Event Hook: Splunk
HYPR Control Center Standard: Integrations
Adding Splunk event hooks allows HYPR-enabled sites to gather and interpret HYPR Events using their own Splunk installation, rather than using HYPR's. By adding an HTTP Event Collector in Splunk and using its API key to enable HYPR CC's connection, you are able to tailor the output to best suit your needs.
HYPR Events are grouped using the eventTags parameter (AUTHENTICATION, REGISTRATION, ACCESS TOKEN, etc.). Custom Event Hooks can also be created for more specific data.
What You'll Need
- An administrator account for Splunk
- An administrator account for Control Center
- If it is not already enabled, contact HYPR Support to enable Splunk Event Hooks for the RP application that you wish to monitor
Setting Up Splunk
Splunk must be configured with an HTTP Event Collector that will communicate with Control Center.
-
Login as an administrator to the Splunk Cloud console.
-
In the top menu, open Settings -> Source types under the DATA subheading.
-
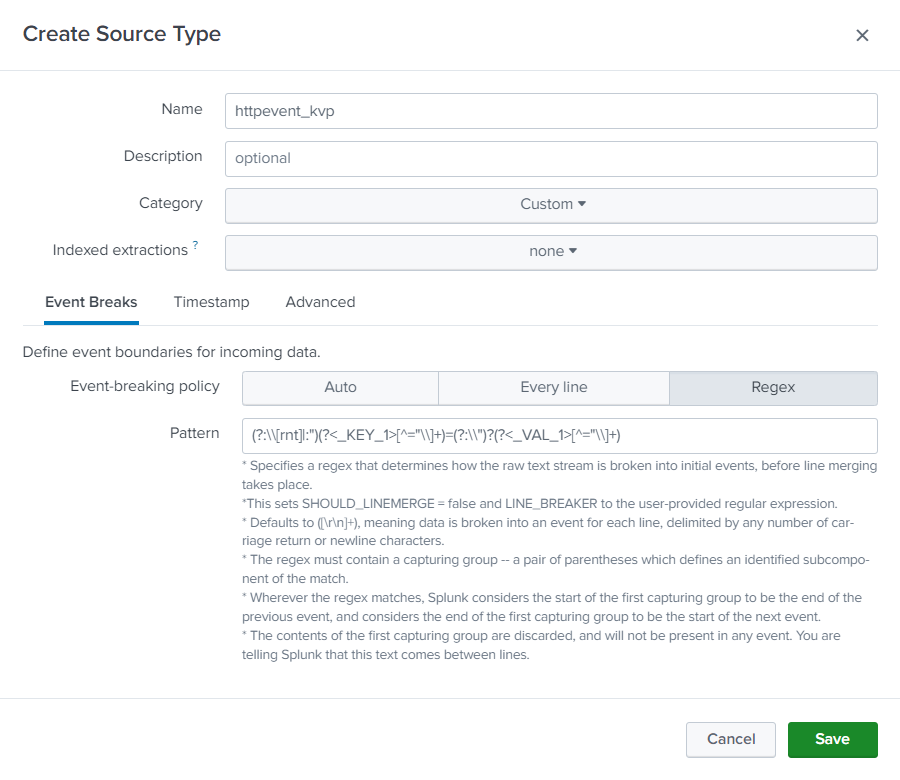
In the Source Types pane, click Create Source Type. Complete the fields as shown in the table below, then click Save when finished.
Field Value Name In this example is it httpevent_kvp, but it can be anything descriptive. Description (optional) Category Custom Indexed extractions none Event Breaks: Event-breaking policy Regex Pattern (?:\[rnt]|:")(?<_KEY_1>[^="\]+)=(?:\")?(?<_VAL_1>[^="\]+) Timestamp (not used) Advanced (not used)
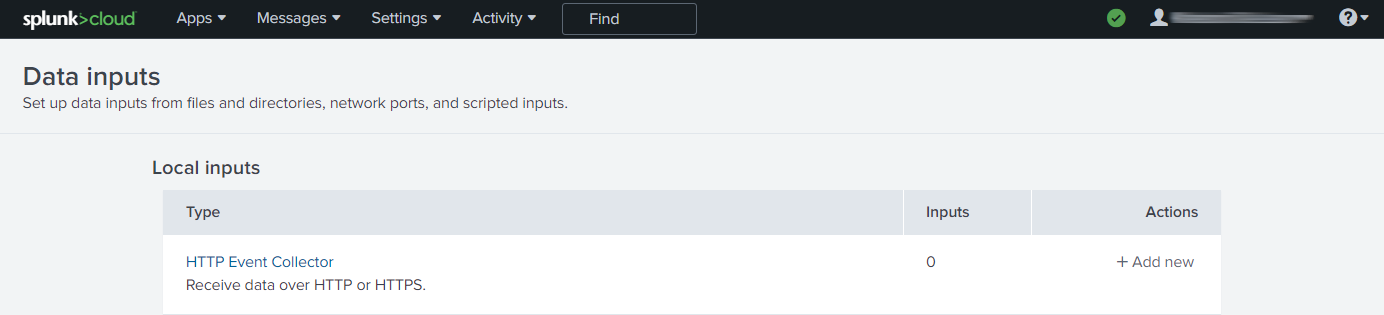
- In the top menu, open Settings -> Data Inputs under the DATA subheading.
- In the Data Inputs pane, click HTTP Event Collector.
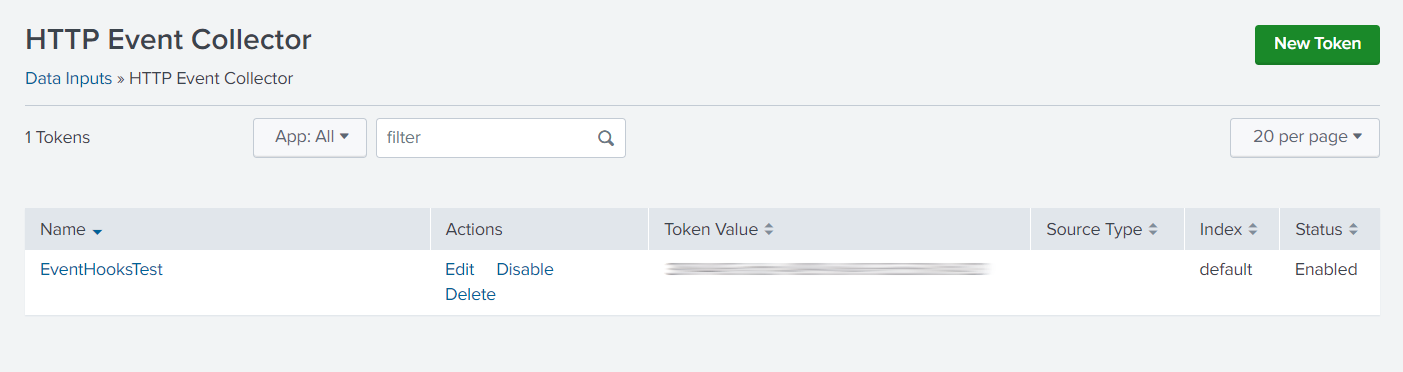
- In the upper right of the HTTP Event Collector pane, click New Token.
- Name your token, then click Next.
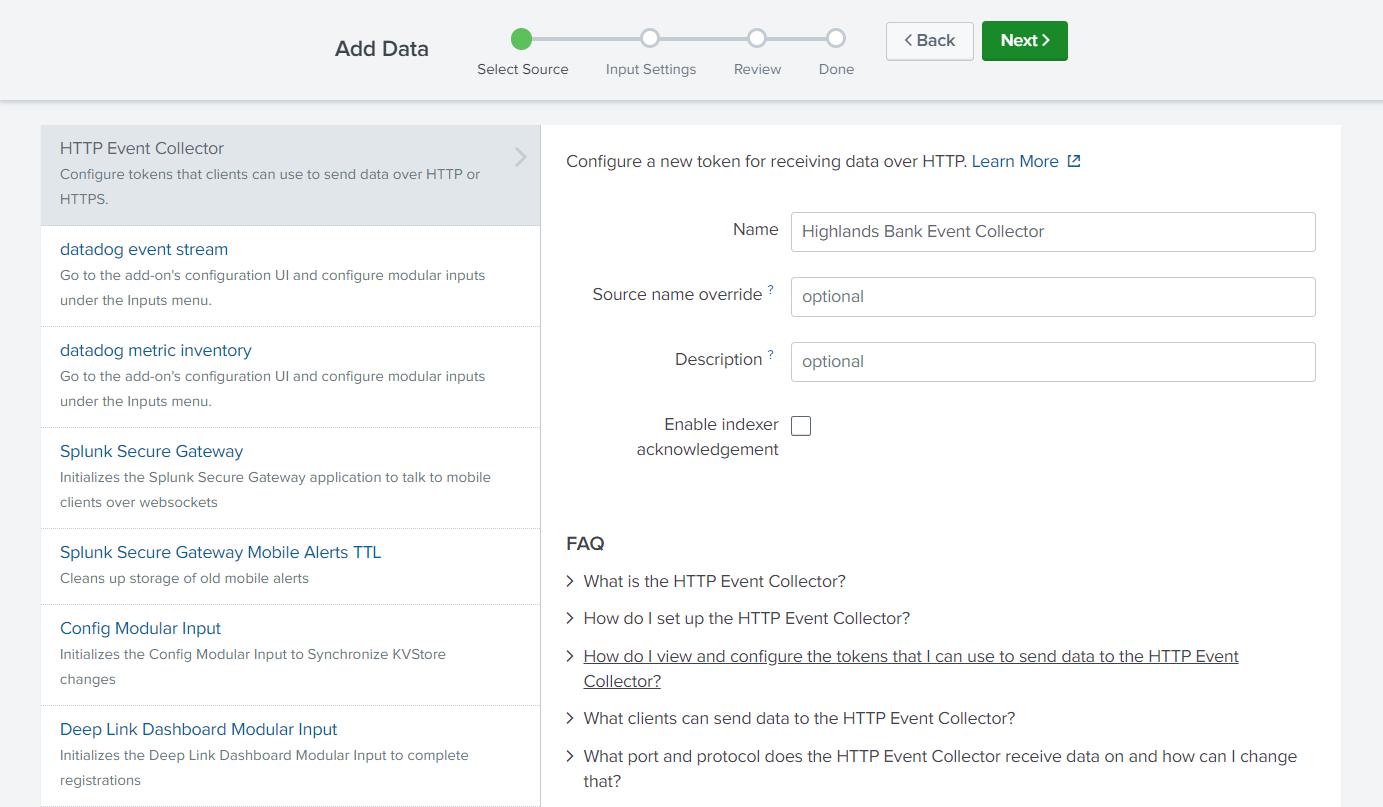
- On the Input Settings pane:
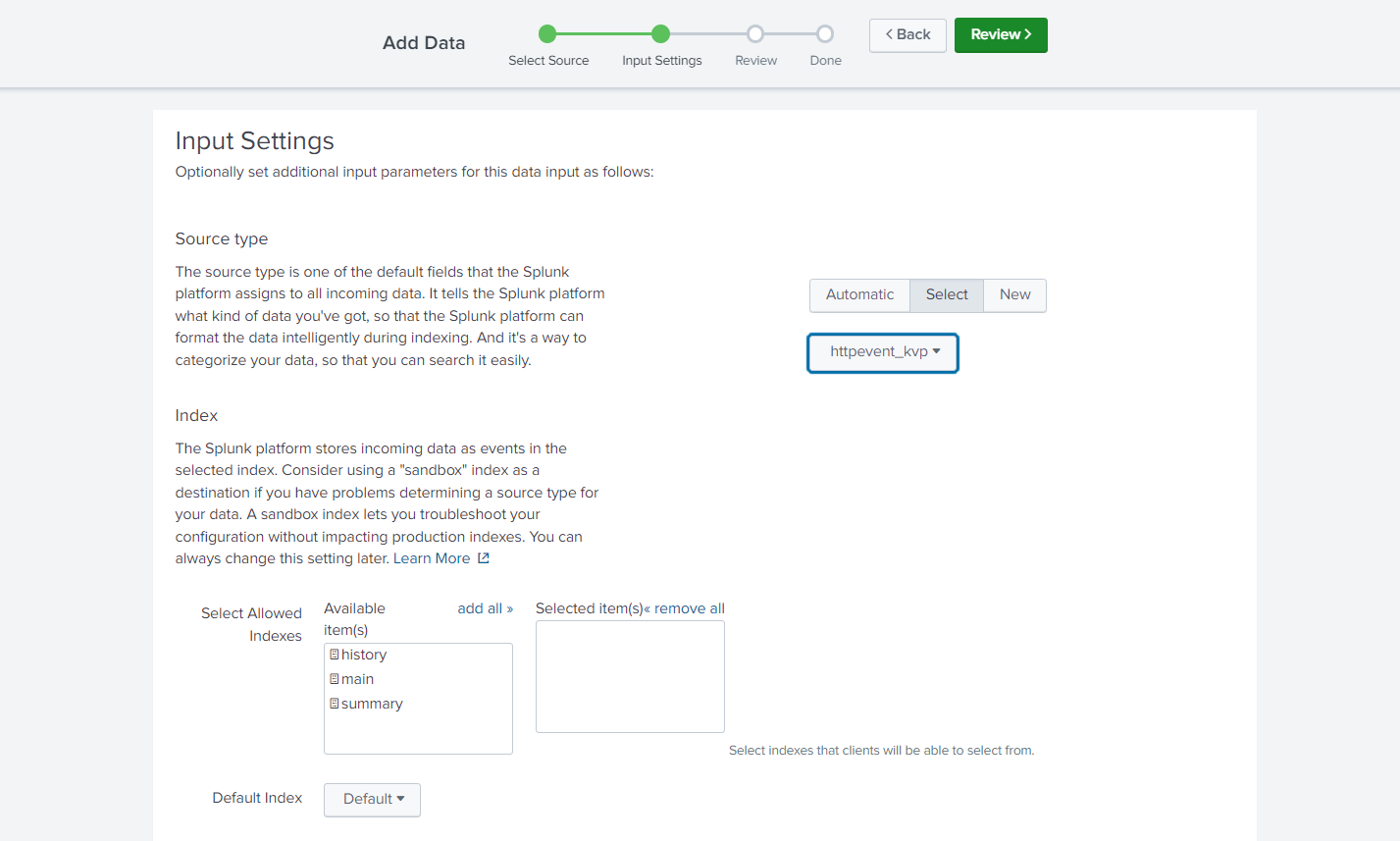
- Set the Source Type to Select; in the drop-down that appears, choose httpeventkvp (or whatever you named your Source Type earlier)
- Select Allowed Indexes by double-clicking the ones you want to copy into the Selected item(s) pane
- Click Review when you are satisfied
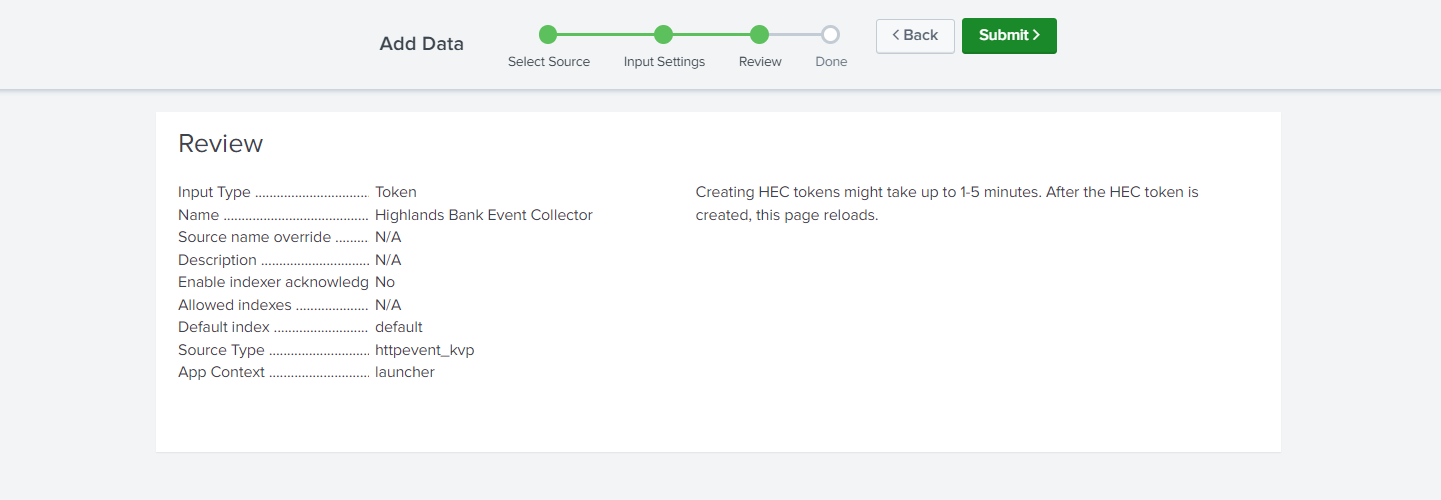
- Review the HTTP Event Collector (HEC) values you entered, then click Submit.
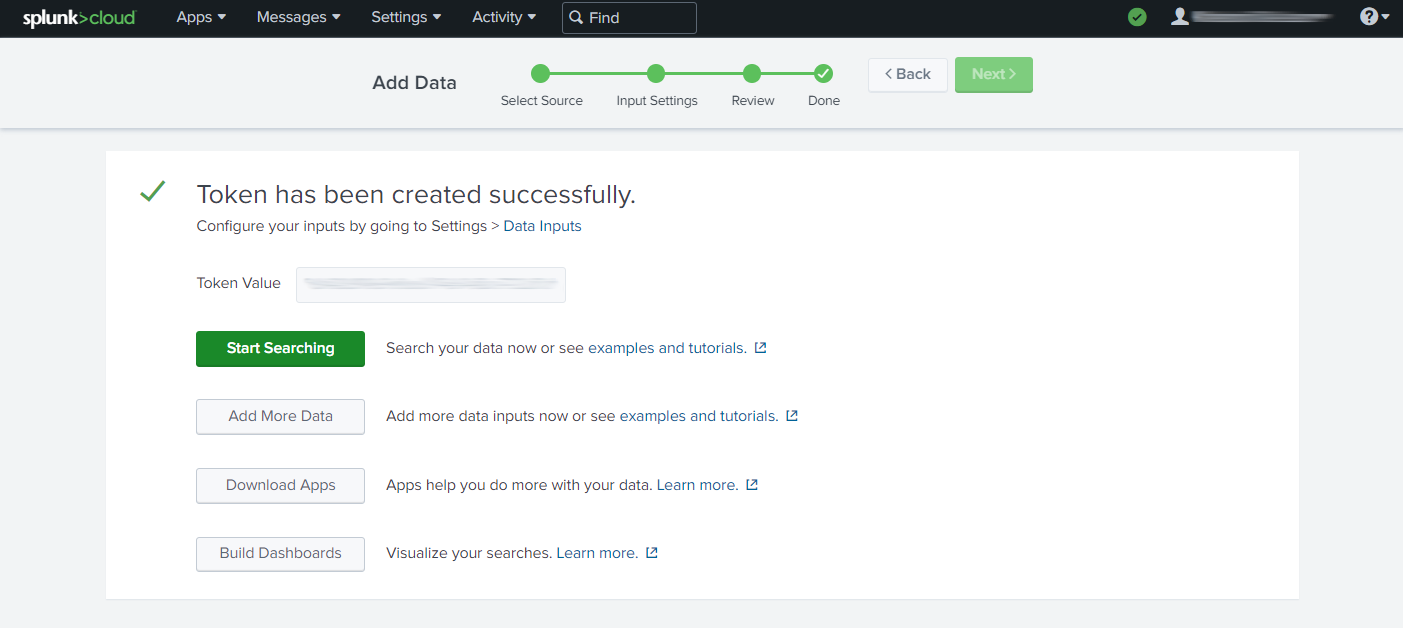
- A confirmation screen appears. Copy the Token Value for use in Control Center.
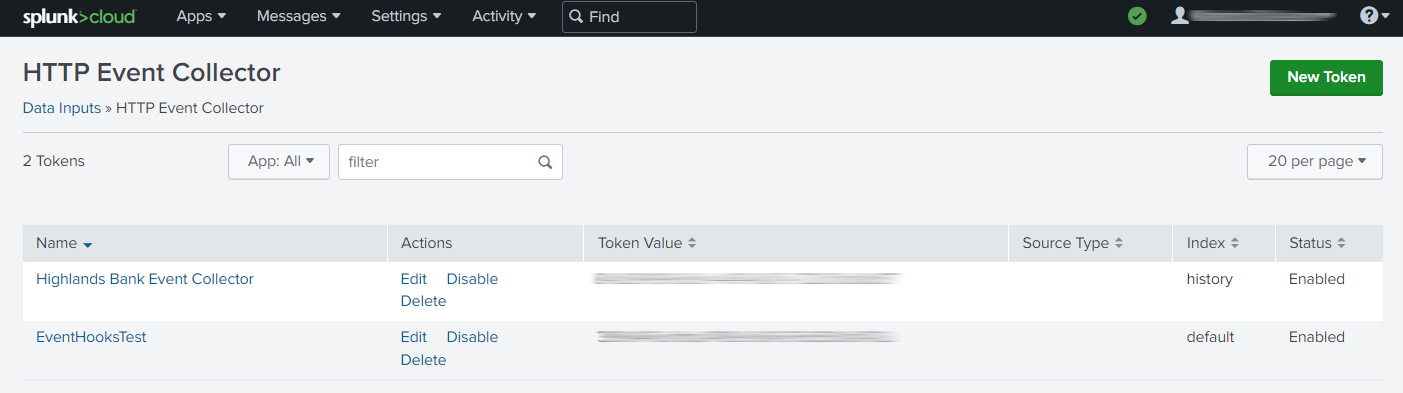
- Return to Settings -> Data Inputs -> HTTP Event Collector and you will not see your new HTTP Event Collector listed with its token value listed.
- Note the subdomain value in your Splunk URL; for example, in
hypr.splunkcloud.com, it would be hypr.
Connecting Splunk to HYPR
You will need the HTTP Event Collector token and the Splunk URL subdomain to proceed.
- Login to HYPR Control Center as an administrator.
- In the left navigation menu, click Integrations.
- On the Integrations page, click Add New Integration. CC displays available integrations.
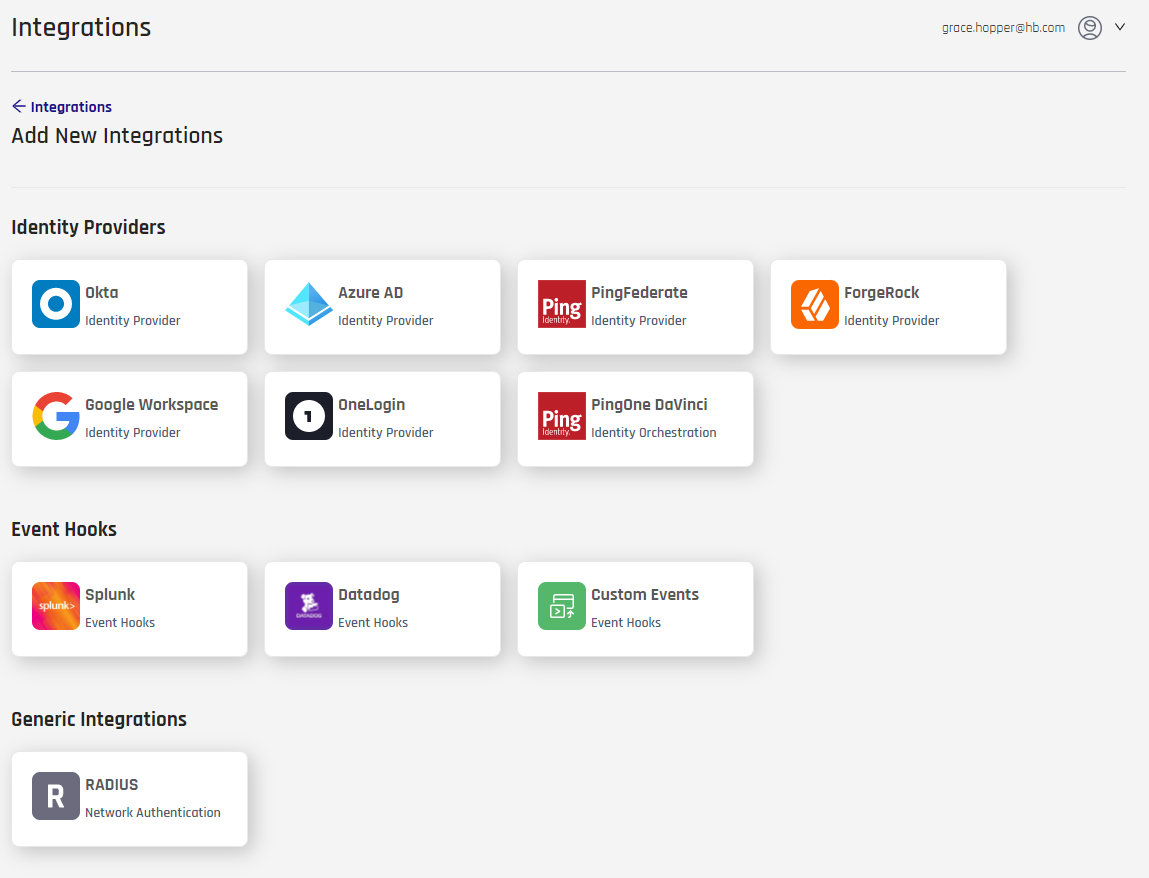
- Click the tile under Event Hooks for Splunk.
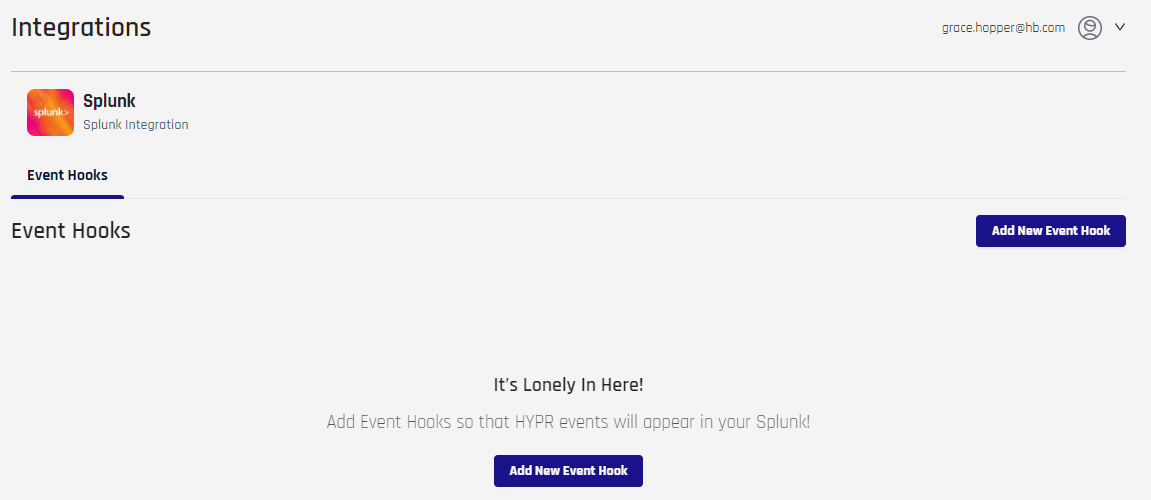
- Click Add New Event Hook.
- On the Add New Event Hook dialog, complete the fields as follows:
| Field | Value |
|---|---|
| Event Name | Type a unique label to identify the Event Hook. |
| Event Type | Select an Event Type to monitor. ADMIN | ALL | AUTHENTICATION | DEREGISTRATION | MAGIC_LINK | OFFLINE_ACCESS | REGISTRATION | SMART_KEY | WEB_REGISTRATION |
| Cloud Provider | Splunk Cloud | Google Cloud |
| HEC Host | The subdomain value from the Splunk URL. |
| API Key | The Token Value from the Splunk HTTP Event Collector. |
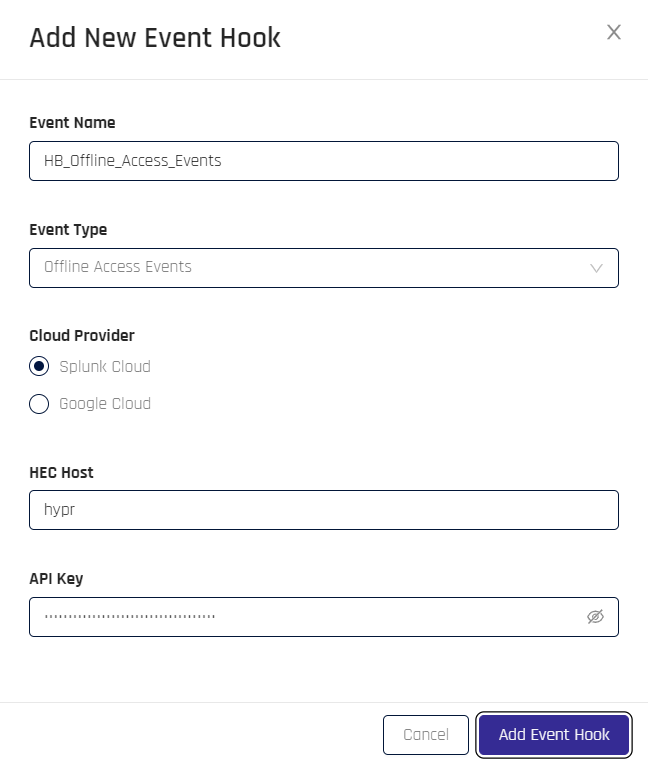
- Click Add Event Hook when you are satisfied. CC returns to the Splunk Event Hooks page.
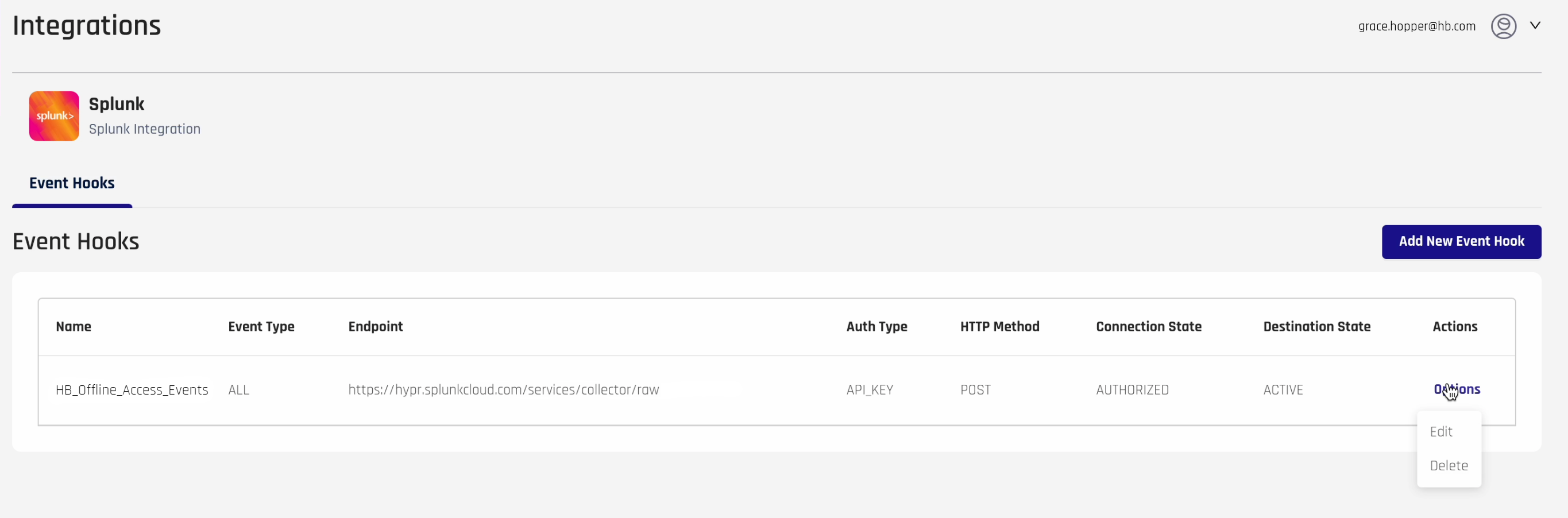
Interpreting Splunk Event Hook Entries
The Splunk Integration Event Hooks table displays values for the available Splunk Event Hooks.
| Field | Description |
|---|---|
| Name | The unique name of the Event Hook. |
| Event Type | The eventTags value associated with the Event Hook.ADMIN | ALL | AUTHENTICATION | DEREGISTRATION | MAGIC_LINK | OFFLINE_ACCESS | REGISTRATION | SMART_KEY | WEB_REGISTRATION |
| Endpoint | The location of the desired endpoint on the Splunk server. |
| Auth Type | API_KEY | BASIC | OAUTH_CLIENT_CREDENTIALS |
| HTTP Method | DELETE | GET | HEAD | OPTIONS | PATCH | POST | PUT |
| Connection State | AUTHORIZED | AUTHORIZING | CREATING | DEAUTHORIZED | DEAUTHORIZING | DELETING | UPDATING |
| Destination State | ACTIVE | INACTIVE |
| Actions (Hover on Options) | Edit | Delete See Editing HYPR Splunk Event Hooks and Deleting HYPR Splunk Event Hooks for how to perform these actions. |
Clicking the name of the Event Hook will open a pane with additional information about the entry:
| Field | Description |
|---|---|
| Auth Params | The .JSON payload for authentication parameters. |
| Connection State Reason | The reason that the connection is in the connection state. |
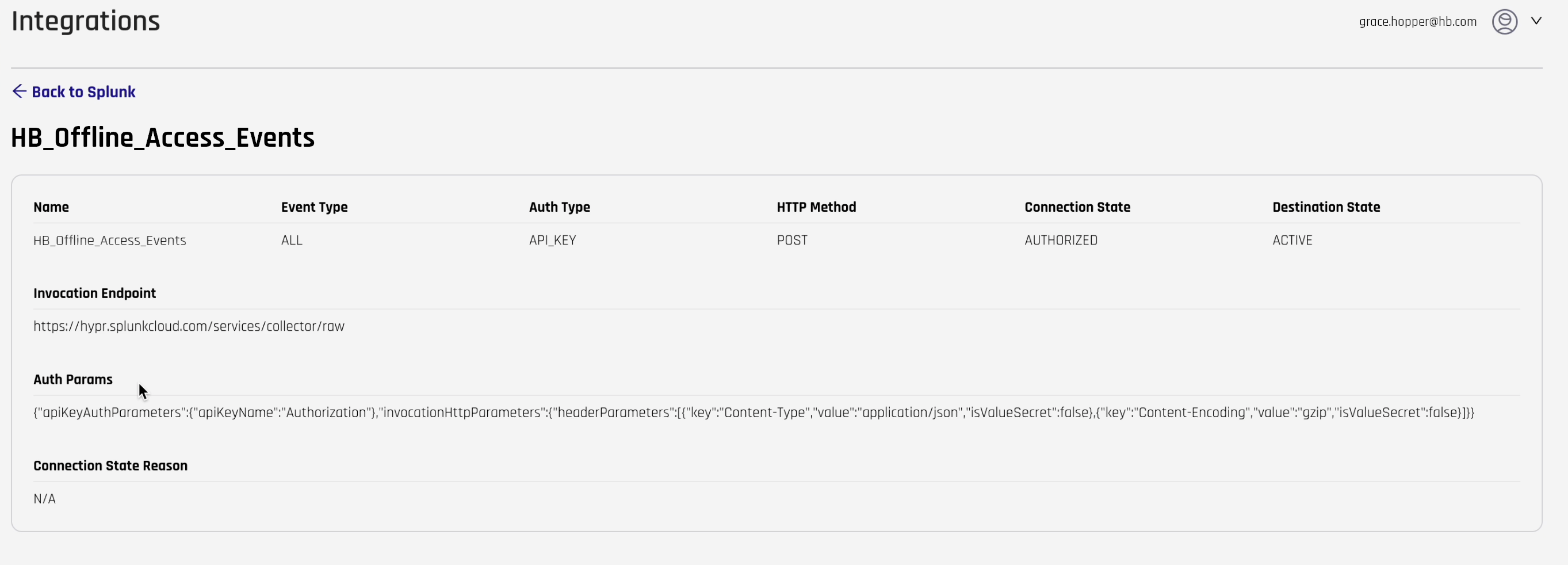
Clicking Back to Splunk returns you to the Splunk Event Hooks page.
Editing HYPR Splunk Event Hooks
- On the Splunk Integration Event Hooks table, on the right side under Actions, click Options-> Edit for the Event Hook you wish to modify.
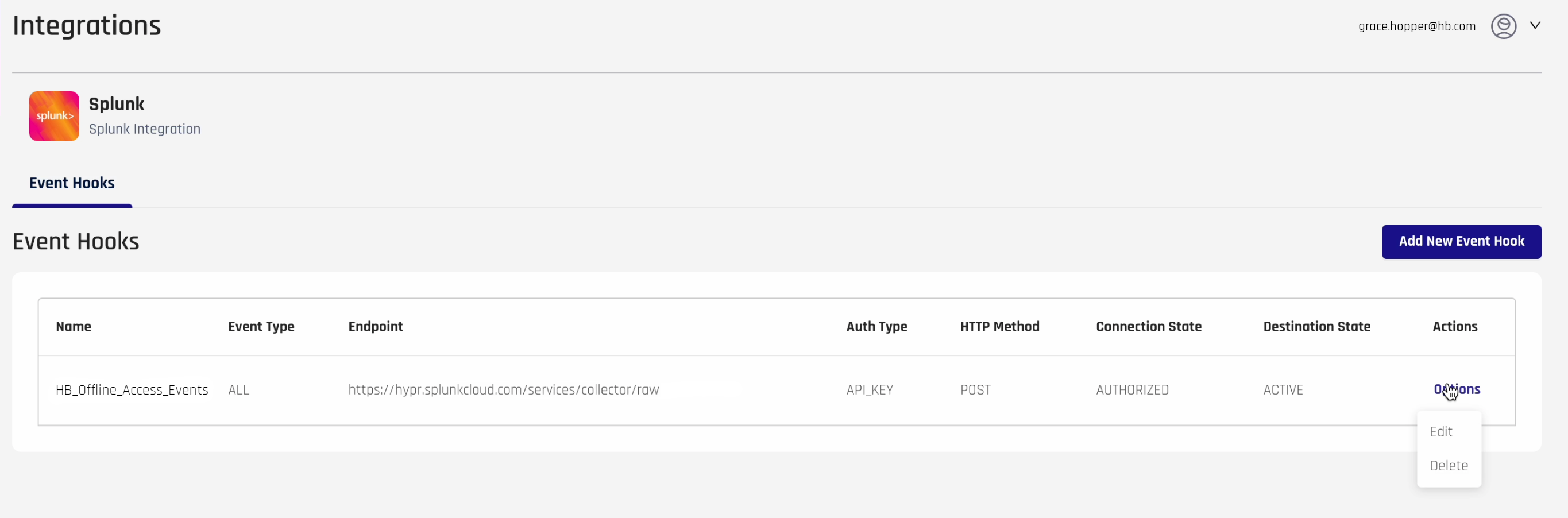
- The Event Hook Details dialog opens. Make changes as needed using the values given in Connecting Splunk to HYPR, Step 6, above.
- Click Save to return to the Event Hooks page.
Deleting HYPR Splunk Event Hooks
- In the Splunk Integration Event Hooks table, on the right side under Actions, click Options-> Delete for the Event Hook you wish to remove.
- The Delete Event Hook dialog opens. Click Delete to remove the event hook.
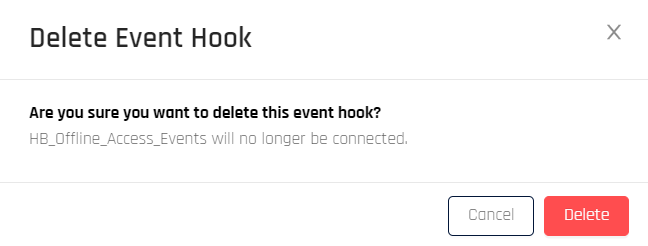
- A dialog appears confirming the Event Hook was deleted. CC returns to the Event Hooks page.
Housekeeping
You may also wish to delete the HTTP Event Collector from Splunk if it is not used by any other systems.
Viewing HYPR Event Data in Splunk
When you go into Splunk to view a report on HYPR Events, the parameters associated with the data field will be broken out in the left pane under INTERESTING FIELDS. Drill into them for details about the parameters as they occurred in a given HYPR Event.
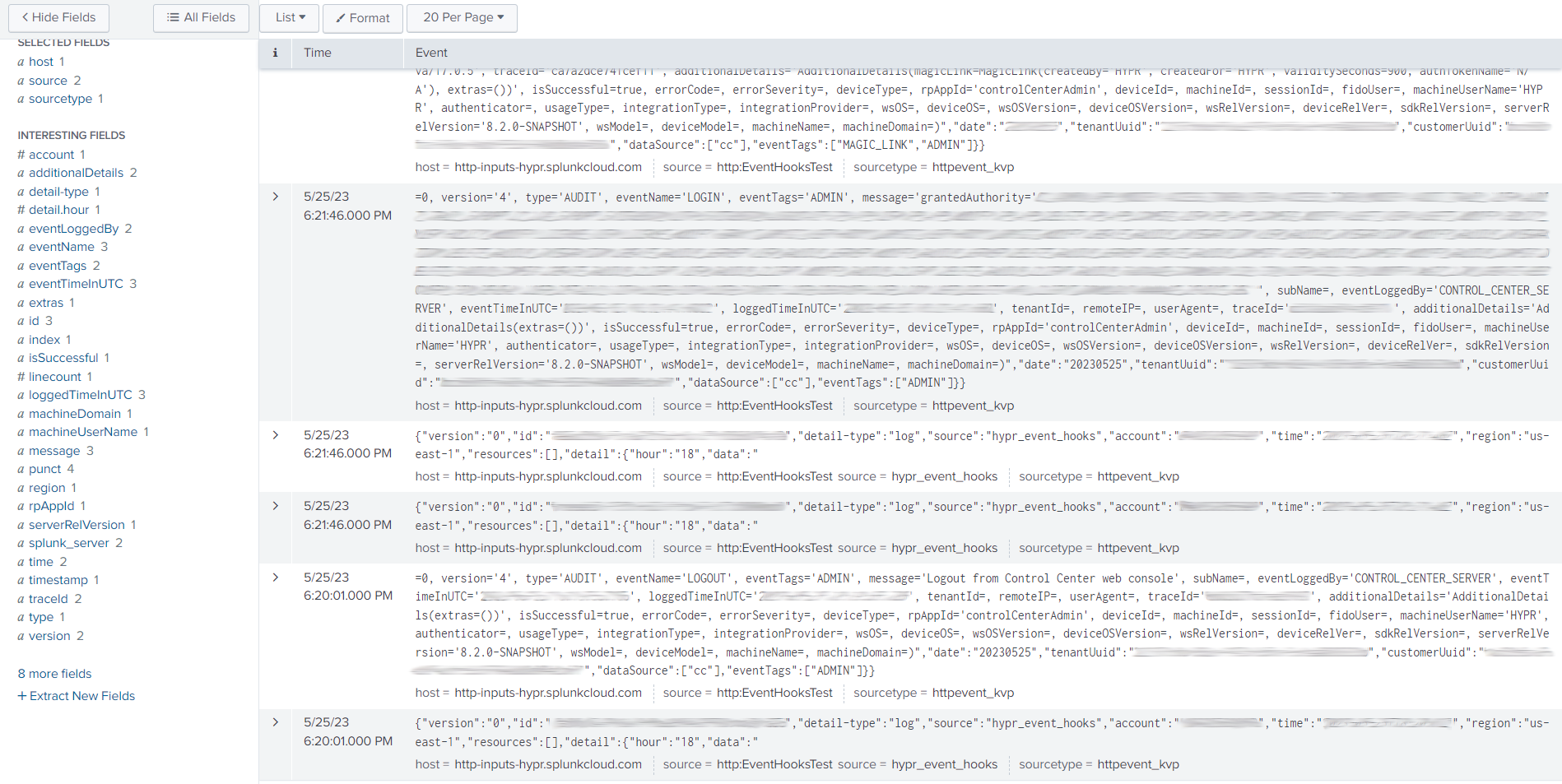
See Event Descriptions: Event Parameters for a full rundown on all Event parameters and their values.
Updated 5 months ago
