Integrating with OneLogin
HYPR Control Center Standard: Integrations
Integrating HYPR with OneLogin lets you access your organization’s OneLogin applications using HYPR passwordless authentication instead of the standard username + password login.
Getting the HYPR OneLogin integration up and running requires the following basic steps:
- Understand how the OneLogin login process changes for end users after you integrate with HYPR. See What Will Change in OneLogin?.
- Make sure you have everything you need before starting. See What You'll Need.
- Configure the OneLogin side of the integration. See Setting Up OneLogin.
- Configure the HYPR side of the integration. See Connecting OneLogin to HYPR.
The following HYPR Integration common tasks are explained on the Integrations main page.
- Choose the methods you want people to be able to use for passwordless authentication; see Allowing the Use of FIDO2 Authenticators
- Enabling the Integration
- Enrolling Users
- Monitor integration-specific user activity with the Audit Trail
What Will Change in OneLogin?
Login Flow
Once you activate the HYPR OneLogin integration, users will experience a different OneLogin login flow depending on whether they’re enrolled or non-enrolled.
Enrolled Users
Users who have been successfully enrolled via the HYPR Control Center will no longer need to provide a password to log in to OneLogin. After providing their username on the OneLogin sign in screen, they’ll be redirected to the HYPR passwordless authorization flow. Essentially, HYPR intercepts the default OneLogin login process and replaces the password step with passwordless access.
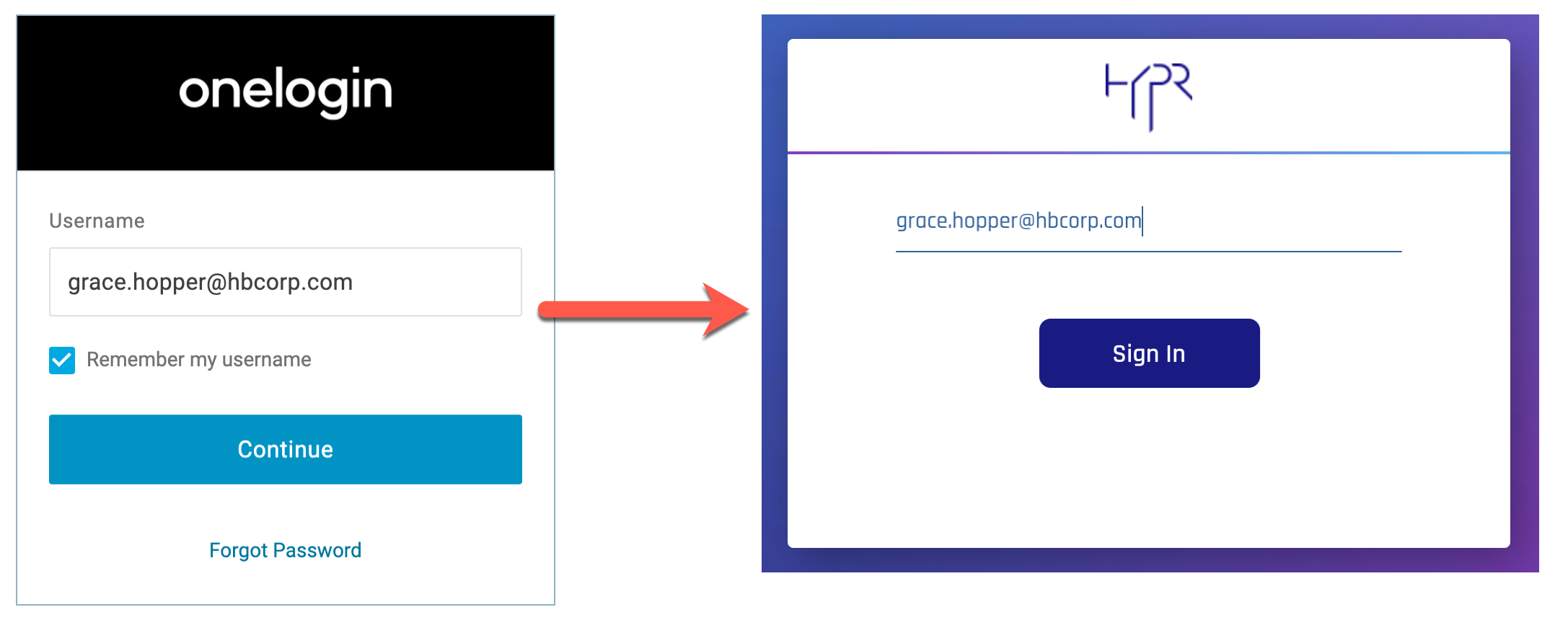
OneLogin Portal
Enrolled users will see a new HYPRDeviceManager application on their OneLogin Portal home page.
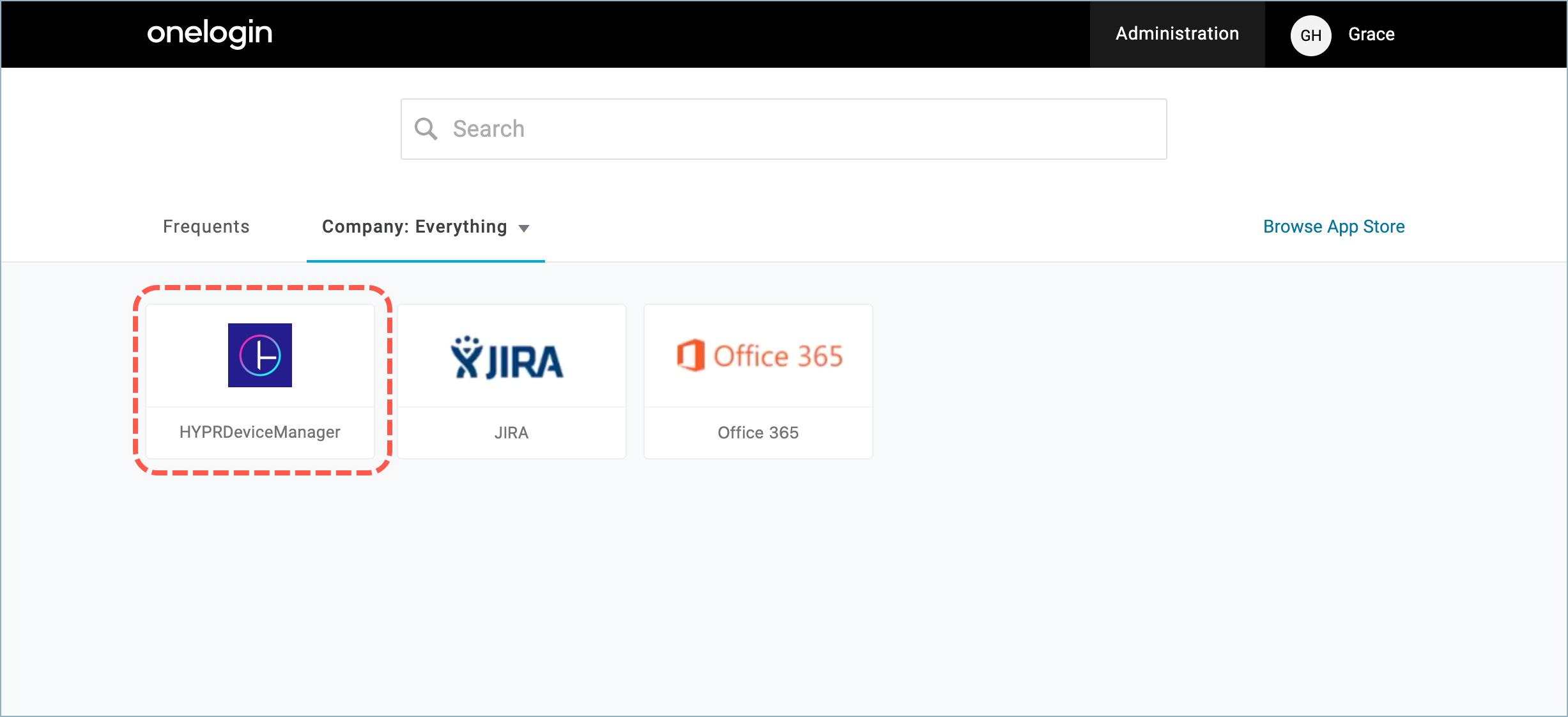
Clicking the application opens the HYPR Device Manager, where the user can add or remove the devices used for authentication.
Non-enrolled Users
Users who have not been enrolled via the HYPR Control Center will be prompted to enter their password to authenticate as usual.

OneLogin Artifacts
As part of the integration with OneLogin, HYPR creates a few artifacts in OneLogin to be able to manage it. Here are the list of artifacts created in OneLogin:
- OneLogin Application: HYPR Device Manager, an OIDC application allowing users to manage their paired devices.
- OneLogin Role: A role connected to the application to allow to connect between users and the application. When a user adds a device to HYPR, the user will be added to the role and will be able to see the Device Manager in OneLogin. This is important especially when the integration is not live to allow the user access to the device manager from OneLogin.
- OneLogin Mapping: A rule that connects between the users, the role, and the trusted IdP. The mapping will be enabled when the HYPR integration is enabled, and disabled when when HYPR integration is disabled.
- User Trusted IdP setup: Connects the user and HYPR. HYPR will assign the Trusted IdP to the user upon being added to the integration.
What You'll Need
HYPR Control Center Account
Since you’re setting up the HYPR OneLogin integration through the HYPR Control Center, you should have already registered for an account, paired your mobile device with HYPR, and used your new passwordless login to access the Control Center. If this isn’t the case, please contact us at [email protected] and we’ll help you out.
OneLogin Account
You must already have OneLogin set up and active for your organization before you start the integration. Most of the HYPR OneLogin integration is automated but you’ll need to log in to the OneLogin Admin console in order to complete the process.
Keycloak Realm and Client Names
To configure the OneLogin Integration, the following Keycloak Realm and Client Name format must be used:
<app_name>= the OneLogin Application Name used in the HYPR Integration, which must also be the Trusted IdP name from OneLogin- In this article, the
<app_name>will be HYPROneLogin - Keycloak Realm =
onelogin_<app_name>all lower case, without spaces - Client Name =
onelogin_<app_name>_clientall lower case, without spaces
Please use these names when you follow the steps in this document to setup OneLogin.
Users that already have an existing OneLogin integration will have to go back to the Trusted IdP setup in OneLogin and change those names in both the URLs and the client name.
Setting Up OneLogin
Generating the OneLogin API Credentials
As part of the connection setup process, you’ll need to provide a OneLogin API client/secret credential pair so HYPR can generate the necessary tokens to access your OneLogin account. See Working with API Credentials in the OneLogin documentation for more information.
You can generate the credentials as follows:
- Login to the OneLogin Admin console
- Select Developers > API Credentials, then click New Credential.
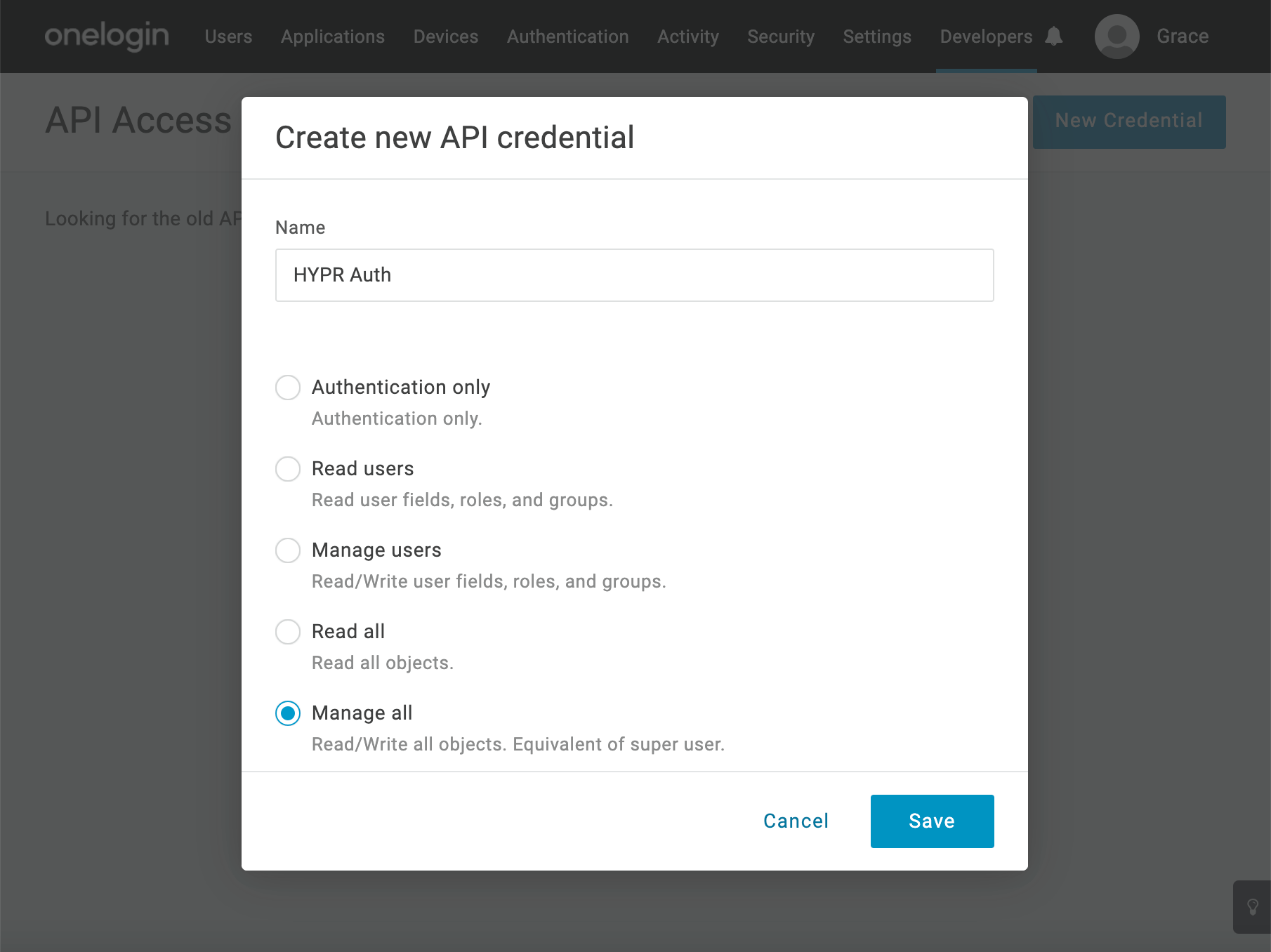
- Give the credential a Name, select the Manage All option, then click Save.
- From the resulting window, note the Client ID and Client Secret , which you’ll need later when configuring the integration in the HYPR Control Center. You can always check them by opening OneLogin to view the credentials you created.
Creating a OneLogin Trusted IdP
- In the OneLogin Admin console, select Authentication > Trusted IdPs, then click New Trust.
- Name the Trusted IdP. Make a note of the name for later.
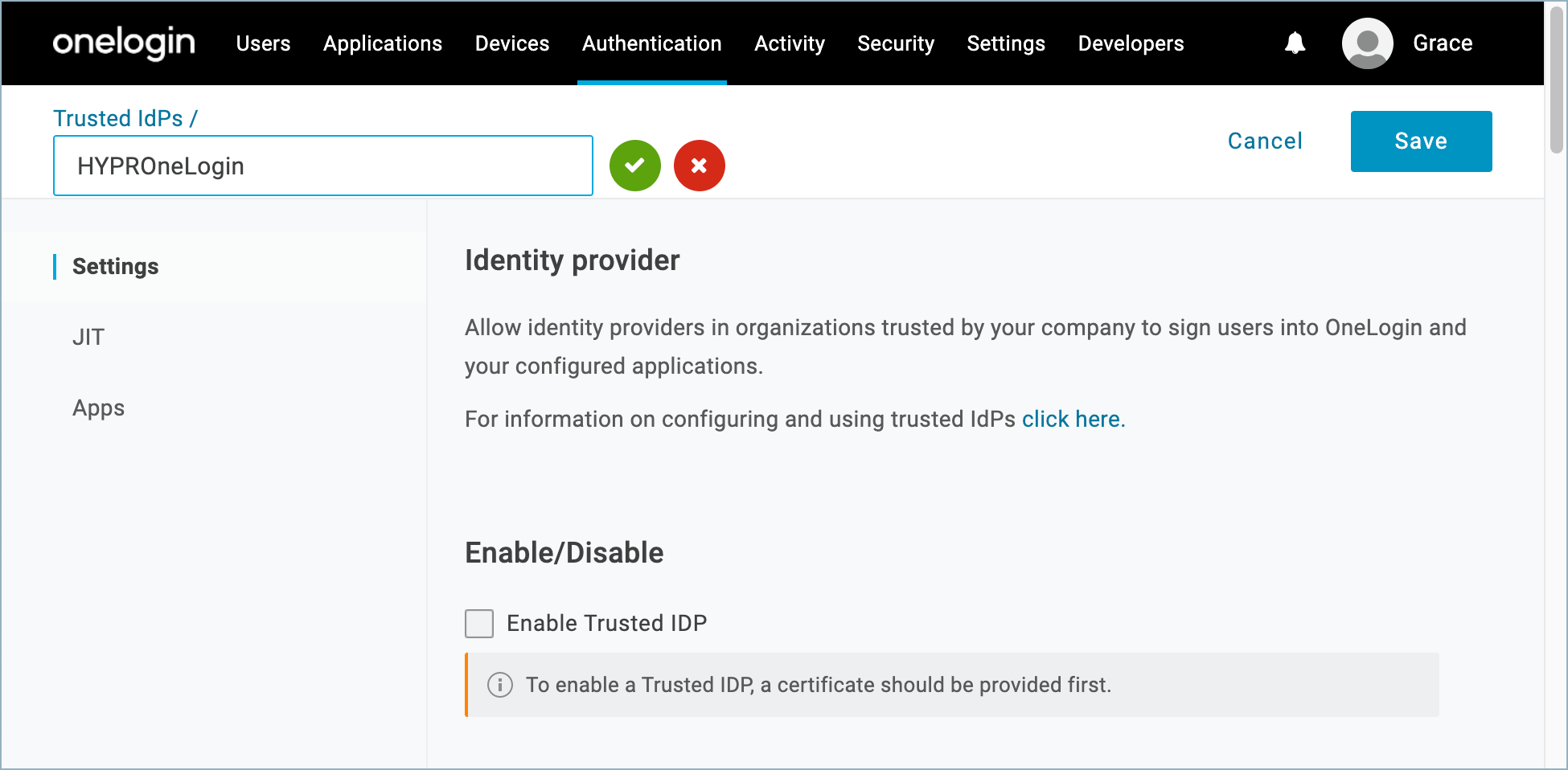
Keep It Safe
You’ll need to use the same name when you configure the integration in the HYPR Control Center and it will subsequently be visible to your end users in several places. See Connecting OneLogin to HYPR for more information.
- Populate the Configurations section as follows:
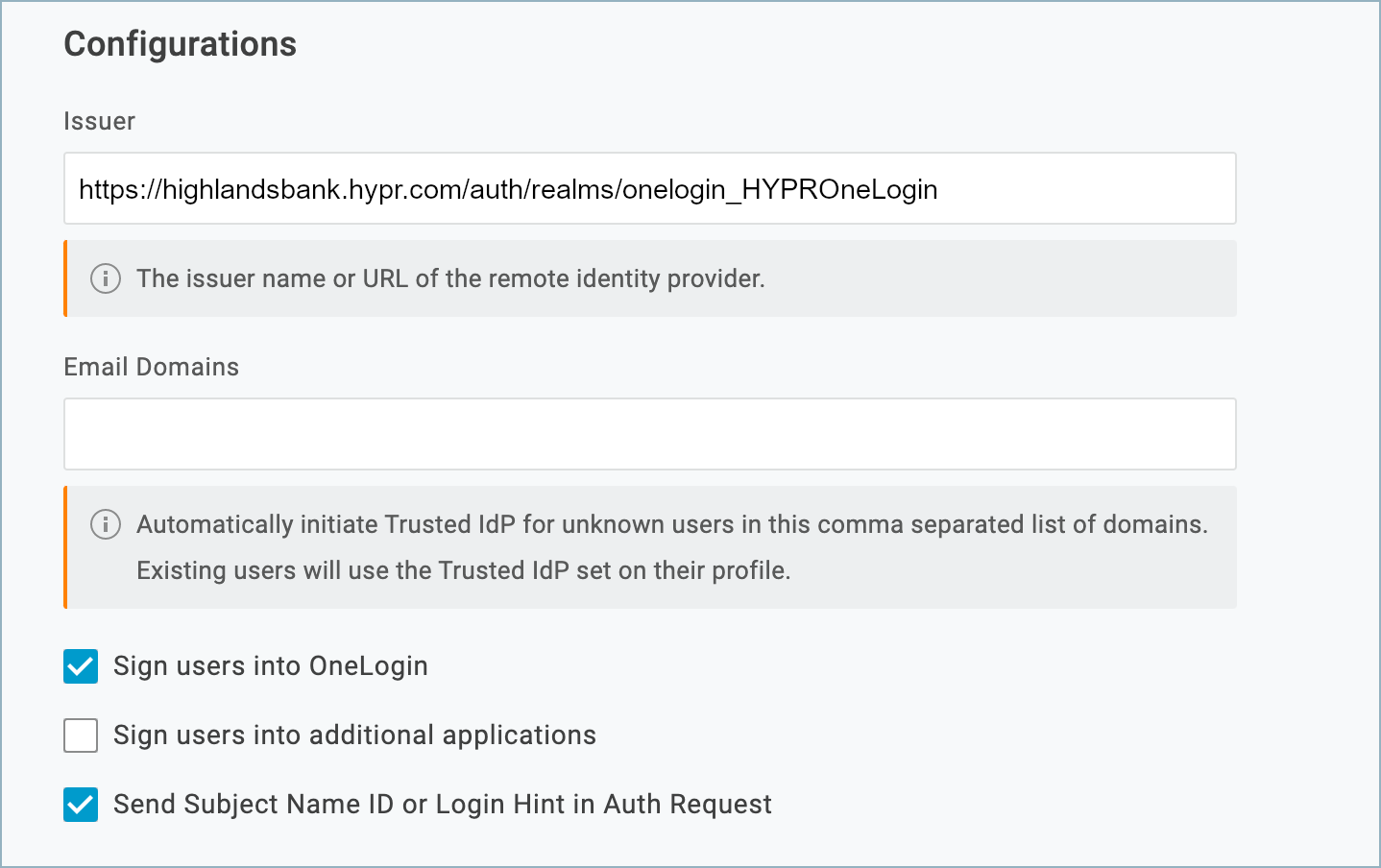
| Parameter | Value |
|---|---|
| Issuer | https://<hypr_tenant>.hypr.com/auth/realms/onelogin_<app_name>Replace <mydomain> with the base domain of your HYPR Control Center instance. For example:https://highlandsbank.hypr.com/auth/realms/onelogin_HYPROneLogin |
| Sign users into OneLogin | Checked |
| Sign users into additional applications | Unchecked |
| Send Subject Name ID or Login Hint in Auth Request | Checked |
- In the Protocol section, set the Protocol Type to OIDC.
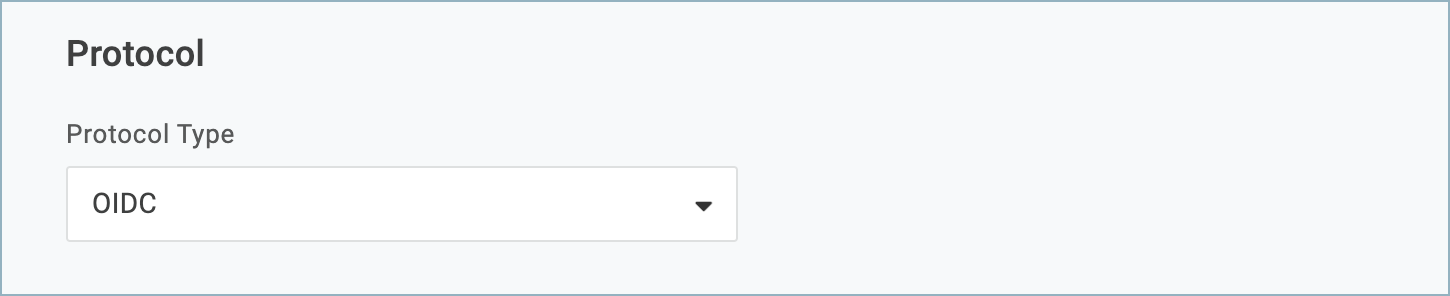
- Populate the OIDC Configurations section as follows:
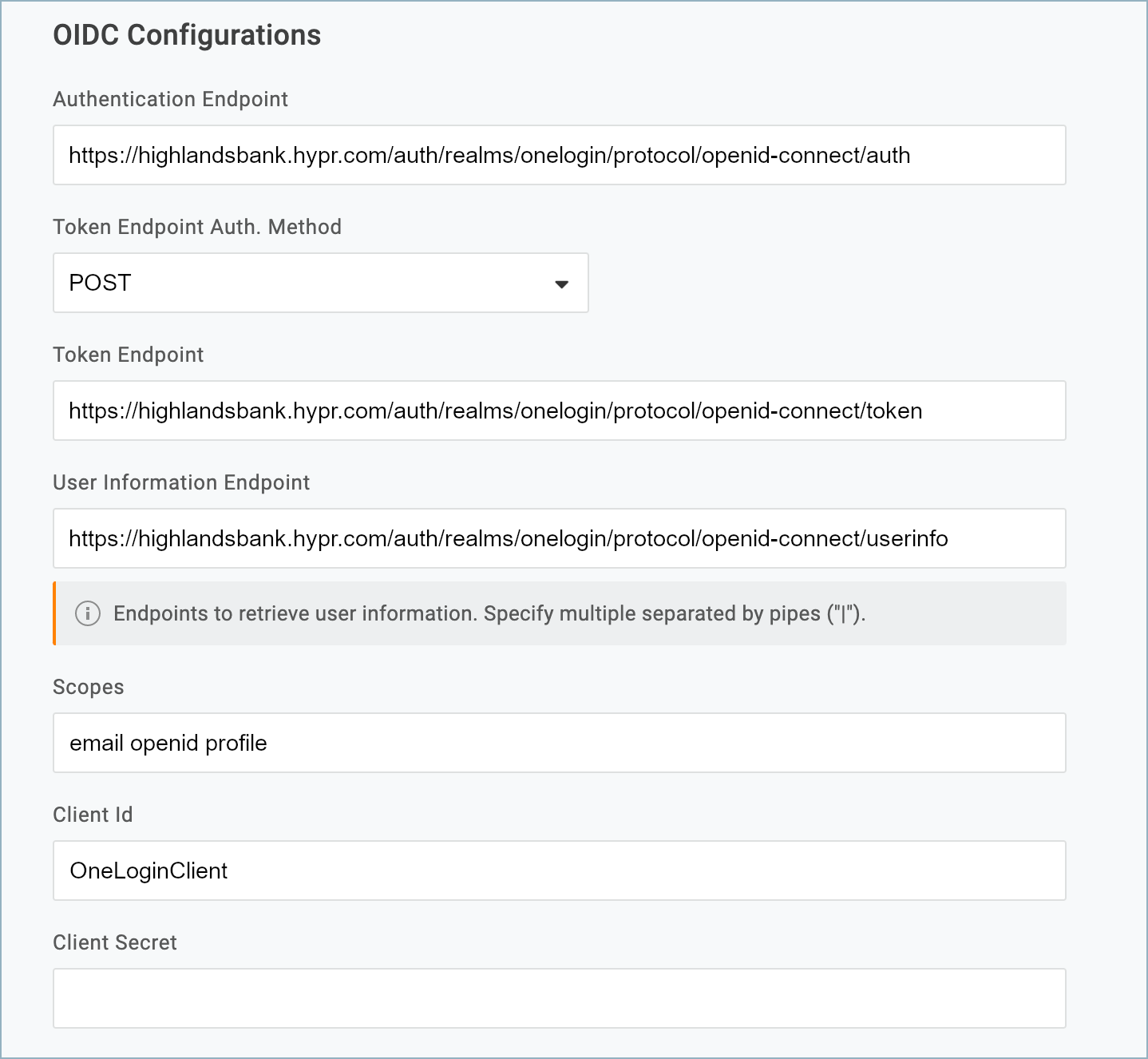
| Parameter | Value |
|---|---|
| Authentication Endpoint | https://<hypr_tenant>.hypr.com/auth/realms/onelogin_<app_name>/protocol/openid-connect/auth |
| Token Endpoint Auth. Method | POST |
| Token Endpoint | https://<hypr_tenant>.hypr.com/auth/realms/onelogin_<app_name>/protocol/openid-connect/token |
| User Information Endpoint | https://<hypr_tenant>.hypr.com/auth/realms/onelogin_<app_name>/protocol/openid-connect/userinfo |
| Scopes | email openid profile |
| Client Id | OneLoginClient |
| Client Secret | Leave empty for right now. You’ll get this from the HYPR Control Center later. |
- Click Save to create the Trusted IdP.
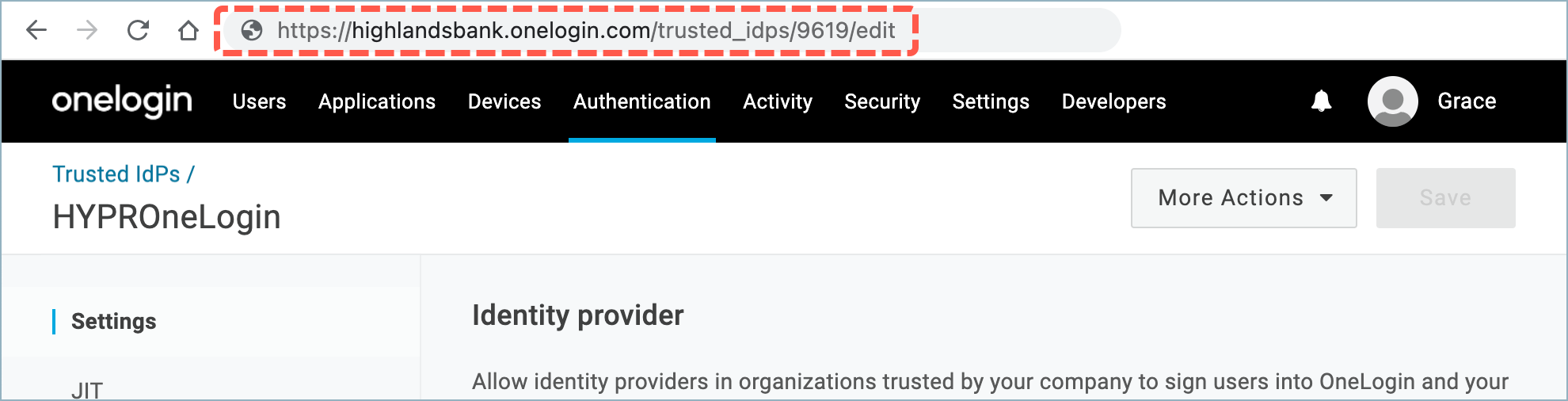
- Click the newly created Trusted IdP to re-open it for editing and make a note of the ID from the URL. For example, in this case the ID is 9619:
Connecting OneLogin to HYPR
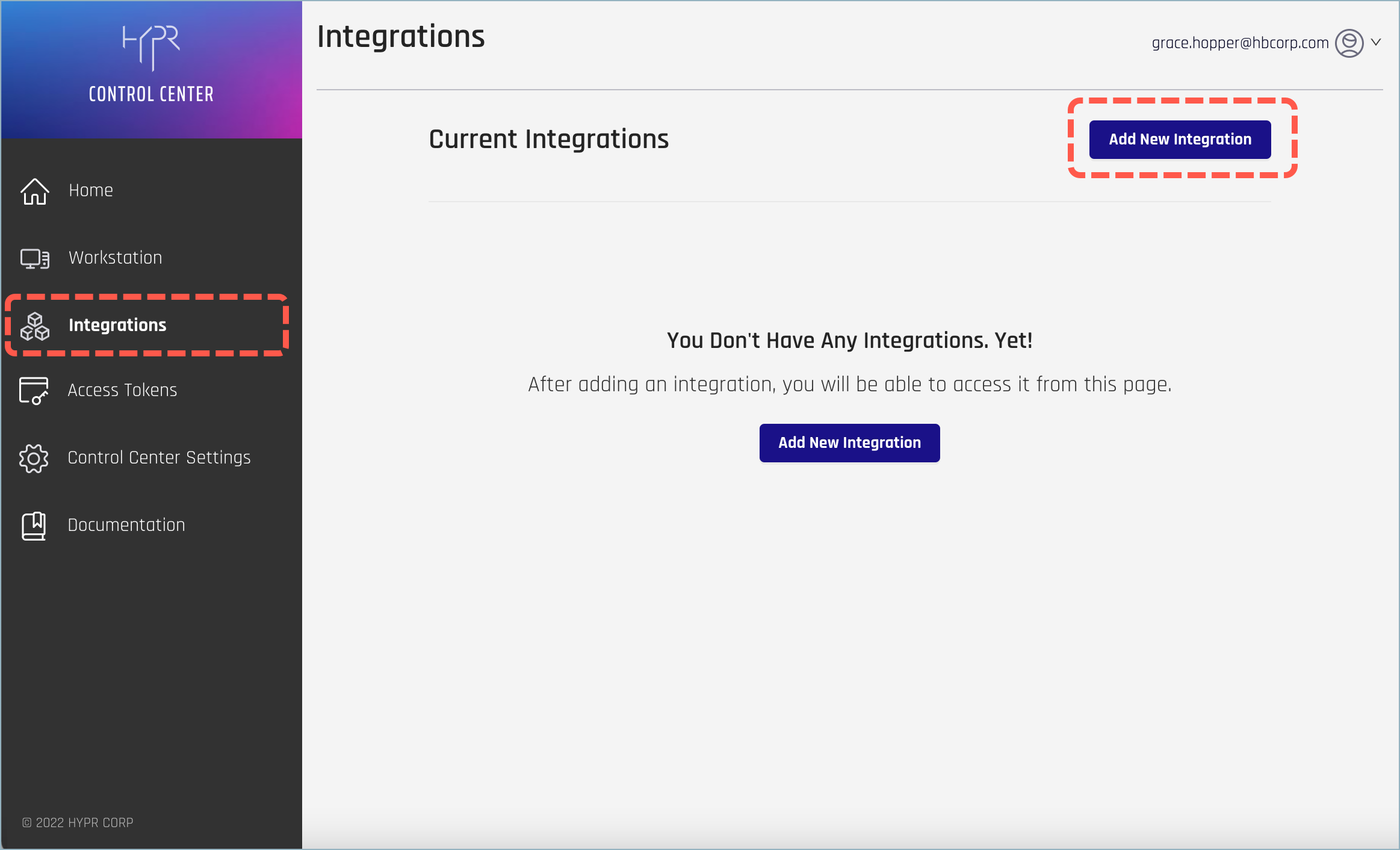
- Open Control Center and select Integrations. At right, click Add New Integration to show a list of available integration types.
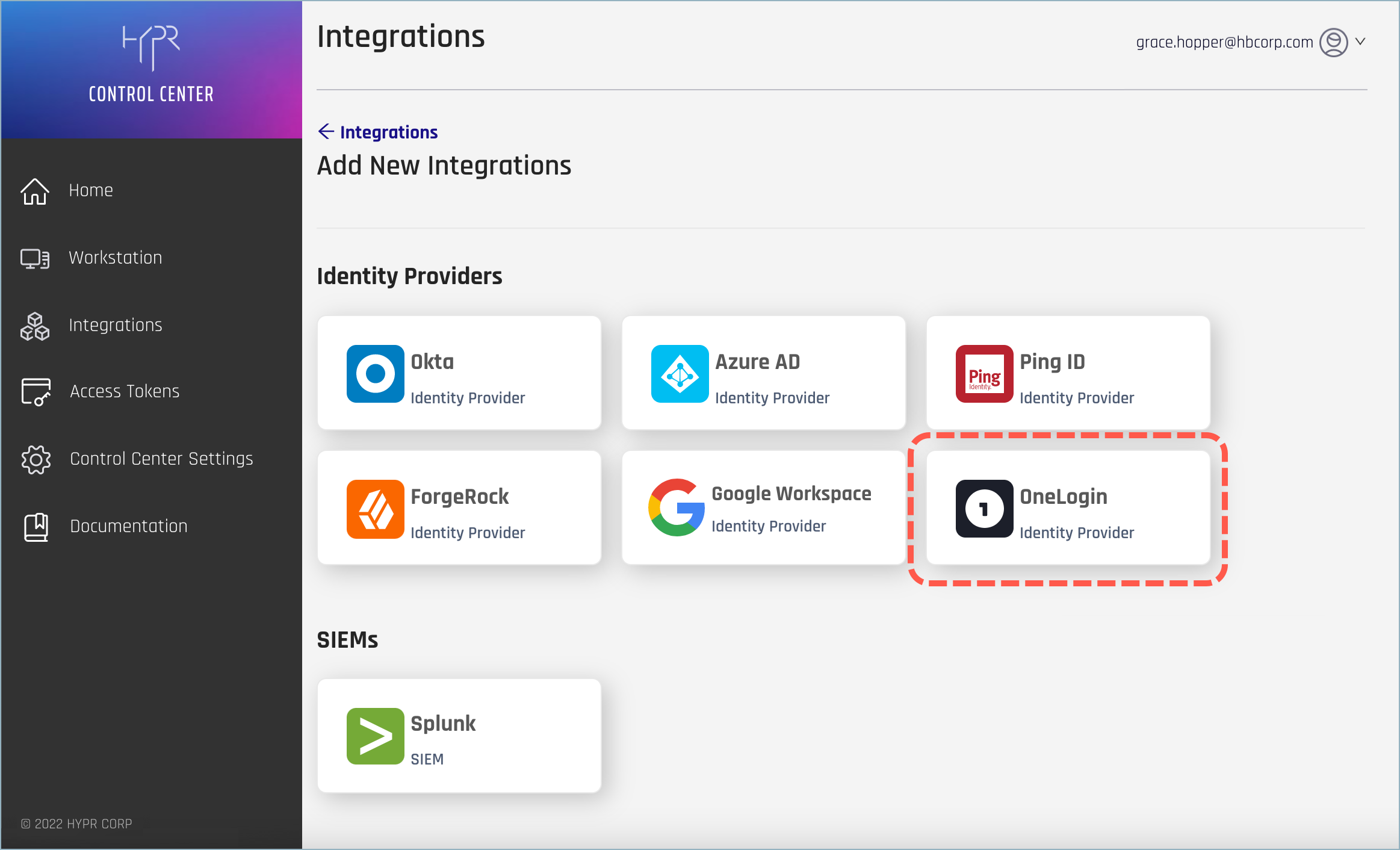
- Select the OneLogin Identity Provider integration.
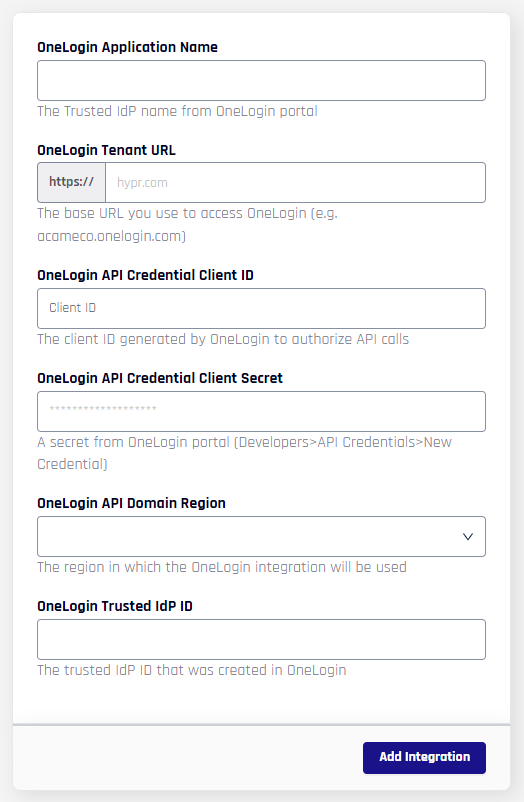
- Provide the following OneLogin information on the Integrations screen.
| Field | Value |
|---|---|
| OneLogin Application Name | The name of the Trusted IdP you created in OneLogin. See Creating a OneLogin Trusted IdP. For example:HYPROneLoginHYPR will use this name in three places: - For the web account name that users will see in the HYPR Mobile App - For the HYPR Device Manager page where users register their devices - For internal identification of this integration within the HYPR platform Note that spaces will be stripped from the name when it’s used to internally identify the integration within the HYPR platform. The namespace is limited to 23 characters. You can’t change this name after you add the integration. |
| OneLogin Tenant URL | The base URL you use to access OneLogin. For example:highlandsbank.onelogin.com |
| OneLogin API Credential Client ID | The Client ID for the credential pair you created in OneLogin. See Generating the OneLogin API Credentials. |
| OneLogin API Credential Client Secret | The Client Secret for the credential pair you created in OneLogin. See Generating the OneLogin API Credentials. |
| OneLogin API Domain Region | The region where you’ll be using this integration (US or EU). |
| OneLogin Trusted IdP ID | The Trusted IdP ID you created in OneLogin. See Creating a OneLogin Trusted IdP. For example:9619 |
- Click Add Integration to begin. If the action is successful, you’ll see the Integration Added confirmation dialog.
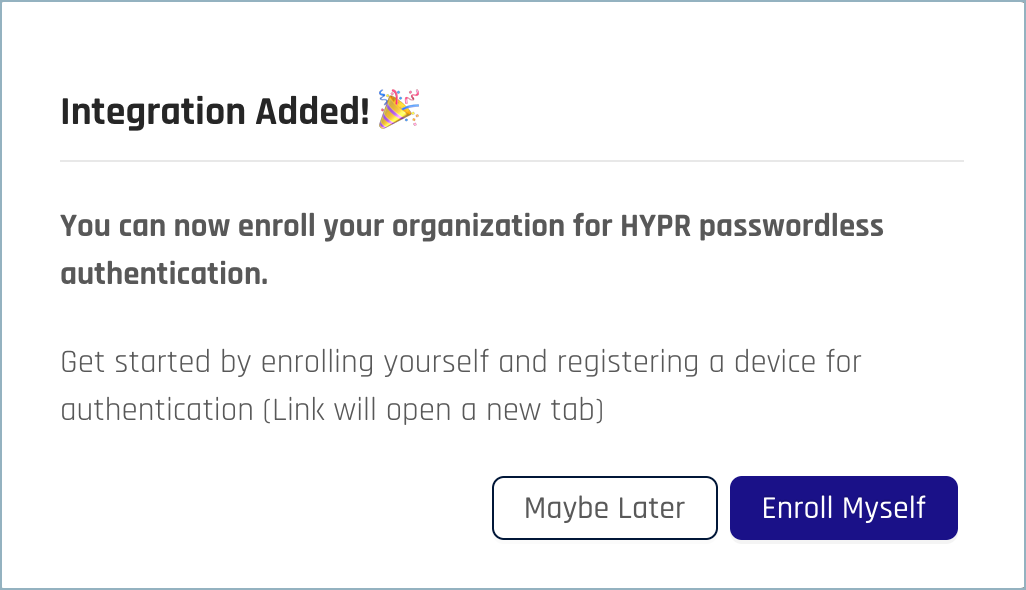
- You can optionally now register to use HYPR OneLogin passwordless SSO yourself by clicking Enroll Myself. You’ll be taken to the HYPR Device Manager where you can register your mobile device.
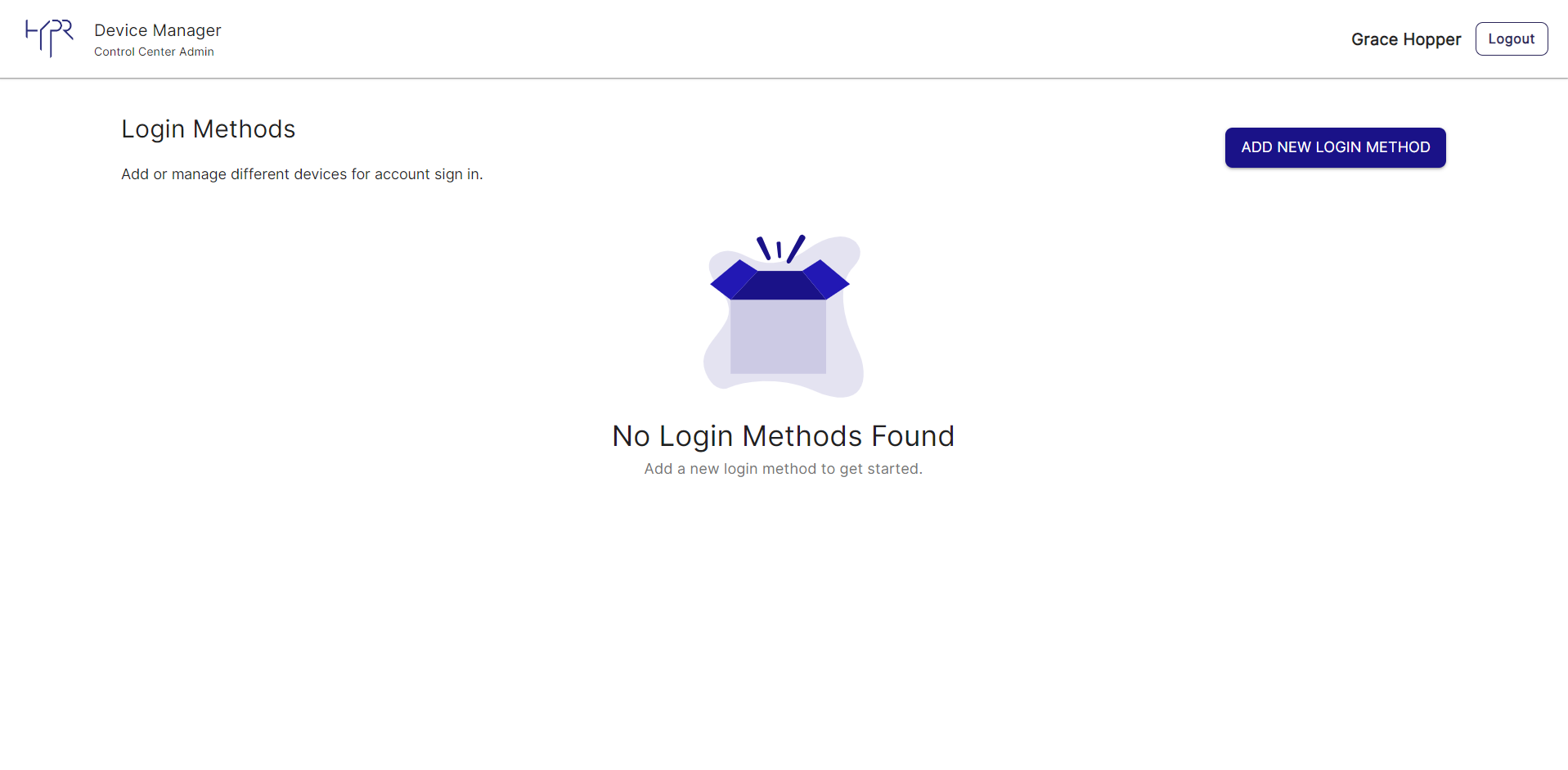
NOTE
The Enroll Myself option is only available if your OneLogin username is the same as your HYPR Control Center username. If not, you can add yourself as a regular user later. See Enrolling Users.
Once you’ve registered a device, you’ll see your username in the list of enrolled users.
Enable the OneLogin Trusted IdP
After you’ve added the integration in the HYPR Control Center, you’ll need to add the HYPR-generated Client Secret to the Trusted IdP you created in OneLogin.
- On the Integration Settings tab for the OneLogin integration, copy the Client Secret for OneLogin Trusted IdP value.
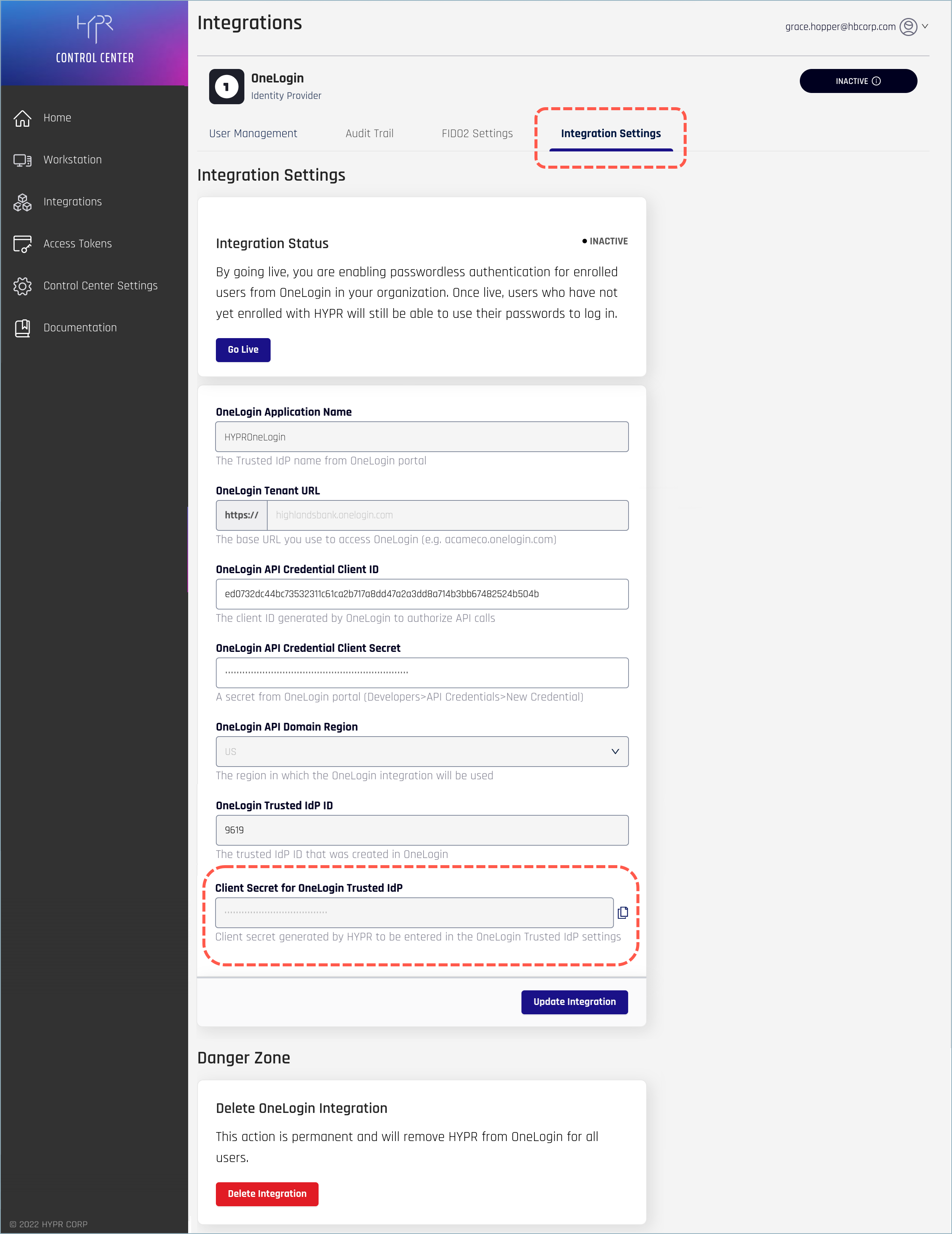
- In the OneLogin Admin console, go to Authentication > Trusted IdPs and open the Trusted IdP you created earlier.
- In the Enable/Disable section, turn on Enable Trusted IDP.
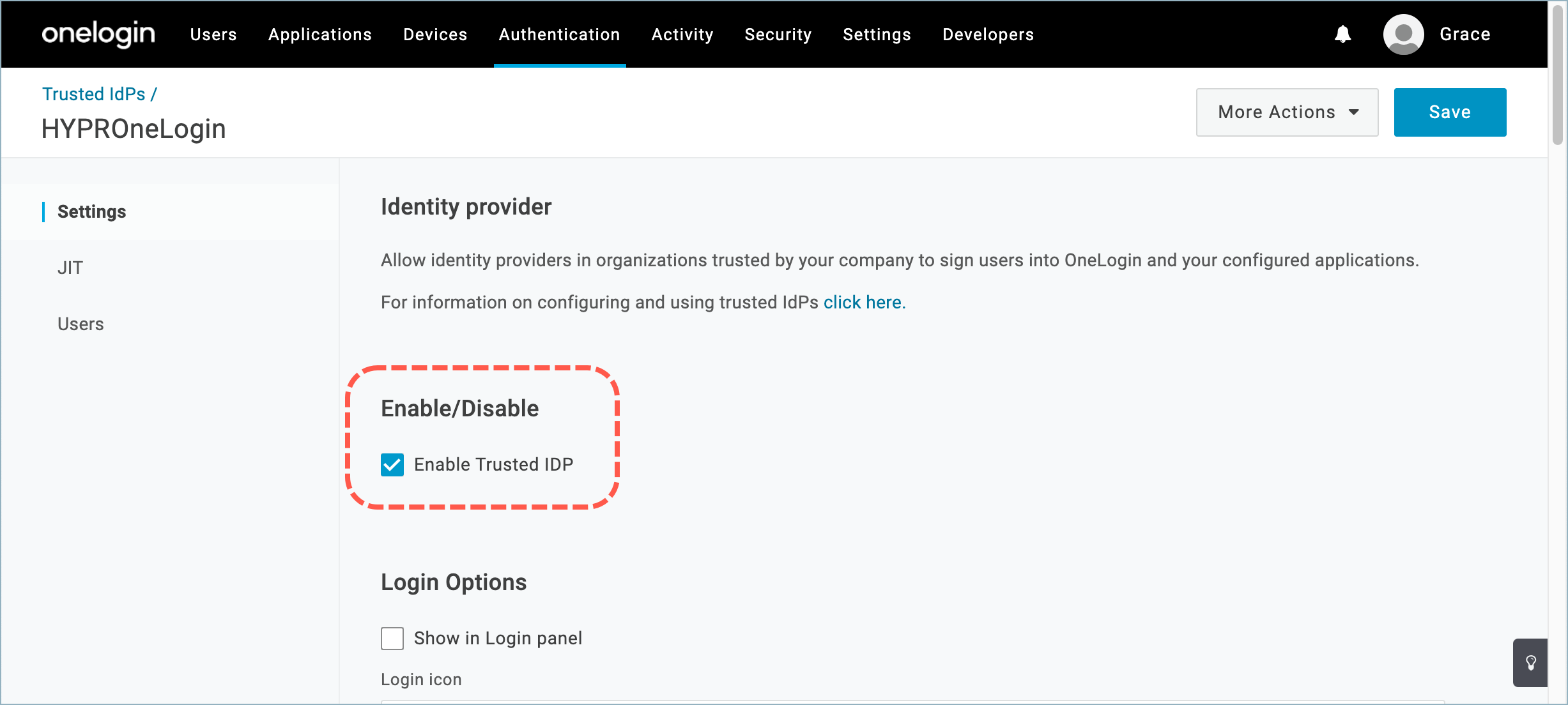
- In the OIDC Configurations section, paste the copied value into the Client Secret field, at the bottom.
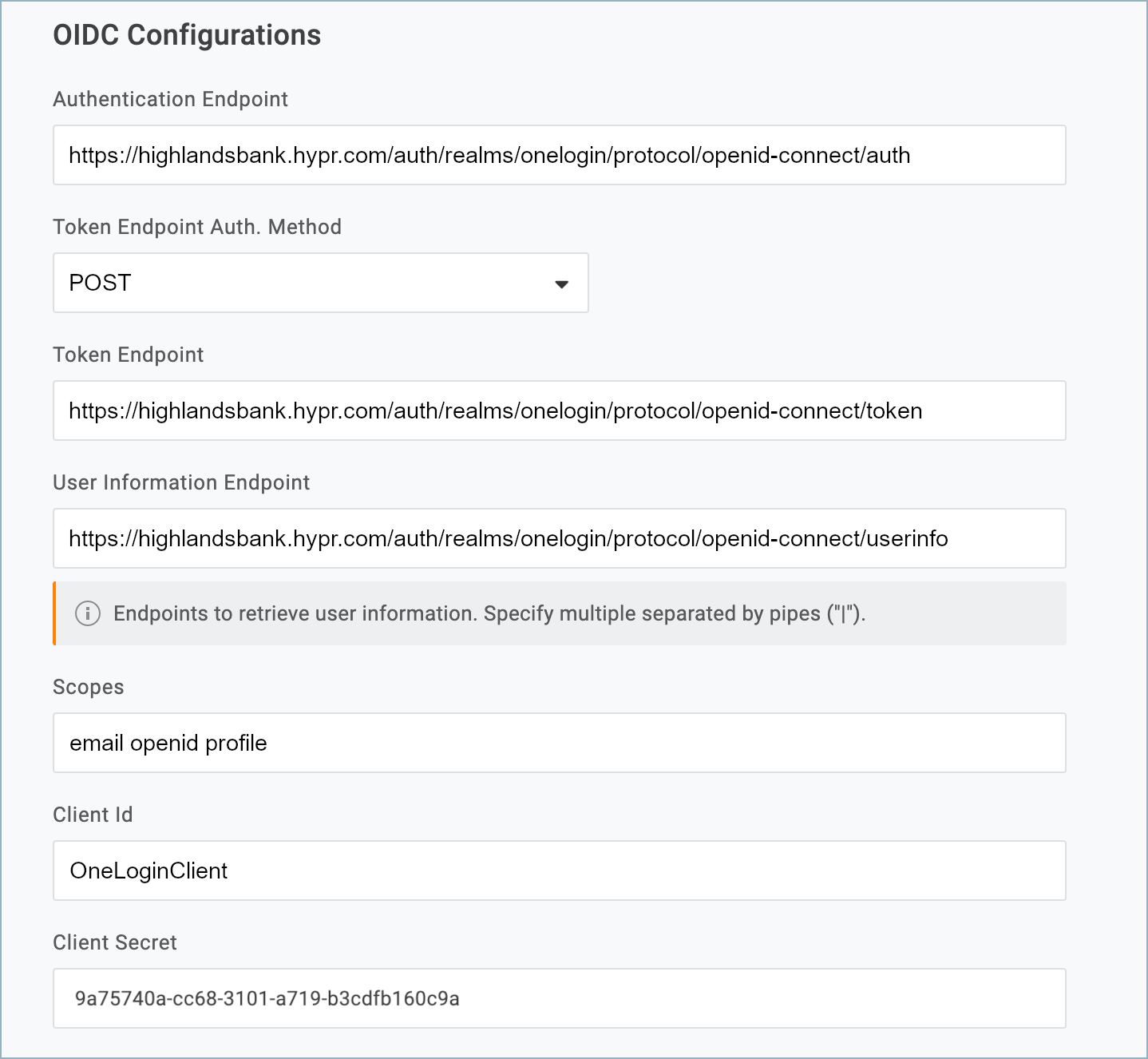
- Click Save to apply the changes.
What Happens behind the Scenes?
When you create/activate the HYPR OneLogin integration, HYPR will handle the back-end configuration for you by adding or modifying the following elements in OneLogin:
HYPRDeviceManager OIDC Application
Settings for the HYPR Device Manager application that is created and assigned to each enrolled user’s OneLogin Portal home page. See What Will Change in OneLogin?.
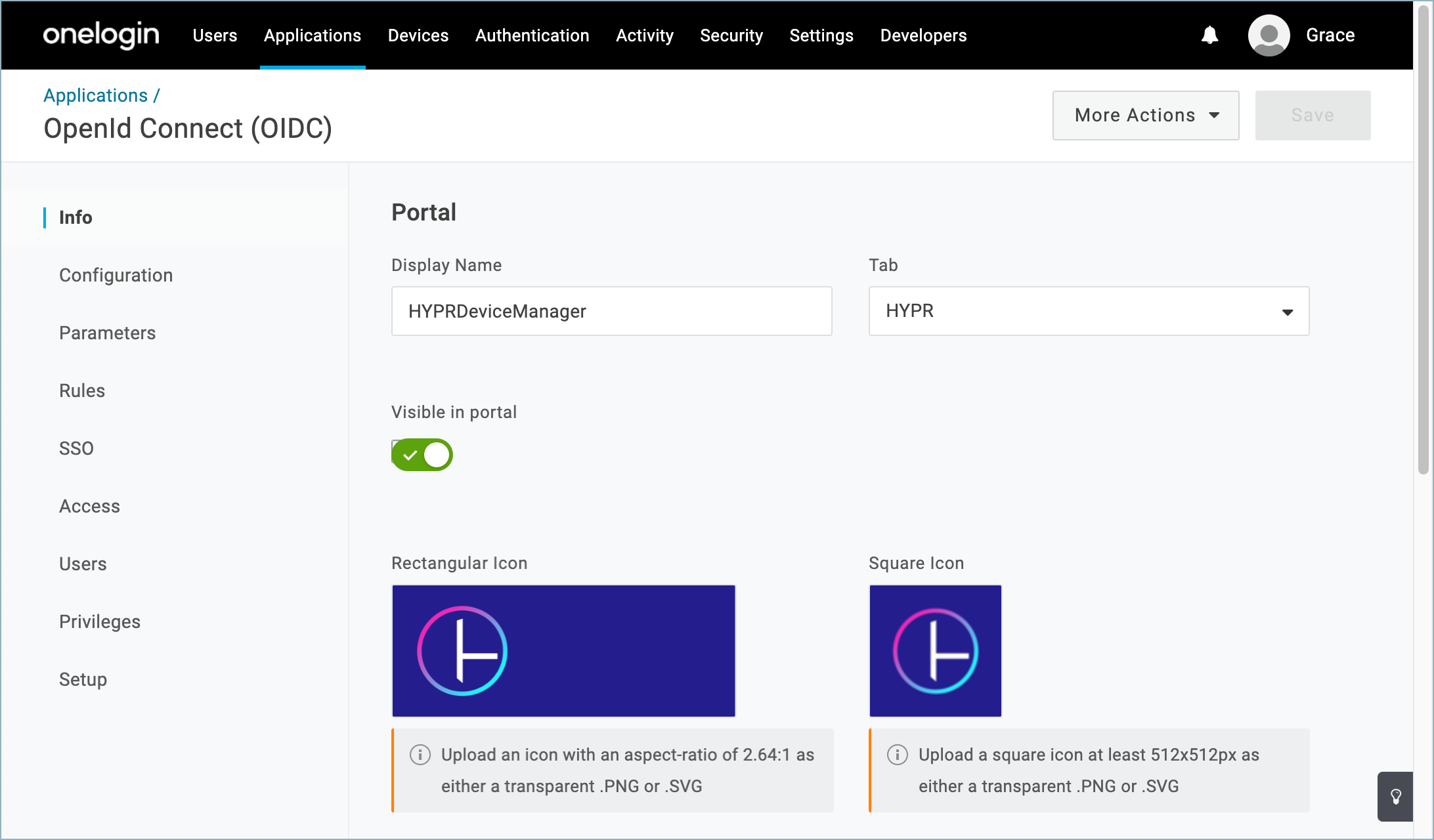
Iconography
The integration isn’t able to set the application icons automatically. However, you can download a visual asset library from HYPR Support that includes some suitable images.
HYPRDeviceManagerRole
A OneLogin role to connect enrolled users to the HYPR Device Manager application.
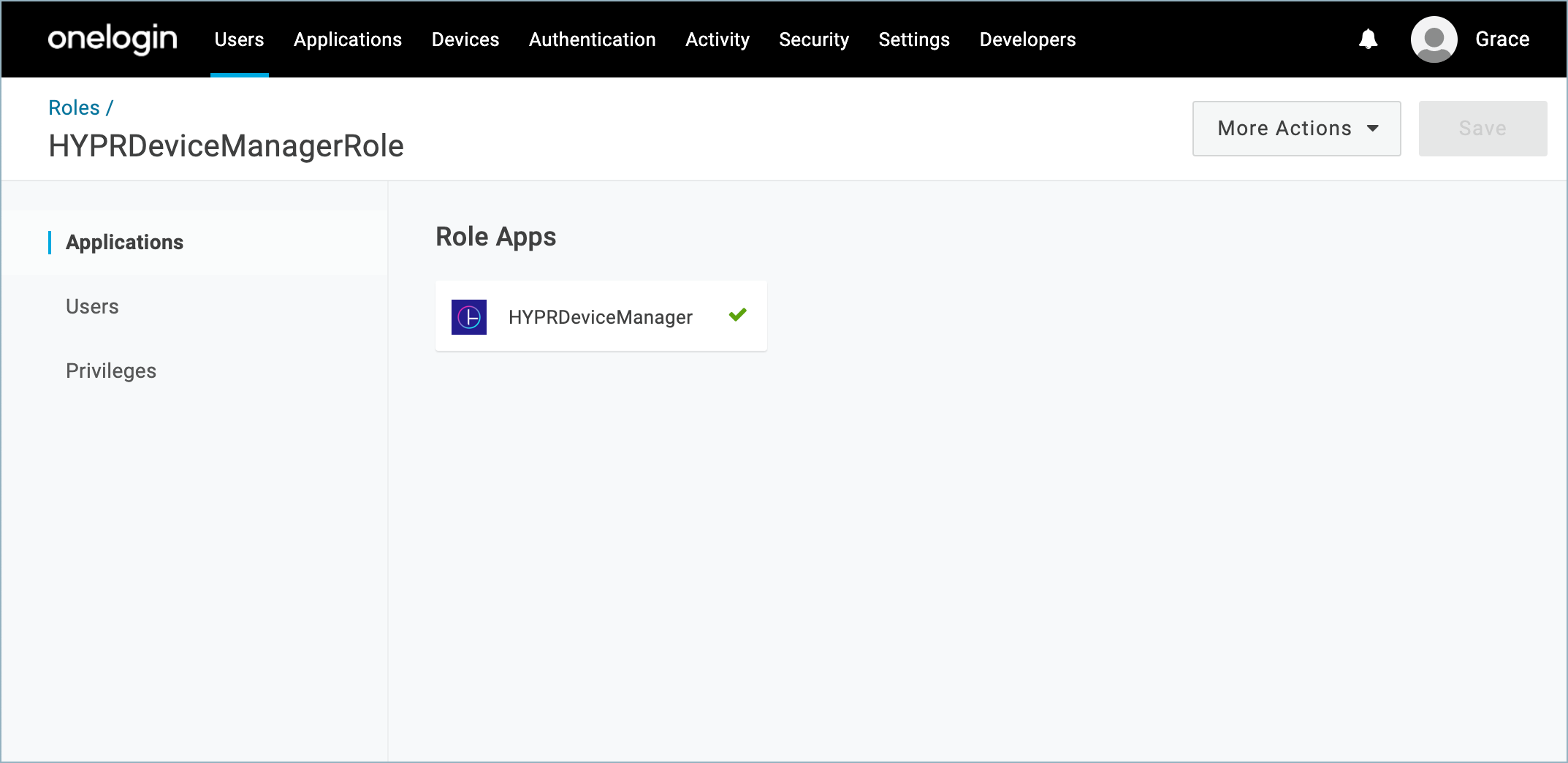
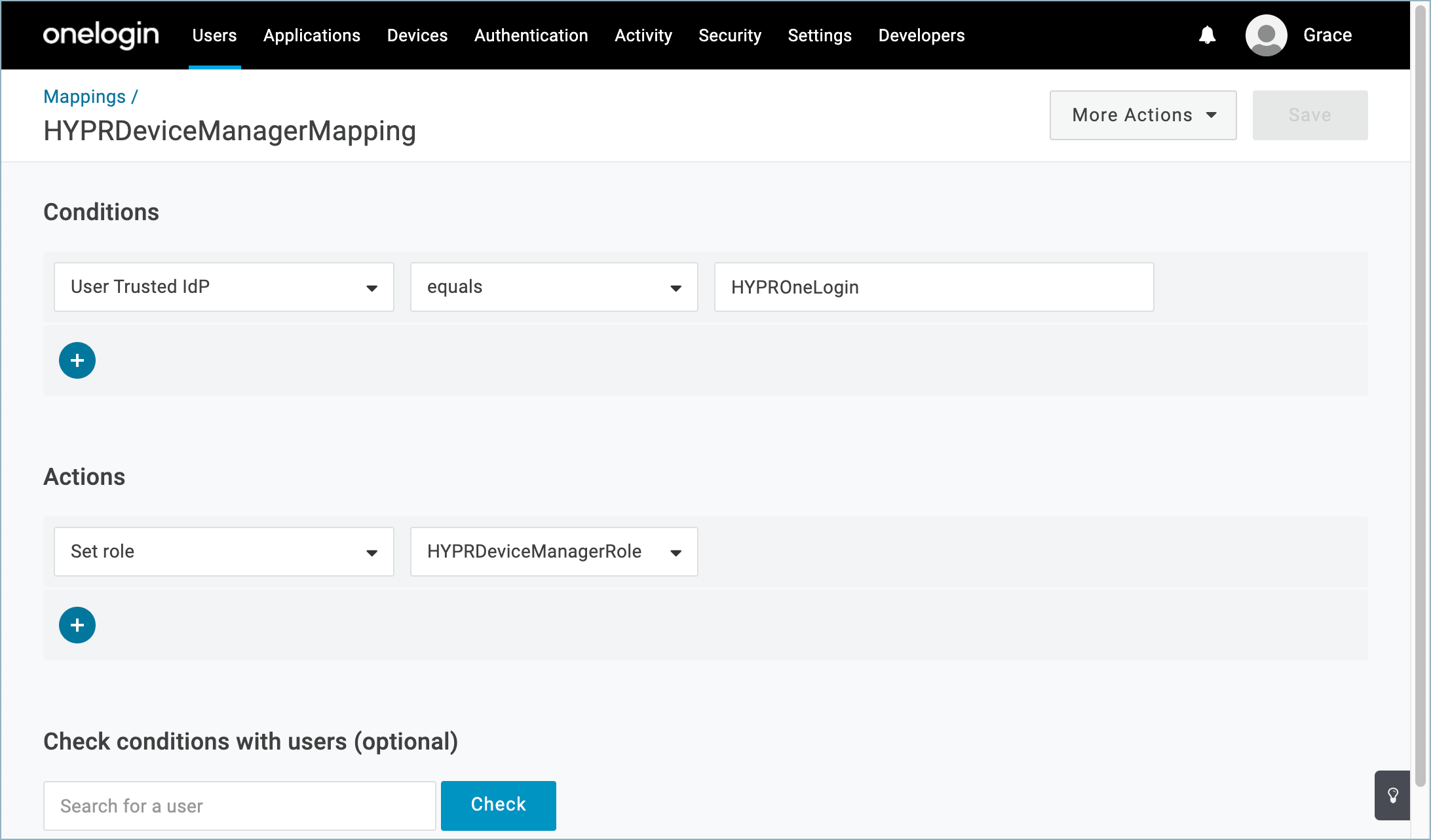
HYPRDeviceManagerMapping
A OneLogin mapping rule to connect users, the role, and the Trusted IdP. This mapping will be automatically enabled when you activate the HYPR OneLogin integration through the HYPR Control Center and disabled when the integration is disabled. See the main Integrations article for Enabling the Integration and Disabling the Integration.
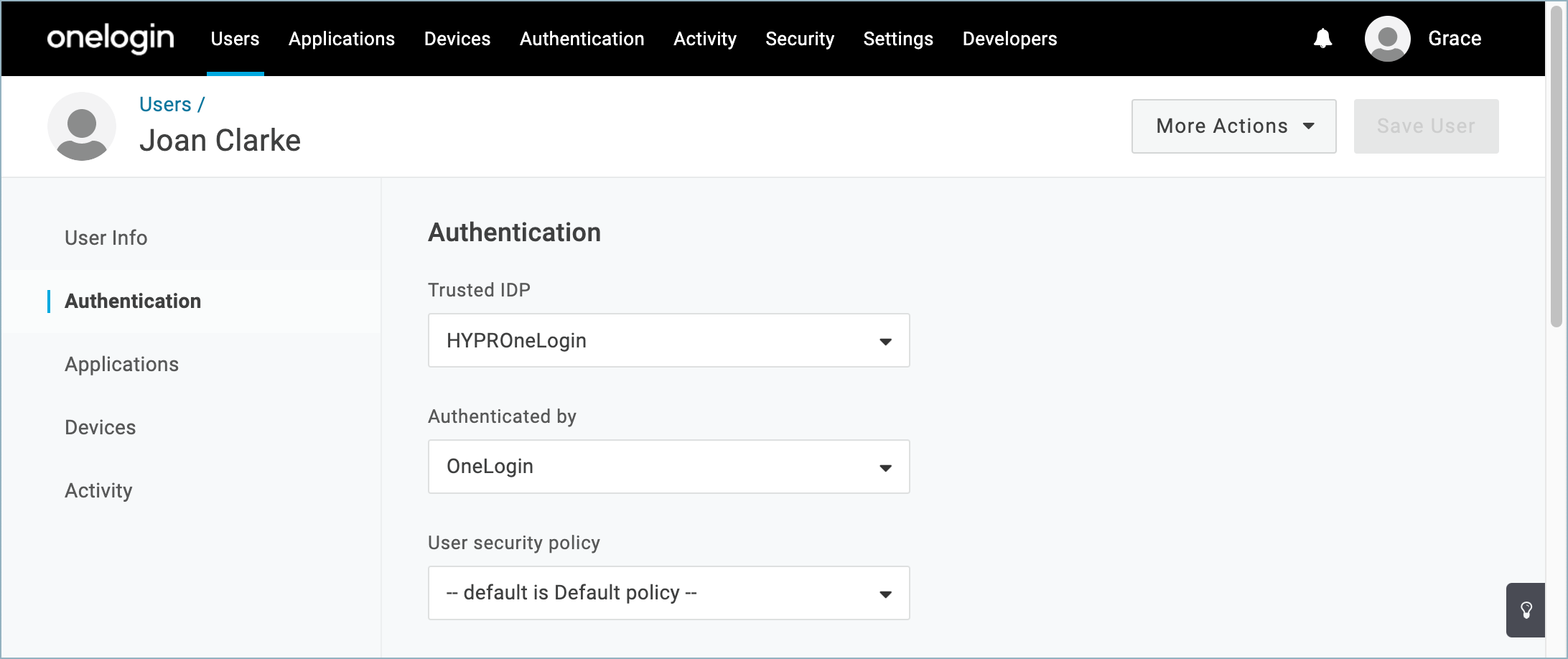
User Authentication
When you enroll users into the HYPR OneLogin integration, their Authentication settings are automatically updated in OneLogin.
Enable, Enroll, and Audit
Continue with the HYPR Integrations common UI experience in the Integrations main page to complete Enabling your integration, enrolling users, and monitoring activity with the integration's Audit Trail.
Updated 4 months ago
