Endpoint Protection
HYPR Passwordless: Advanced Configuration
To ensure the overall security of the HYPR platform, the various HYPR components (HYPR Passwordless Client, HYPR Mobile App, and Control Center) pass an encrypted token to the HYPR Server when making internal API calls.
When installing the HYPR Passwordless client on a user's machine, you need to include an RP application-specific Access Token generated by the Control Center. The HYPR Passwordless client will verify the token's validity with the HYPR Server during the pairing process and automatically exchange it for a new device-unique security token which is then used to authenticate all HYPR communications between the workstation, the mobile device, and the HYPR Server.
First you must create the new access token for installing on that workstation (endpoint). Then you will need to install HYPR Passwordless client for Windows using the access token you make.
Waiting for an Invitation
This feature is not enabled by default. Please contact your HYPR Support team member to enable it for your organization.
Windows
Generate the Workstation Installation Token
Complete the steps under Creating Access Tokens. Use the same token when installing or upgrading the HYPR Passwordless Client (see below):
"installToken": "6a74ce20-2c1e-4c7d-ae9d-14be27e2c197"
Use the Access Token to Install HYPR Passwordless Client for Windows
Once you've generated an access token, include it when installing the HYPR Passwordless Client on the workstation. Installation can happen either by using the wizard or by the command line.
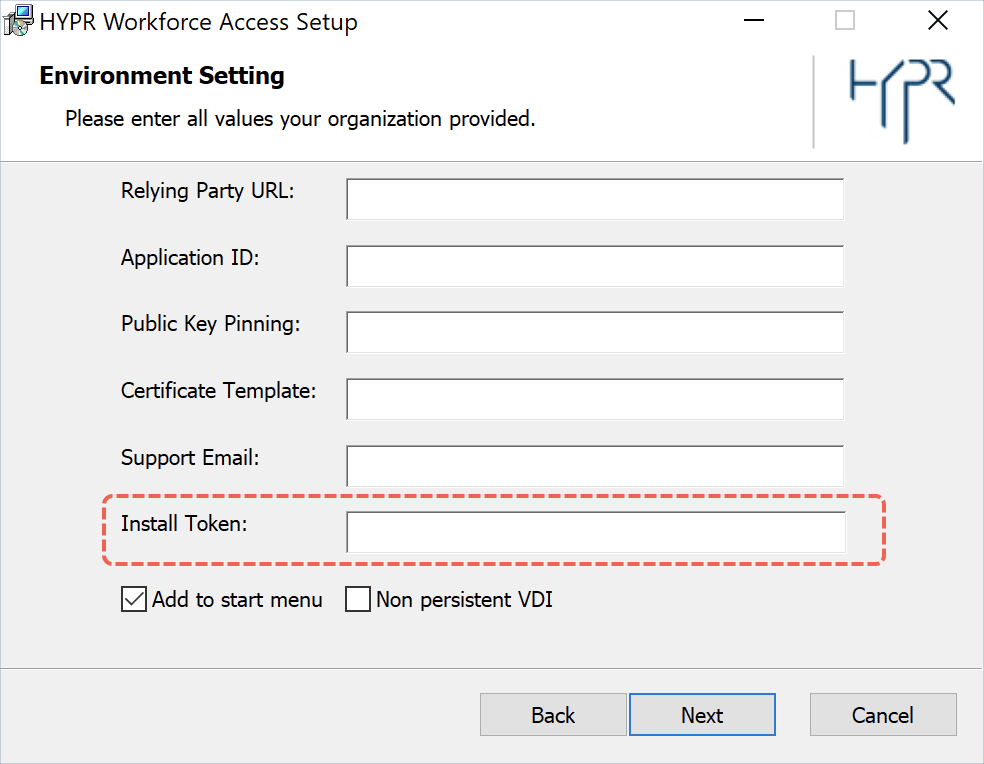
Using the Wizard
If you're using the HYPR installer, set the Install Token value on the Environment Setting screen to the token you generated above.
Using msiexec with Command Line Parameters.
msiexec with Command Line Parameters.If you're setting the parameters directly on the command line, pass in the token via the HYPRINSTALLTOKEN parameter. See Command Line Installation for Windows.
msiexec.exe /qn /i .\WorkforceAccess.msi HYPRAPPID="WorkstationAccess" HYPRRP="https://highlandsbank.com/rp"
HYPRSUPPORT="[email protected]" HYPRHASH="LeM8XnCIy8+Cxm+HKTEOBZr1g3D8odQNHTH+vdu7RWc="
HYPRTEMPLATE="HYPRUser" HYPRINSTALLTOKEN="6a74ce20-2c1e-4c7d-ae9d-14be27e2c197"
Using msiexec with the hypr.json File
msiexec with the hypr.json FileIf you're setting the parameters using the hypr.json configuration file, pass in the token via the installToken parameter.
{
"version":"1.0",
"rpUrl":"https://highlandsbank.com/rp",
"appId":"WorkstationAccess",
"pinningHash":"LeM8XnCIy8+Cxm+HKTEOBZr1g3D8odQNHTH+vdu7RWc=",
"supportEmail":"[email protected]",
"installToken":"6a74ce20-2c1e-4c7d-ae9d-14be27e2c197",
"fullUI":"1"
}
Feature Security
For security reasons, the
InstallTokenparameter won't be displayed in the Registry Editor alongside the other HYPR keys.
Upgrading Earlier Versions
When you upgrade an earlier version of the HYPR Passwordless client to 6.12.0 or higher, you need to add the Install Token value as part of the update process. This is mandatory step.
The installation commands are the same as for a fresh install (see above). However, you only need to provide the new Install Token value. The installer will reuse the existing values for the rest of the parameters.
For example, to upgrade using msiexec with command line parameters, just specify the HYPRINSTALLTOKEN value:
msiexec.exe /q /i WorkforceAccess_x64.msi HYPRINSTALLTOKEN="6a74ce20-2c1e-4c7d-ae9d-14be27e2c197"
macOS
Generate the Workstation Installation Token
Complete the steps under Creating Access Tokens. Use the same token when installing or upgrading the HYPR Passwordless Client (see below):
"installToken": "6a74ce20-2c1e-4c7d-ae9d-14be27e2c197"
Use the Access Token to Install HYPR Passwordless Client for Mac
Once you've generated a Workstation Installation access token, include it when installing the HYPR Passwordless client on the workstation. See Installing with the UI: Installing on macOS.
Upgrading Earlier Versions
When you upgrade an earlier version of the HYPR Passwordless client to 6.12.0 or higher, you need to include the Install Token value as part of the update process. This is mandatory step.
If your installer came without a hypr.json configuration file, you'll need to manually create one with the installToken field added. For example:
{
"version":"4",
"rpUrl":"https://highlandsbank.com/rp",
"appId":"WorkstationAccess",
"pinningHash":"LeM8XnCIy8+Cxm+HKTEOBZr1g3D8odQNHTH+vdu7RWc=",
"supportEmail":"[email protected]",
"installToken":"6a74ce20-2c1e-4c7d-ae9d-14be27e2c197",
}
See the Installing Manually page for more information about the hypr.json configuration file.
To upgrade, place the hypr.json file and the HYPR installer package in the same folder and execute:
installer -pkg WorkforceAccess-X.X.X-Installer.pkg
Updated 4 months ago
