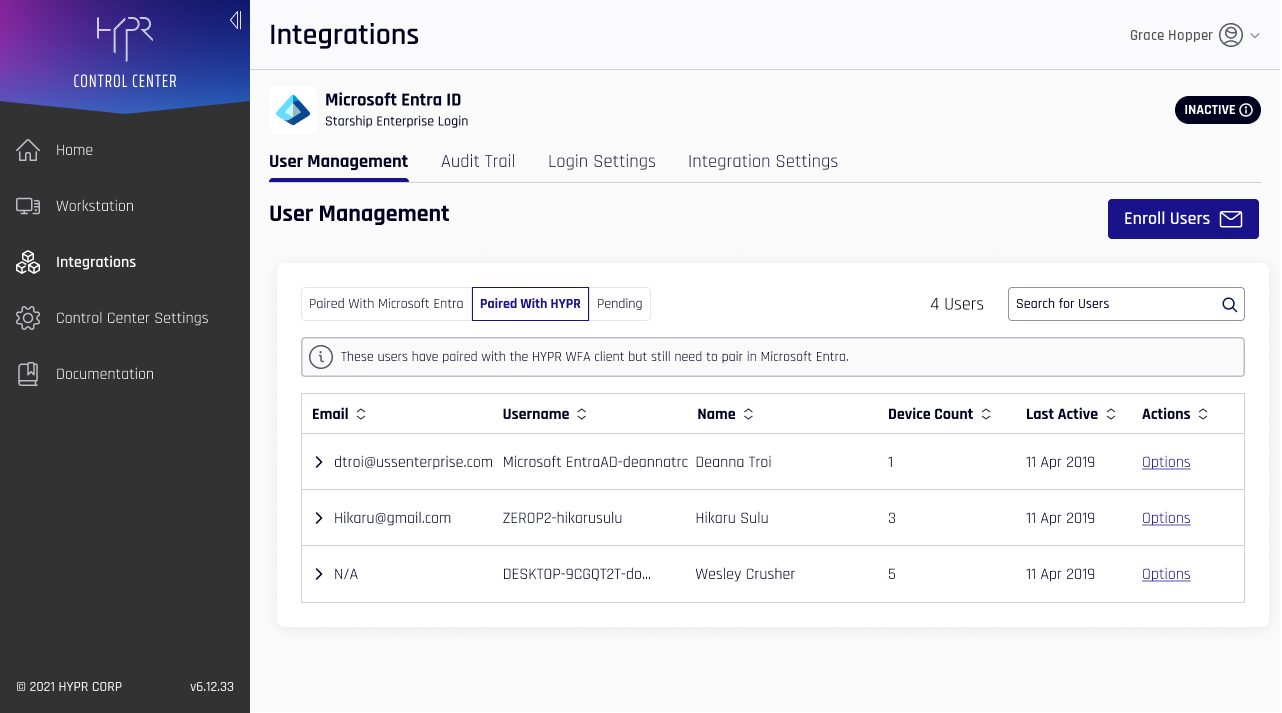
See Integration User Management in the main Integrations article for how to navigate User Management.
Pairing Using Windows Bluetooth
With the addition of Bluetooth pairing, a new set of dialogs comes into play if you use Bluetooth to connect to your network. The pairing process may refer to Windows flows for connecting your device to your computer via Bluetooth; we have included this flow here for reference.
Devices paired using Bluetooth are able to use this connection to authenticate in Offline Mode.
Following are the screens presented by Windows when using Bluetooth to register a security key for the first time.
After seeing these notifications, you will continue with the Entra/Azure FIDO portion of pairing.
Back to Whence You Came
In the middle of pairing? Jump back to continue.
Pairing With Azure
Back on the Azure VM:
-
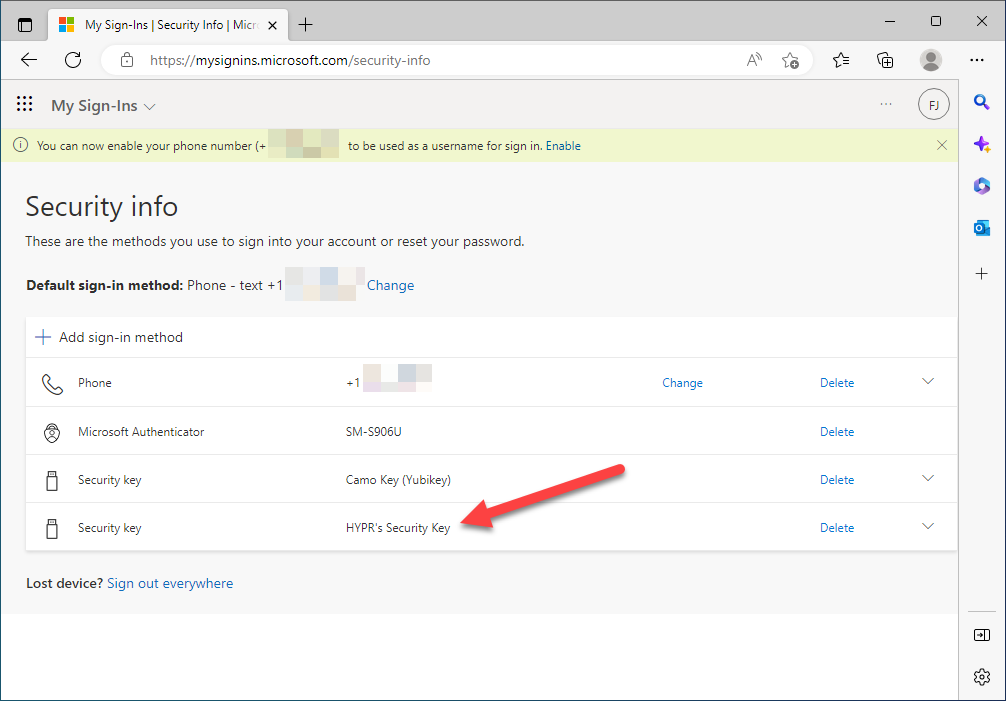
Login to https://mysignins.microsoft.com/security-info. This will take you to the screen below.
-
Select UPDATE INFO.
Get the Edge
If you are using Microsoft Edge, you should not need to manually login. Edge will have a desktop SSO-like experience where you are not prompted. Chrome and FireFox will prompt you.
-
Here you see all of the authenticators registered for the user. Azure traditionally requires at least one authenticator, which depends on how the tenant is configured. Usually it will be phone and/or text. Click Add sign-in method.
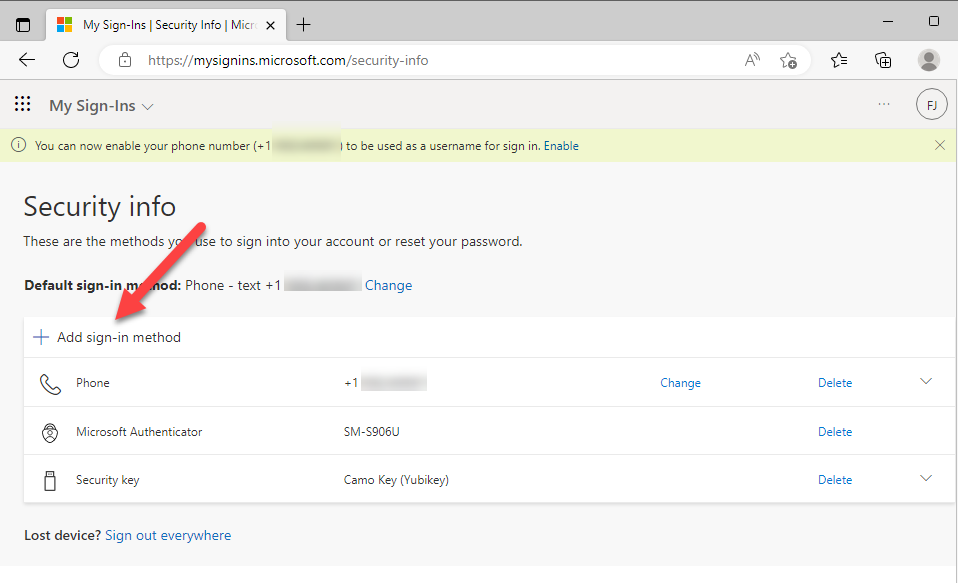
- The Add a method options will depend on the configuration of the tenant, but in this case, select Security key, then click Add.
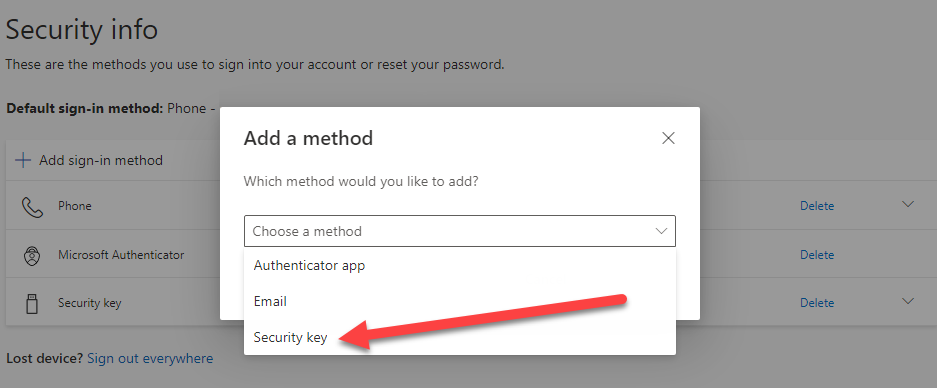
Note
Microsoft may require MFA depending on how you logged in initially. You need to complete MFA to change authentication methods (add/delete).
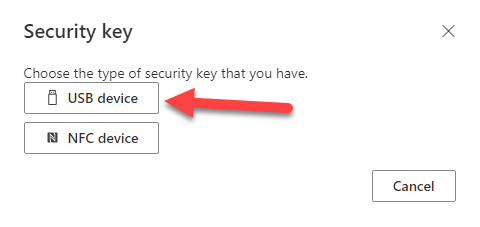
- Confirm the Security key type; select USB device.
- Microsoft then prompts you to have your key ready. Open the HYPR Mobile App on your device. This is required for the HYPR Mobile App to virtually connect to the USB on the VM/workstation. Once the HYPR Mobile App is open, click Next.
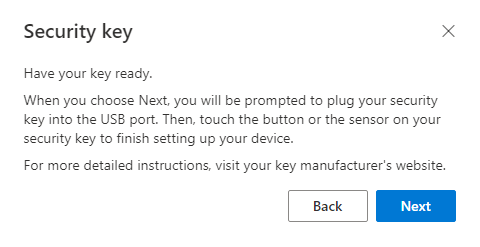
The next few prompts come from the browser and the Windows operating system as part of the FIDO2 protocol.
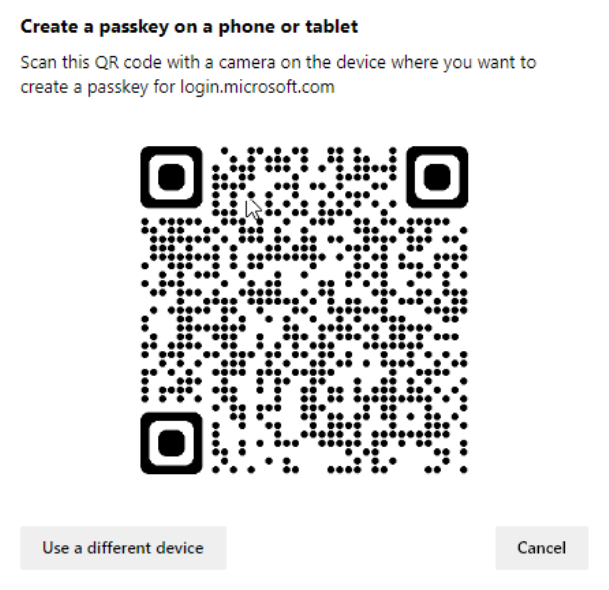
- If the browser version supports passkeys, this will appear. Click External security key or built-in sensor. Some versions of this dialog display the choice as Windows Hello or external security key; this option is valid for those cases, and should be chosen if it is presented instead of what appears here.
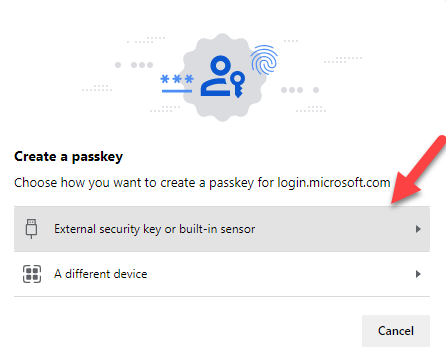
Wrong QR
Occasionally on BLE-enabled machines, the following dialog will display when clicking External Security key or built-in sensor. Do not use this QR code; instead, click Cancel on this dialog and click Use a different device on the bottom left corner of this dialog.
- On the Security key setup dialog, click OK.
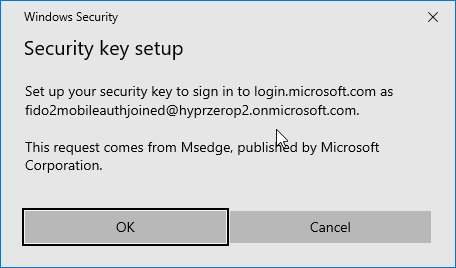
- On the Continue setup dialog, click OK.
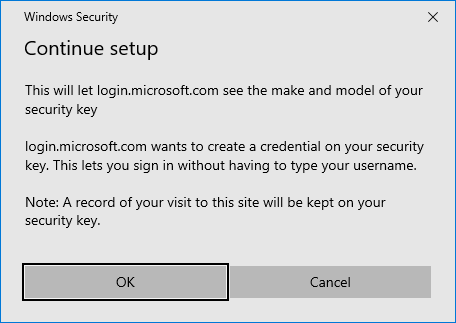
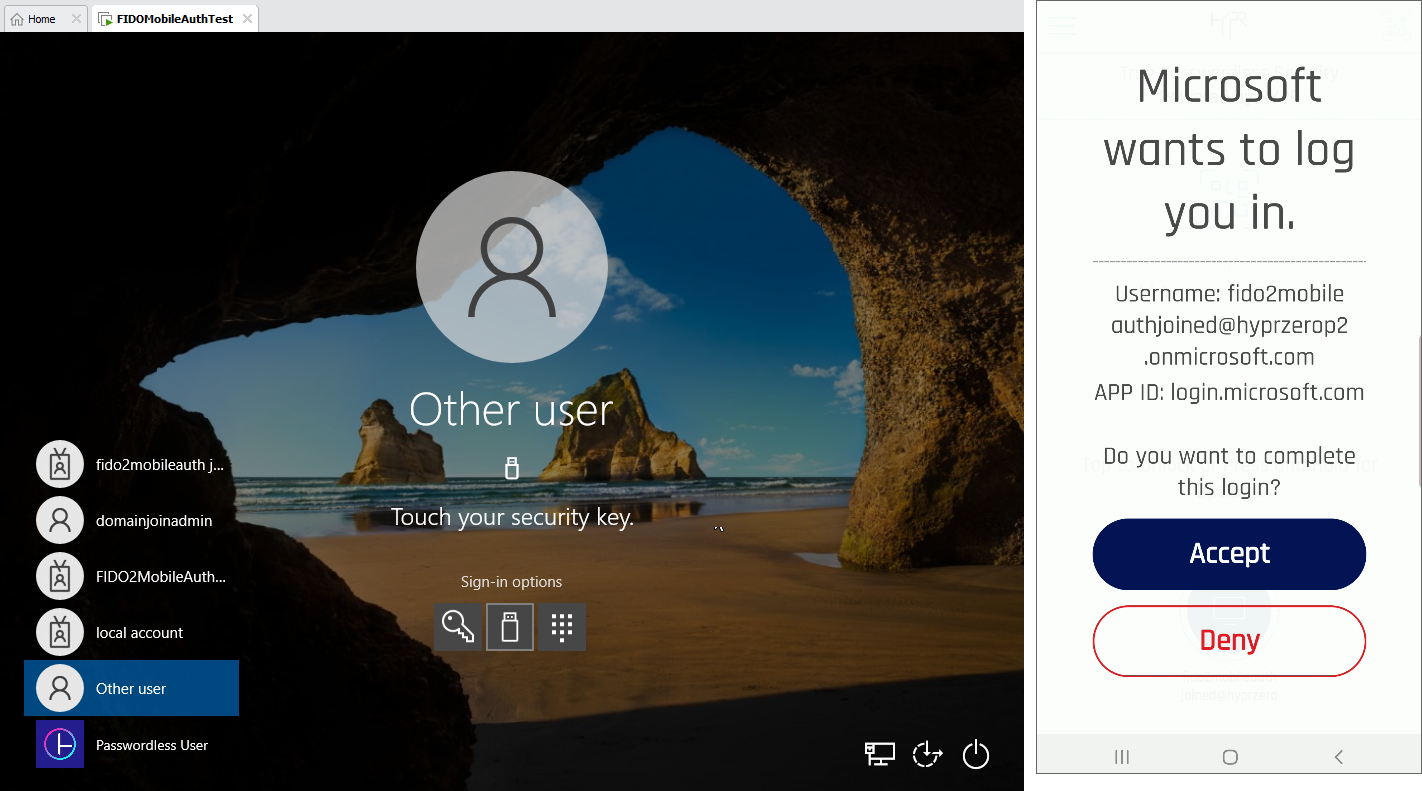
- Now Microsoft prompts you to touch your security key. You will see a verification screen to add this device on the HYPR Mobile App. Touch Accept.
Virtually Blind
If you see this message from Microsoft instead, it means that the workstation did not discover the mobile device. You will not be able to continue until this is resolved.
- HYPR Mobile App will prompt you to register a biometric. Follow those instructions.
Separate Biometrics
This biometric is specific to Azure; it is not the same biometric requested for the HYPR QR code scan.
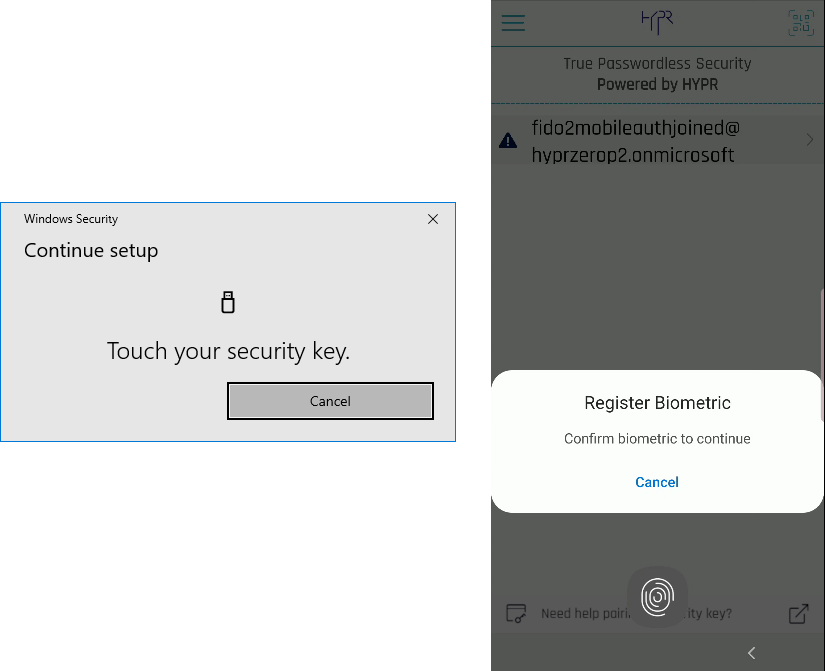
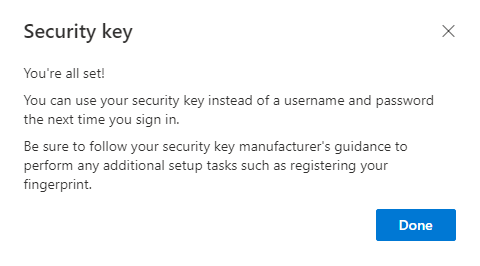
- Once the biometric is registered, Microsoft will ask you to name the new security key. Have at it.
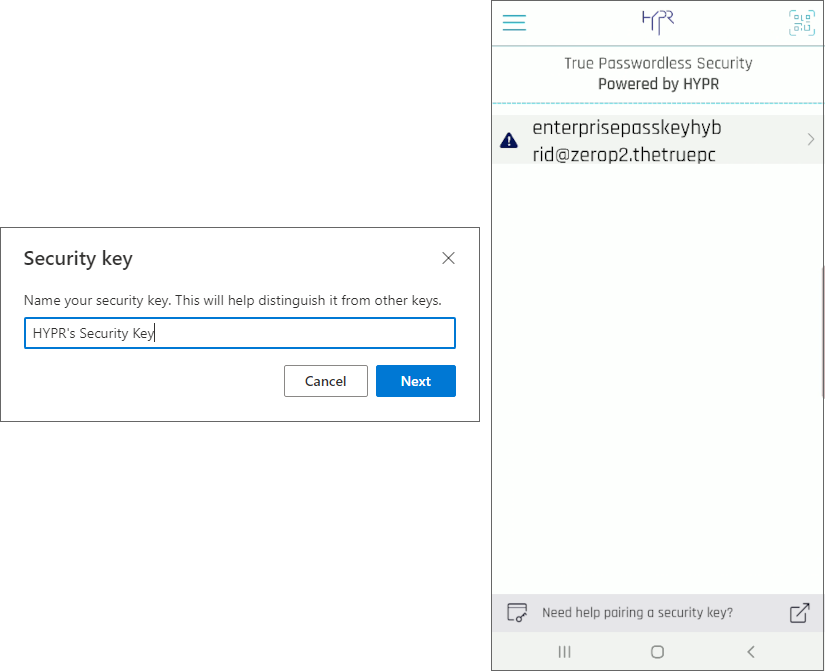
All set. You now are able to leverage HYPR’s FIDO2 Mobile Authenticator as a Security Key in Azure, and you will see it listed as an available authenticator:
HYPR Mobile App Changes
Now that you are paired with Azure, the HYPR Mobile App will change.
The first time the My Computers page is opened, a banner message will display stating, "Learn how to pair a security key." Clicking this banner opens this article. The banner will remain visible until cleared by clicking the X at right.
When scanning HYPR’s QR code the HYPR Mobile App will display the workstation pairing under the My Computers section.
- Azure/Entra domain-joined:
- Fully paired computers are in a dark blue bubble
- Partially paired computers are in a light grey bubble
- A deleted security key reverts the bubble back to grey/partial
- All other (AD joined, hybrid joined, and non-joined) paired computers are in a dark blue bubble
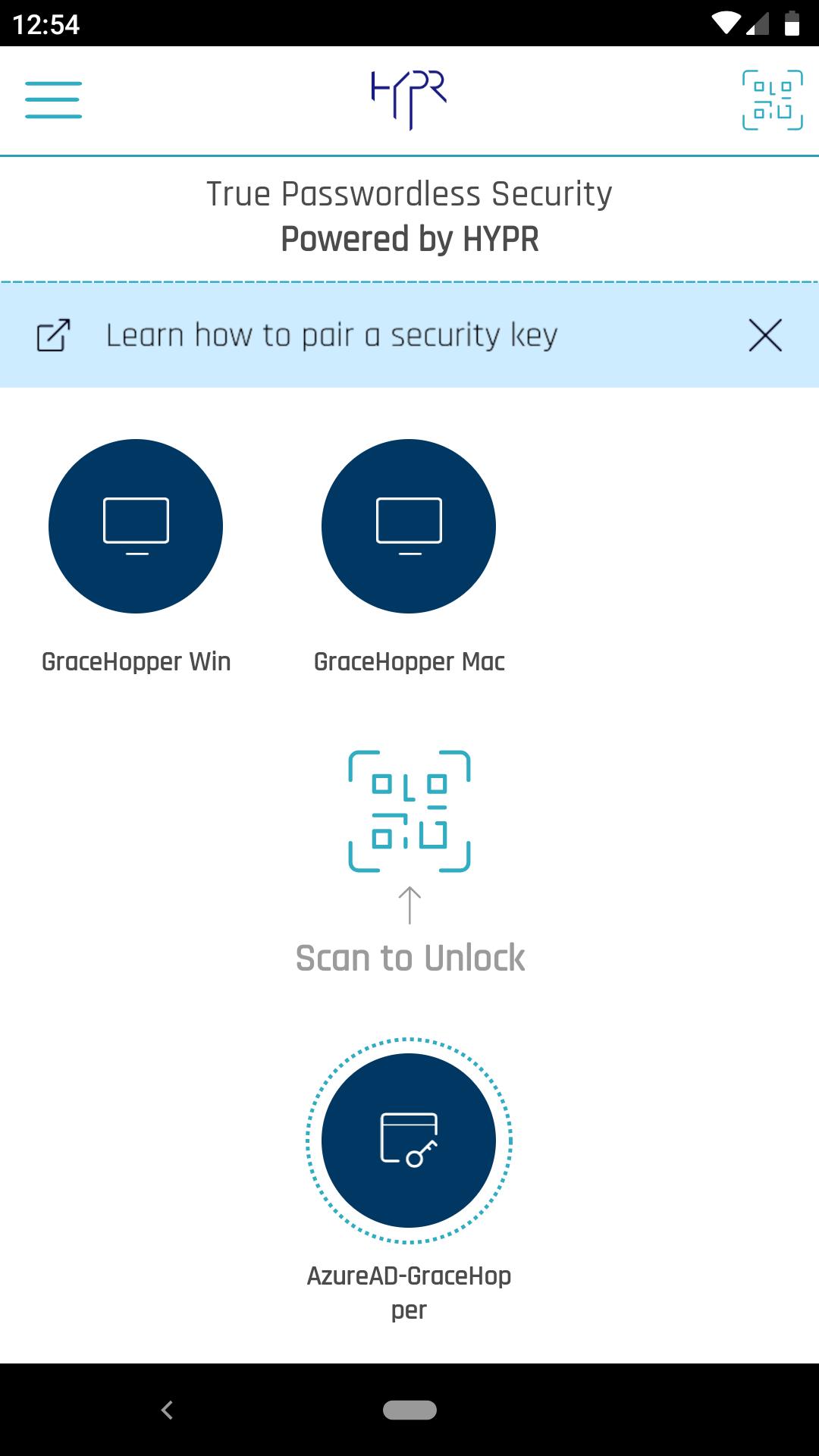
Navigate to the Device Manager, and tap My Security Keys.
When you tap My Security Keys, the warning icon next to the username is now gone.
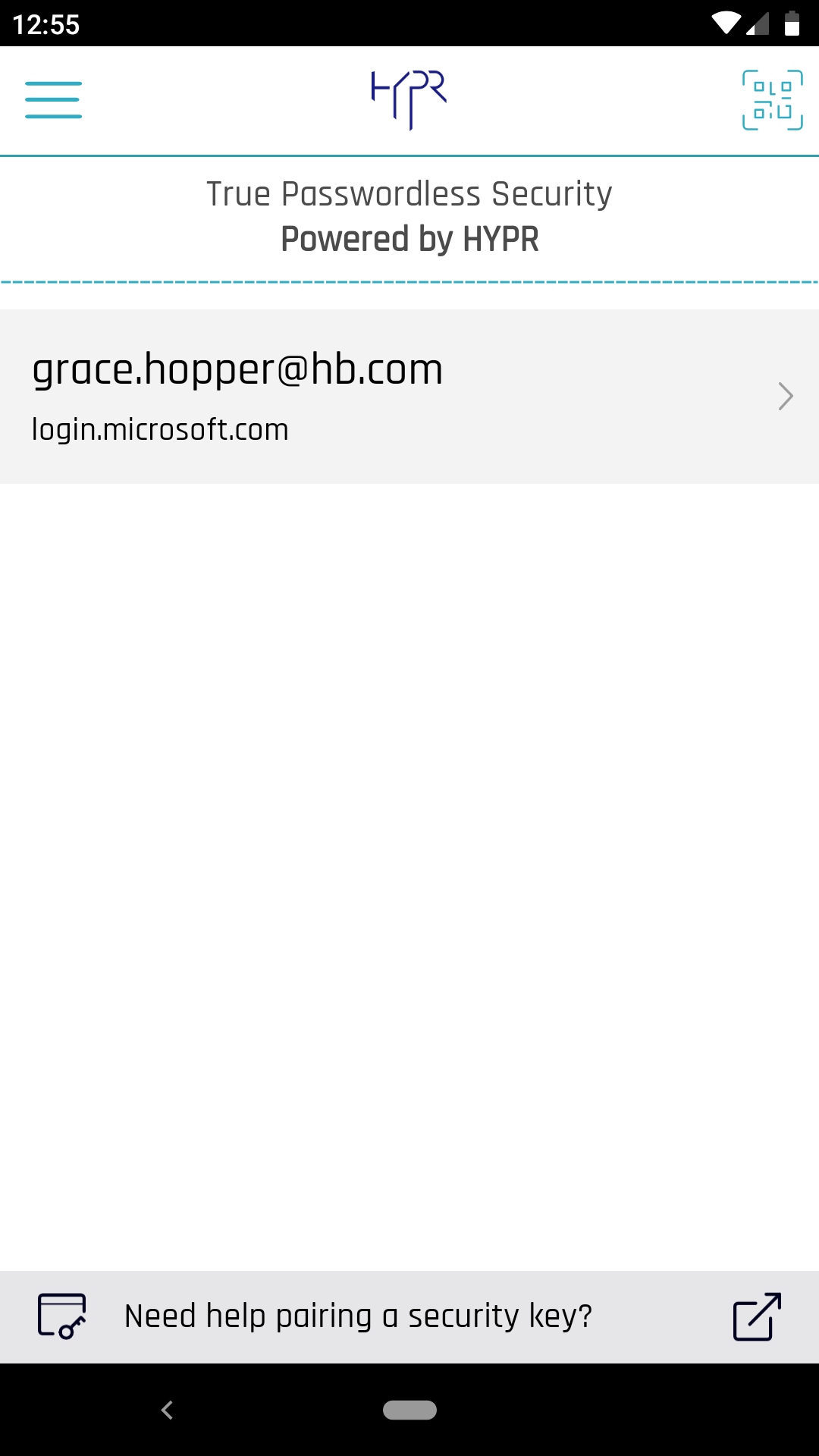
Selecting the arrow at right now shows the details (username, RP ID, Last Used) of the pairing and allows you to rename it, delete it, or view the login activity; similar to My Computers or My Web Accounts.
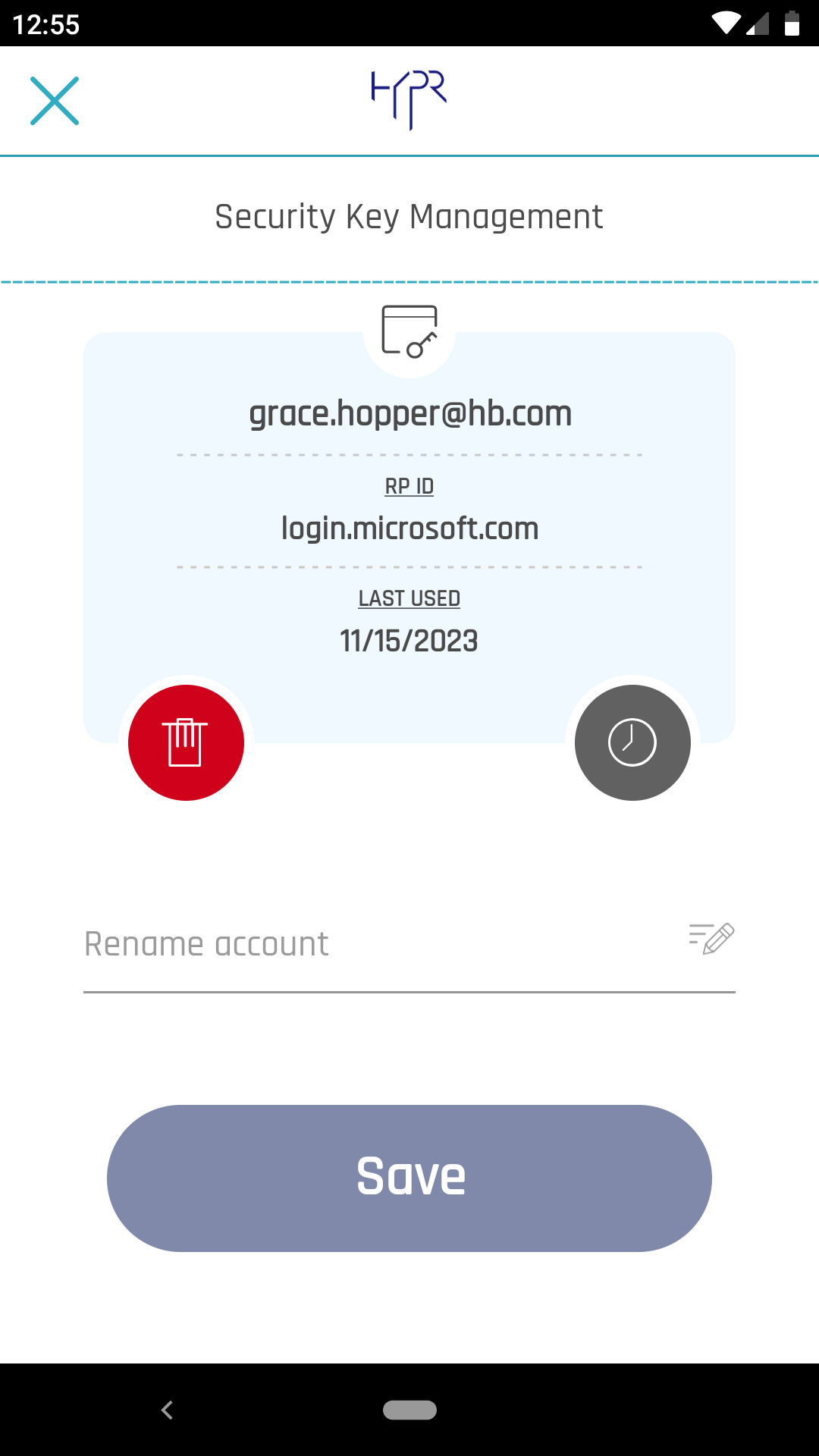
While the Integration is DISABLED, if a user attempts to pair with HYPR, the HYPR Mobile App will issue a warning.
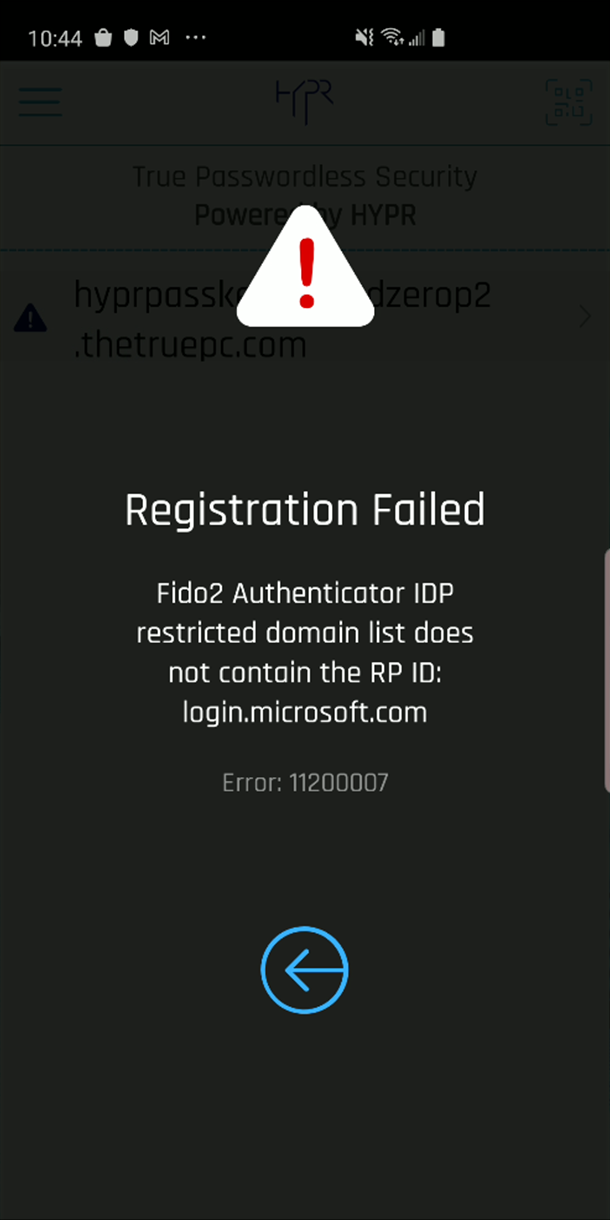
Likewise, if domains have been restricted in the Desktop Client tab, and the user is not part of an accepted domain, HYPR Mobile App will issue the following warning:
Tap to Login
When using the HYPR Mobile App Tap to Login function to authenticate to an Entra domain-joined HYPR Passwordless client, the option to use a security key will be absent from the method choices.
Invitation Emails
Unlike other integrations' enrollment processes, HYPR Enterprise Passkey does not send invited users a link to pair with Device Manager. Instead, the email is informational only, and the link provided connects to Pairing with HYPR in this article.
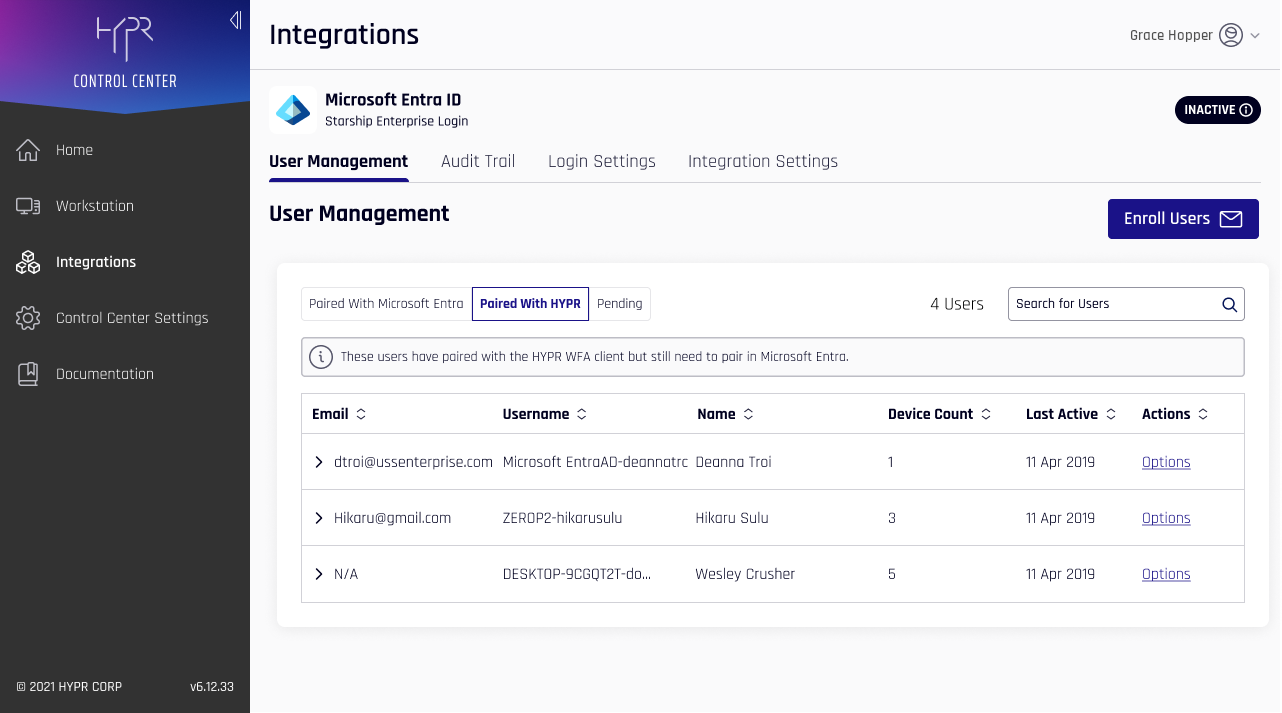
User Management for HYPR Enterprise Passkey
Paired with HYPR and Paired with Azure
Due to the infrastructure underpinning the HYPR Enterprise Passkey, in addition to the Pending state shown in other Integrations, users may be either Paired with HYPR (awaiting Enterprise Passkey pairing completion) or Paired with Azure (fully paired as a HYPR Enterprise Passkey), instead of Enrolled.
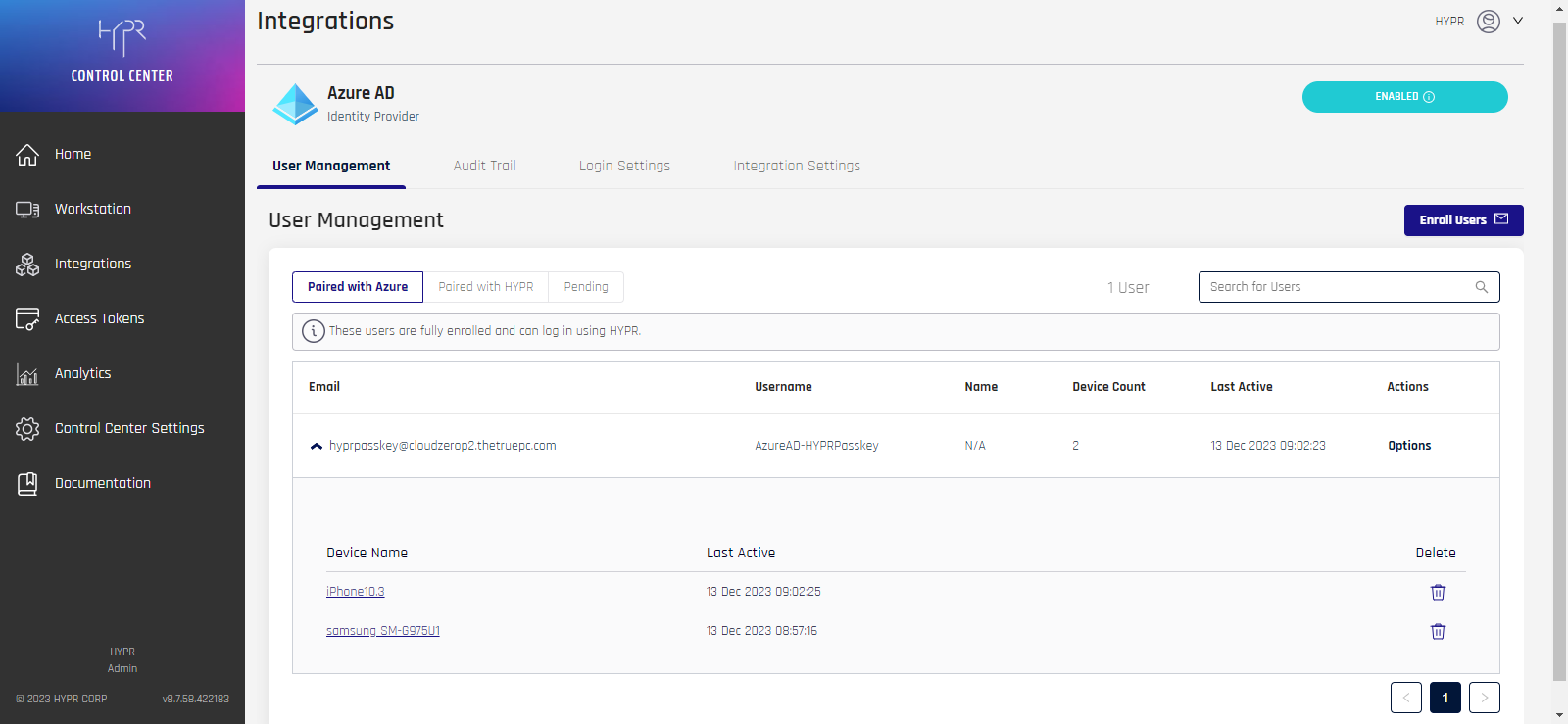
The information shown under each tab is the same as described here.
| Column | Description |
|---|---|
| The Entra/Azure account email. | |
| Username | The Entra/Azure username. |
| Name | The user's full name, if entered. |
| Device Count | The number of devices registered. |
| Last Active | The last time this device was used. |
| Actions | Hover on over Options; here you may Delete the account. |
Expanding a user displays all registered FIDO2 devices, including the ones that may be registered with other Integrations or IdPs.
The labels here are as follows:
| Column | Description |
|---|---|
| Device Name | The name of the device as assigned by the user. This may be the default manufacturer's label or a name given to the device by the user in Device Manager. Click this value to open Device Details for that device. |
| Last Active | The time this key was last in use. |
| Delete | Click the trash can icon to delete this device from this user account. |
User Device Details
For users that are Paired with HYPR, drilling into one of the Device Name values will open Device Details.
- The Mobile Devices tab shows the FIDO2 web domain and the FIDO2 username which were paired
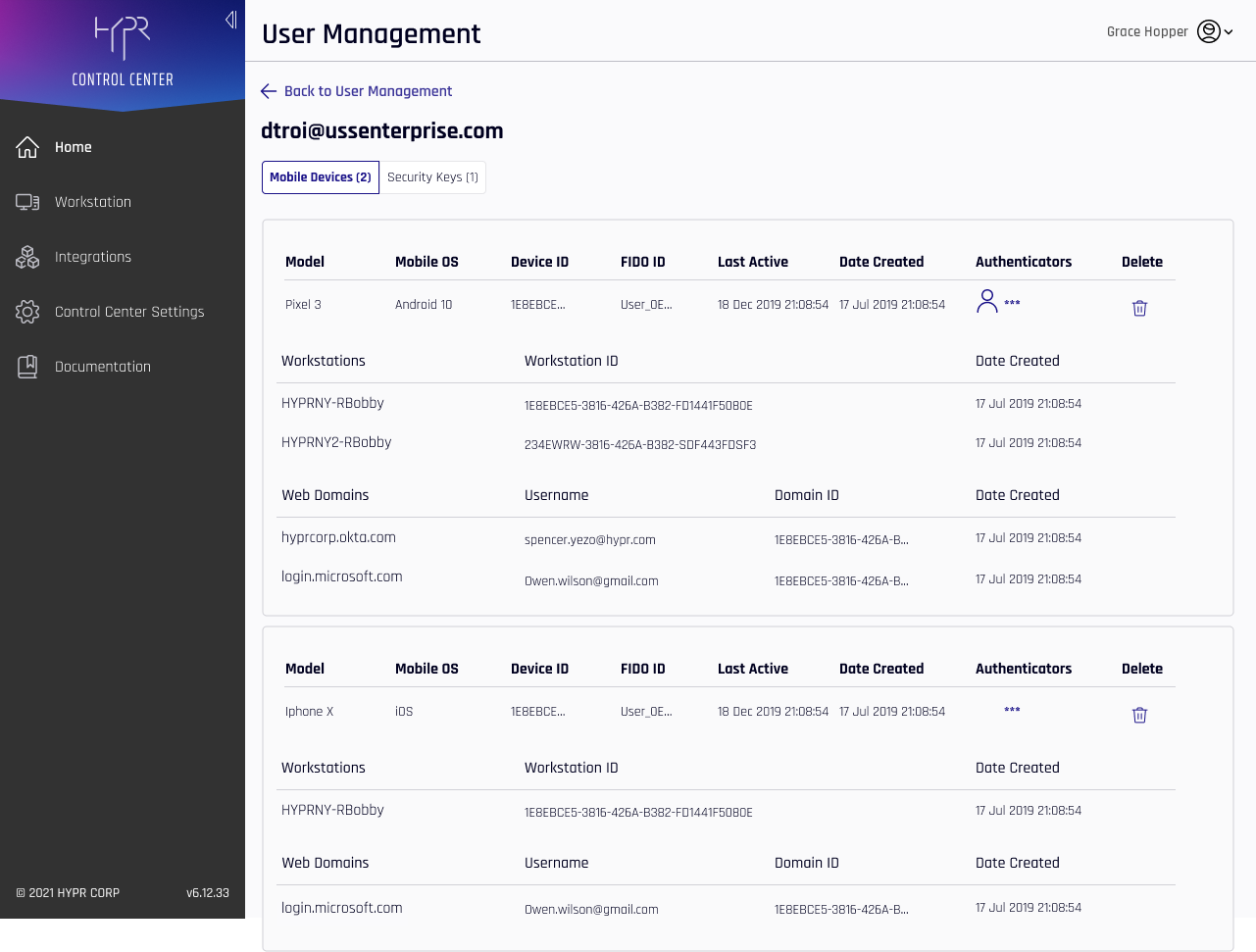
The following additional columns appear in this list:
| Column | Description |
|---|---|
| Model | The model of the Enterprise Passkey mobile device. |
| Mobile OS | The operating system (OS) of the Enterprise Passkey mobile device. |
| Device ID | The deviceId attribute assigned to this device. |
| FIDO ID | A unique number for the FIDO credential. |
| Date Created | The time at which the device pairing was made for the device or machine in question. |
| Authenticators | Icons matching applied authenticators from Policy Management appear here. |
| Delete | Click the trash can icon to delete this device or domain. A confirmation will display before HYPR returns to this page. |
| Workstations | A list of workstations to which this HYPR Mobile App is paired. |
| Workstation ID | The unique identifier for the workstation. |
| Web Domains | The fully qualified FIDO2 web domain. |
| Username | The FIDO username, which may differ from the domain username. |
| Domain ID | The unique identifier for the domain. |
- The Security Keys tab shows a few different properties associated only with passkeys
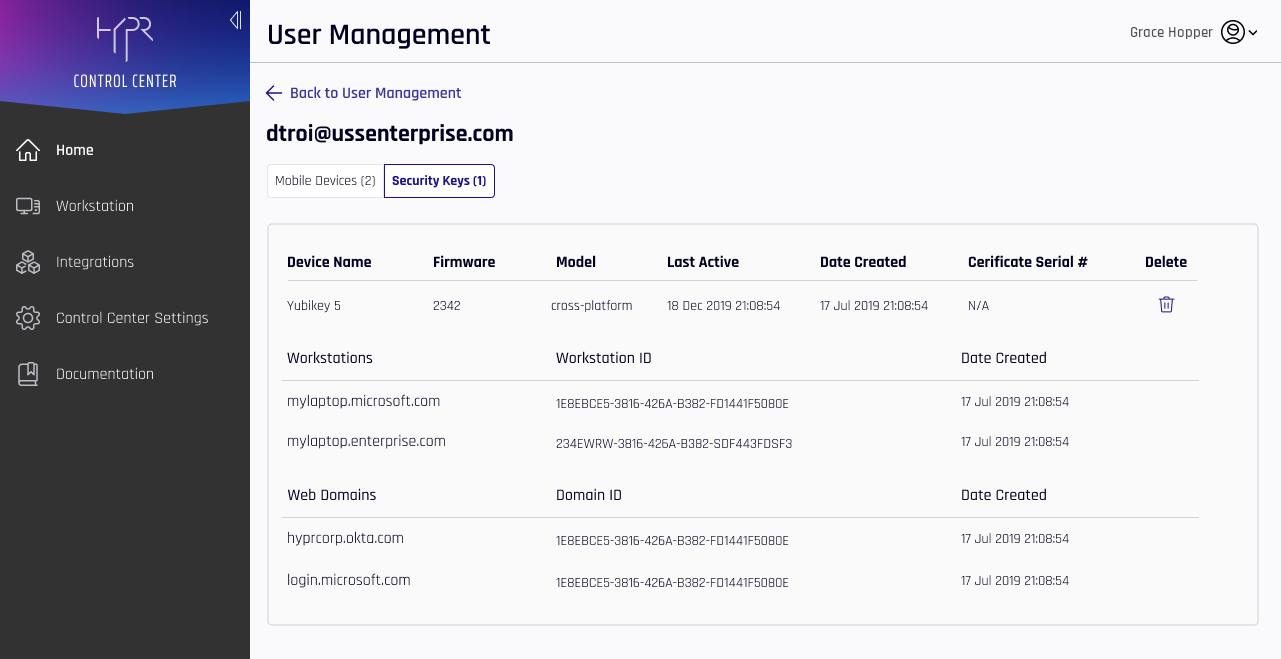
The values not already defined that appear under Security Keys are as follows:
| Column | Description |
|---|---|
| Device Name | The name of the device. This may be the factory label, or may have been changed by the user in Device Manager. |
| Firmware | The firmware version used by this device. |
| Model | platform: A security key built in to the machine; typically a biometric. |
| Certificate Serial # | The serialized number in the production series for this device. |
- On either tab, click Back to User Management to return to the main User Management pane.
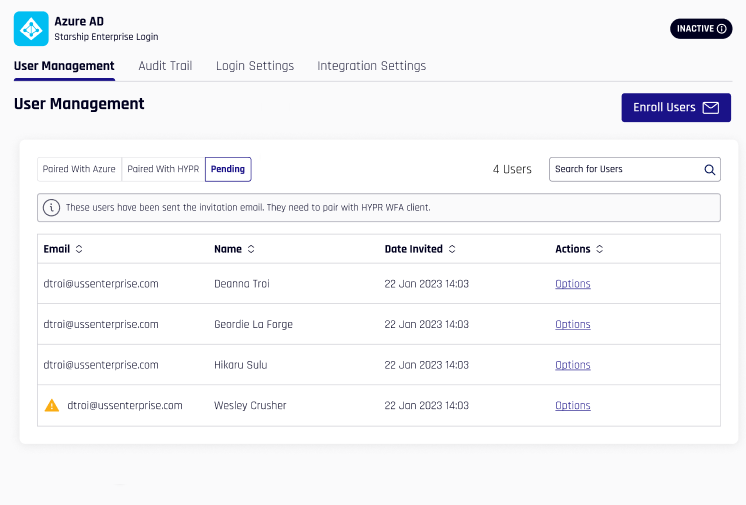
Unpaired Users
Users who are Paired with HYPR or Paired with Azure who unpair their devices will be moved to the Pending tab of User Management; a warning icon appears next to the Email field. Hovering over the icon, the text appears, "This user unpaired from HYPR." Likewise, accounts that are unpaired with Azure but still retain the HYPR pairing will be moved under Paired with HYPR.
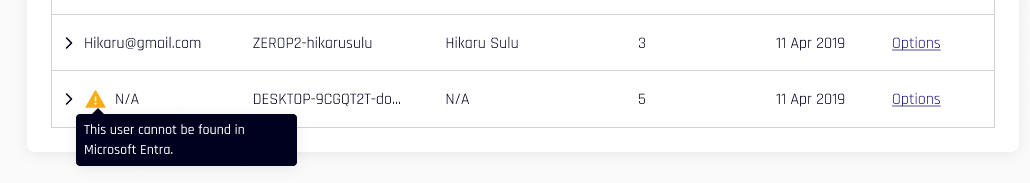
Likewise, if an Entra/Azure account is suspended or removed, HYPR shows an icon indicating, "This user cannot be found in Microsoft Entra." HYPR calls Entra/Azure to confirm account statuses when this page is opened.
Logging In with HYPR Enterprise Passkey
Logging In to Windows
Lock the VM or workstation and then unlock it. Windows defaults to the last account and method used to successfully log in. The example shown here used a Windows Hello PIN, so that's what Windows is putting forth:
- Open HYPR Mobile App and select Sign-In options.
- Tap the security key icon.
- Microsoft will send the user presence (UP) verification to the HYPR Mobile App. On the HYPR Mobile App, tap Accept.

- Complete the biometric prompt (User Verification).
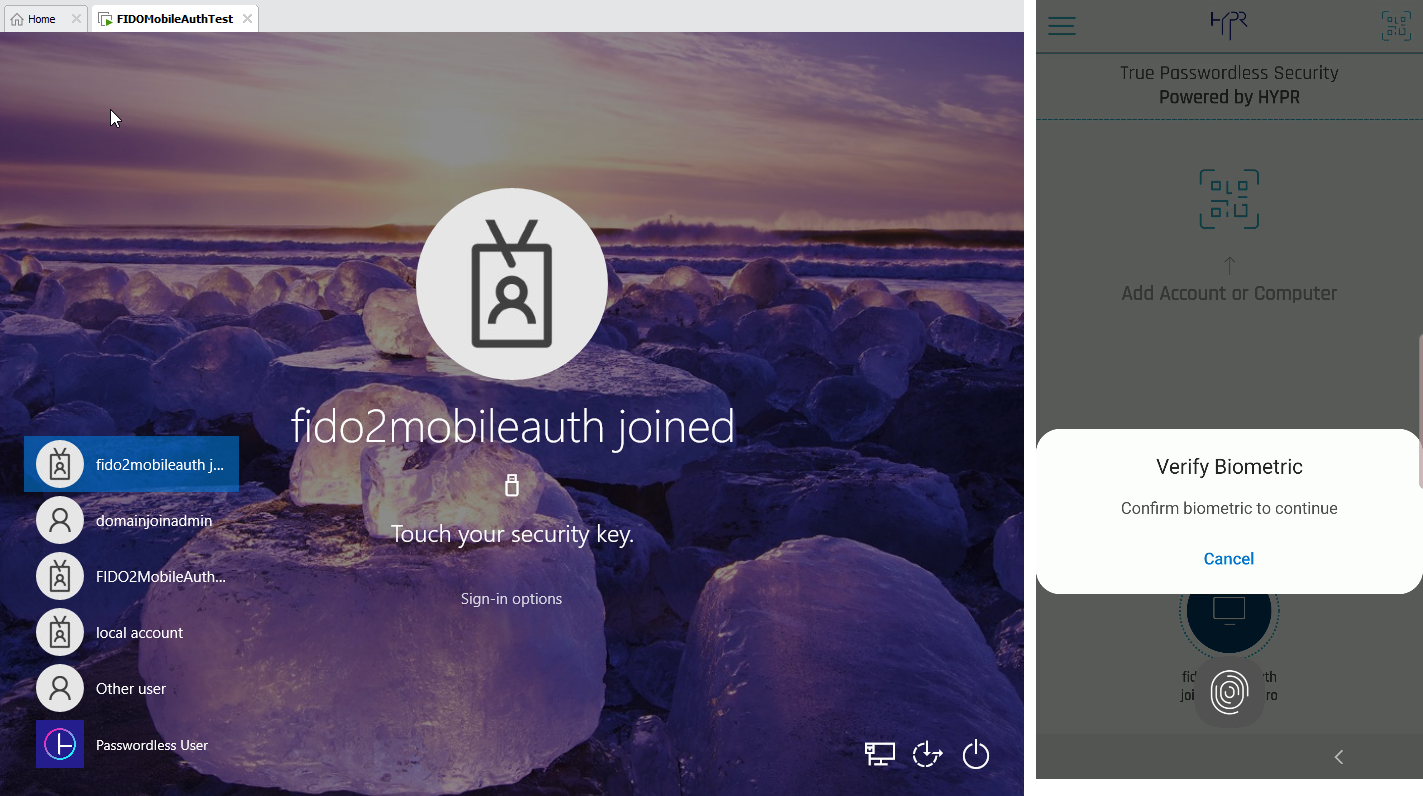
Once this is completed, you will be logged into Windows!
State Dependency
The Windows login experience depends on the state of the Windows OS.
Sometimes it will behave like above. Other times as soon as you wake it, it will start the FIDO authentication process and send the user presence (UP) verification to the mobile device for “Other User”. This is perfectly fine; after HYPR Mobile App’s Accept and biometric authentication, Microsoft will recognize for whom the FIDO keys are, and switch the username to the correct one.
Logging In to Azure Protected Content (Like O365.com)
- Login with the paired user account in Chrome to ensure you get a login prompt (Edge will use SSO).

- You may get the default login screen with password or you may just get the FIDO2 prompt. It all depends on the browser and what Microsoft has recorded. If you see the password prompt, select Other ways to sign in.
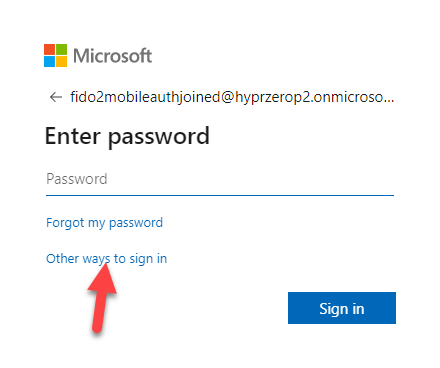
- Select Use Windows Hello or a security key.
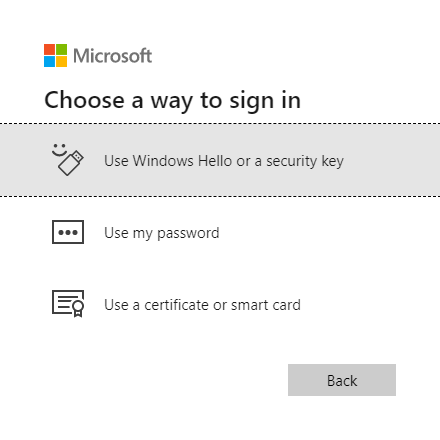
- Open the HYPR Mobile App and select Security key.
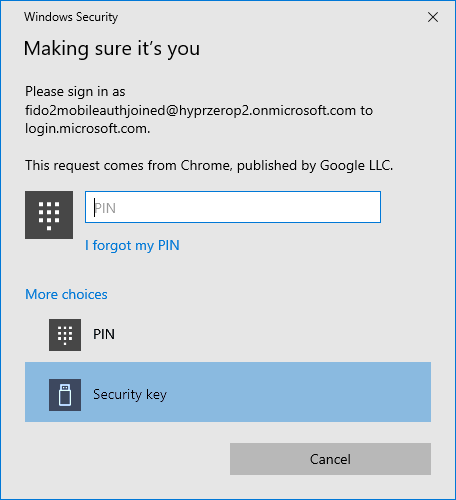
- Go through the motions for FIDO UP and User Verification (UV), and you are now in Microsoft Office.
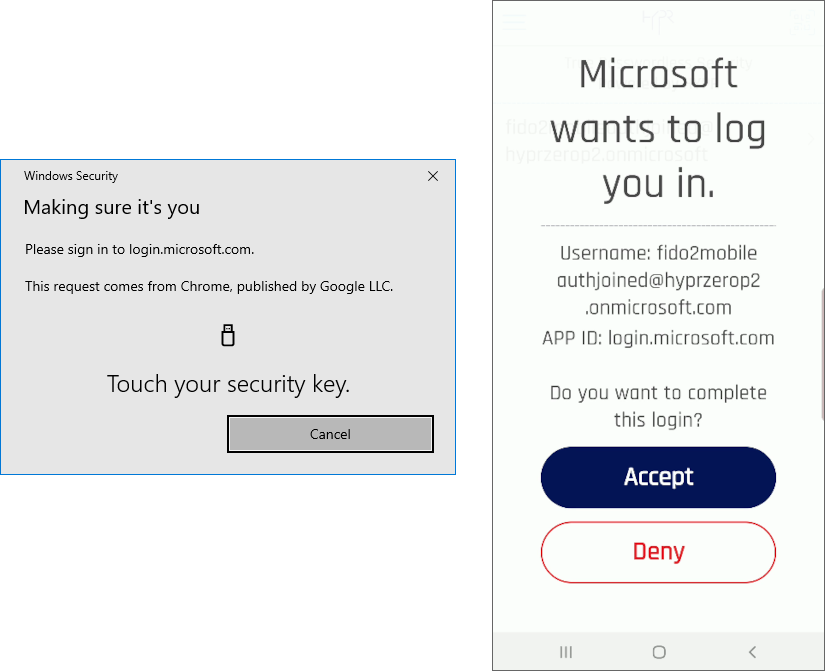
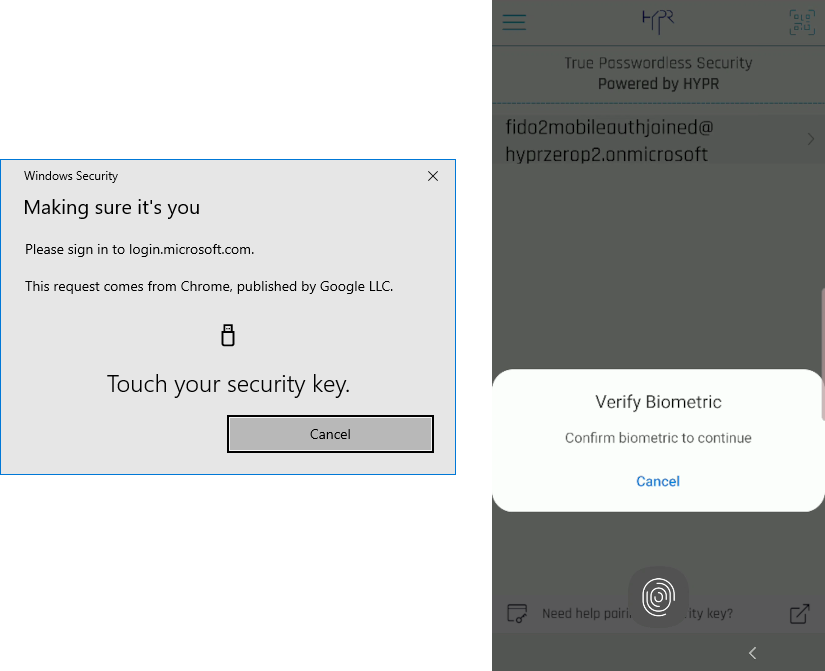
Logging In Using Windows Bluetooth
With the addition of Bluetooth authentication, a new set of dialogs comes into play. Following are the screens presented by Windows when using Bluetooth to authenticate a security key.
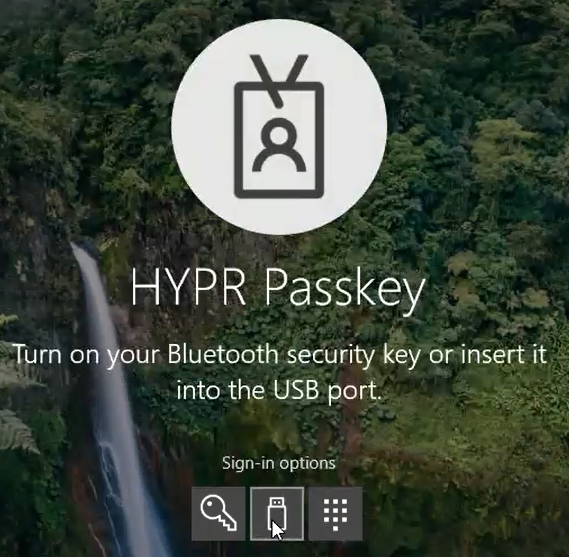
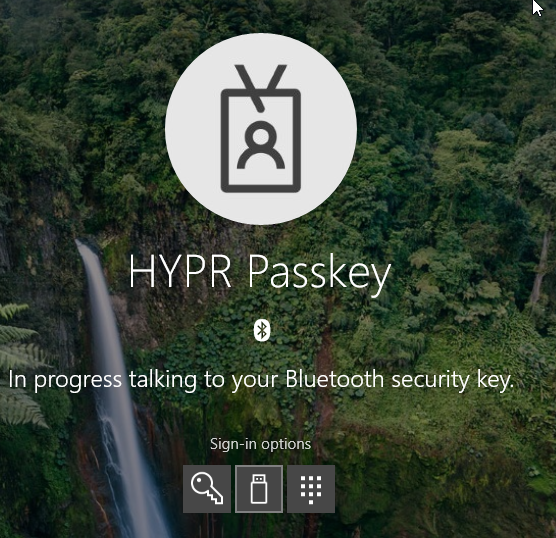
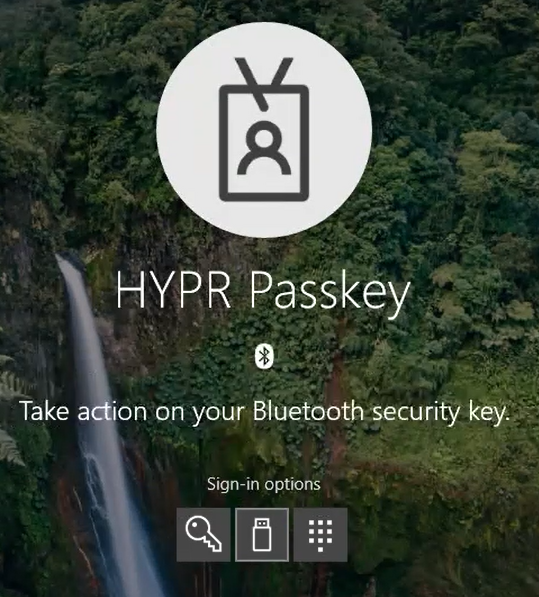
After seeing these notifications, you will continue with the FIDO portion of authentication.
Updated 4 months ago