Installing Manually
HYPR Workforce Access Client: Installation
For testing and pilot purposes you can install the HYPR Workforce Access Client application manually for each user. However, for deploying to larger segments of your workforce population you’ll want to integrate with a configuration management solution such as Microsoft Endpoint Configuration Manager (formerly SCCM) or Jamf on macOS.
This page describes the available installation parameters and shows how to run the installer from the command line for compatibility with configuration management tools.
Installation Parameters
For both Windows and macOS, the HYPR installer reads its configuration parameters from the hypr.json file located in the same directory as the installer. For Windows, you can also pass the parameters directly on the command line.
All Right
If your downloaded install package already includes a
hypr.jsonfile, be cautious about changing any of the preconfigured values. This is how HYPR provides the necessary custom parameters for your installation.
The `hypr.json file is a simple collection of name-value pairs, each defining a single install parameter. For example:
{
"version":"1.0",
"rpUrl":"https://highlandsbank.hypr.com/rp",
"appId":"HighlandsBankWeb",
"pinningHash":"LeM8XnCIy8+Cxm+HKTEOBZr1g3D8odQNHTH+vdu7RWc=5kJvNEMw0KjrCAu7eXY5HZdvyCS13BbA0VJG1RSP91w=",
"installToken":"0f03f635-4d9a-46ff-b537-cd97ad77cb6e",
"certTemplate": "hyprwin",
"securityKeyCertTemplate": ""
"supportEmail":"[email protected]",
"fullUI":"1"
}
The available parameters are as follows:
| JSON | Command Line | Description |
|---|---|---|
rpUrl | HYPRRP | (Required) The URL of your HYPR instance:https://highlandsbank.hypr.com/rpNote that the URL must end in /rp |
appId | HYPRAPPID | (Required) The ID of the HYPR Control Center internal application used to configure the Workstation functionality. The value may vary for different HYPR deployments. Integrated Workforce Access Clients will typically use the Integration appID.EX: HighlandsBankWeb |
pinningHash | HYPRHASH | (Required) An SHA1 hash of the HYPR server SSL certificate which serves as a public key pinning value. This value can be obtained from the hypr.json file included when you download HYPR Passwordless (Workforce Access Client). |
installToken | HYPRINSTALLTOKEN | (Required) A token used to establish encrypted communication between the Workforce Access Client and the HYPR Server. The value is pre-set for each HYPR deployment and shouldn’t be changed. |
certTemplate | HYPRTEMPLATE | The name of the Active Directory certificate template for Advanced Installs and mobile enrollment. HYPR Support will help you create and name the template, but by default the template name is either hyprwin (for Windows) or hyprmac (for macOS).If you prefer to create your own custom AD certificate template, please follow these instructions. |
supportEmail | HYPRSUPPORT | The email address used for any support requests sent by the user from within the Workforce Access Client. |
proxyServer | HYPRPROXYSERVER | A proxy server to be used when the HYPR Workforce Access Client communicates with the HYPR Server, in the form proxy[:port]. For example:proxy.myoffice.com:3128The port is optional and defaults to 8080. |
proxyBypass | HYPRPROXYBYPASS | A comma-separated list of host names to be excluded from the proxy connection. If the URL matches any of the hosts in the list, the proxy will be bypassed and a direct connection made. Host names can include wildcards (e.g., .mycompany.com or 10.20.). |
certPublishers | N/A | (macOS only) (Optional) A comma-separated a list of DNS names for the servers running the service that can generate certificates on behalf of the user. The Workforce Access Client will browse the AD forest if you omit this parameter, but if you have multiple servers deployed to manage the domain infrastructure it can take time to explore all of them. This corresponds to the CertificatePublishers value described in Configuration Parameters. |
certAuthority | N/A | (macOS only) (Optional) The name of the publisher of the Active Directory. The Workforce Access Client will browse the AD forest if you omit this parameter, but if you have multiple servers deployed to manage the domain infrastructure it can take time to explore all of them. This corresponds to the CertificateAuthority value described in Configuration Parameters. |
fullUI | N/A | (Windows only) Should the Environment Setting dialog be displayed during the install. 0 - hide the dialog 1 - show the dialog Hiding the dialog keeps users from changing any of the configuration parameters set in the hypr.json configuration file when the installer is run normally. Not applicable when installing using msiexec with command-line parameters. |
customLogo | HYPRCUSTOMLOGO | (Windows only) The path to a locally stored custom image to override the default HYPR logo. Supported formats: .png, .jpg, or .svgPreferred image size: 101×82 pixels Backslashes in the file path need to be doubled up. For example: C:\\myImages\hb_logo.png |
customBackground | HYPRCUSTOMBACKGROUND | (Windows only) The path to a locally stored custom image to override the default background. Supported formats: .png, .jpg, or .svgPreferred image size: 633×398 pixels Backslashes in the file path need to be doubled up. For example: C:\\myImages\hb_backgound.png |
passwordlessUserTile | HYPRPASSWORDLESSUSERTILE | (Windows only) If enabled (value 1), the Passwordless User login tile displays by default. Otherwise (value 0), the default is controlled by Windows. The equivalent registry setting is Passwordless User Tile. This functionality requires Roaming Users to be enabled. |
securityKeyCertTemplate | HYPRSECURITYKEYTEMPLATE | (Windows only) The name of the Active Directory certificate template if using non-exportable private keys. If this parameter is defined, HYPR Workforce Access Client will use the certTemplate value when requesting a certificate for a mobile enrollment, and the securityKeyCertTemplate when requesting a certificate for a security key. If a value is not specified (or is empty), the same template will be used for mobile devices and security keys.Installations using this parameter will generate a Certificate Template (Security Keys) registry value in the key, HKLM:\SOFTWARE\HYPR Workforce Access.To create your own custom AD non-exportable security key certificate template, please follow these instructions. |
Command Line Installation for Windows
You can use the msiexec command to deploy the HYPR Workforce Access Client for Windows without the displaying the installation UI. Note that if you’re doing this manually at the command line you’ll need to run from a command prompt that has administrative privileges.
You have two options for setting the necessary parameters:
Option 1
- Define the installation parameters in a
hypr.jsonconfiguration file located in the same folder as the Workforce Access.msifile. (See Installation Parameters above.) - Run
msiexecwithout any parameters:
msiexec.exe /qn /i WorkforceAccess_x64.msi
Option 2
- Pass the installation parameters directly to
msiexecon the command line. For example:
msiexec.exe /qn /i WorkforceAccess_x64.msi HYPRAPPID="HighlandsBankWeb"
HYPRRP="https://highlandsbank.hypr.com/rp" HYPRSUPPORT="[email protected]" HYPRHASH="LeM
8XnCIy8+Cxm+HKTEOBZr1g3D8odQNHTH+vdu7RWc=,5kJvNEMw0KjrCAu7eXY5HZdvyCS13BbA0VJG1RSP91w="
HYPRINSTALLTOKEN="0f03f635-4d9a-46ff-b537-cd97ad77cb6e" HYPRSUPPORT="[email protected]"
HYPR Registry Keys
The installation process adds a HYPR key to the Windows Registry at the following location:
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\HYPR Workforce Access
The contents of this registry key are required for normal functioning of the application and shouldn’t normally be changed post-install. However, for troubleshooting purposes HYPR Support may ask you to review or modify some of the values.
Terminal Installation for macOS
You can use the installer command to deploy the HYPR Workforce Access Client for macOS without displaying the installation UI. Note that if you’re doing this manually in a Terminal window you’ll need to use sudo to grant the necessary privileges.
- Define the installation parameters in a
hypr.jsonconfiguration file located in the same folder as the Workforce Access.pkgfile. (See Installation Parameters above.) - Run the
installercommand as follows:
installer -pkg /path/to/WorkforceAccess-\<version\>-Installer.pkg -target /
- The installer will prompt you for a password (if using
sudo) and report on the status of the install. For example (replace with the HYPR version):
ghopper@MacBook-Pro ~ % sudo installer -pkg /Users/gracehopper/Desktop/WorkforceAccess-
[<version>]-Installer.pkg -target /
Password:
installer: Package name is WorkforceAccess-<version>-Installer
installer: Upgrading at base path /
installer: The upgrade was successful.
installer: The install requires restarting now.
ghopper@MacBook-Pro ~ %
- Restart the workstation when finished.
HYPR Application .plist Keys
.plist KeysThe installation process stores a number of key values in an application .plist file in the following location:
/Library/HYPR/HyprOneService.plist
These keys are required for normal functioning of the application and shouldn’t normally be changed post-install. However, for troubleshooting purposes HYPR Support may ask you to review or modify the values.
Configuration Parameters
| Parameter | Description | Type | Example |
|---|---|---|---|
ApplicationId | Name of your Application in the HYPR Control Center | Required | AcmeMacOSApp |
RelyingPartyPins | Pinning Hash | Required | (a long hash string) |
RelyingPartyUrl | URL of your HYPR tenant with added /rp path. | Required | https://acme.hypr.com/rp |
SupportEmail | Email address of your support team managing the HYPR server. | Required | [email protected] |
CertificateAuthEnabled | A boolean parameter that enables/disables certificate-based authentication. | Optional | true |
CertificateTemplate | Name of your Certificate Template in the Microsoft Security Authority. This is a required parameter if you're using the domain-joined computer. | Optional | AcmeMacOSUser |
CertificatePublishers | A comma-separated a list of DNS names for the servers running the service that can generate certificates on behalf of the user. The Workforce Access Client will browse the AD forest if you omit this parameter, but if you have multiple servers deployed to manage the domain infrastructure it can take time to explore all of them. This corresponds to the certPublishers value described in Installation Parameters. | Optional | DNS1.ADDRESS.COM, DNS2.ADDRESS.COM |
CertificateAuthority | The name of the publisher of the Active Directory. The Workforce Access Client will browse the AD forest if you omit this parameter, but if you have multiple servers deployed to manage the domain infrastructure it can take time to explore all of them. This corresponds to the certAuthority value described in Installation Parameters. | Optional | hypr-DEVW2012R9DOMXDC-CA |
Manual Configuration
- In a terminal, use
sudoto edit/Library/HYPR/HyprOneService.plistvia an editor (vi, nano, etc.). - Modify the file according to your configuration. It will appear similar to this:
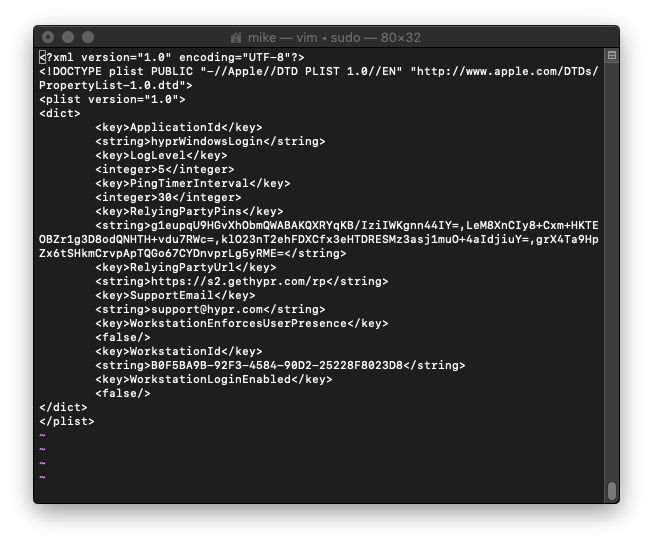
-
Update the
ApplicationId,RelyingPartyUrl,RelyingPartyPins, andSupportEmailbased on the current server configuration. -
Reboot the computer to apply the changes.
Enterprise Deployment and Configuration
To deploy the HYPR Workforce Access Client in an enterprise, wrap a script around that installation package. The script installs the package and updates the HyprOneService.plist file of all affected users.
This can be achieved with a combination of the defaults and plutil commands.
Example
#! /bin/bash
PLIST_FILE=/Library/HYPR/HyprOneService.plist
# Install the HYPR Employee Access package.
installer -pkg EmployeeAccess-2.1-Installer.pkg
# Customize the configuration.
defaults write $PLIST_FILE ApplicationId "NAME OF YOUR APP IN CONTROL CENTER"
defaults write $PLIST_FILE RelyingPartyPins "<COMMA DELIMITED LIST OF PINS>"
defaults write $PLIST_FILE RelyingPartyUrl "https://CONTROL_CENTER_URL/rp"
defaults write $PLIST_FILE SupportEmail "SUPPORT EMAIL"
# Convert the configuration file to XML.
plutil -convert xml1 $PLIST_FILE
FileVault Configuration
Apple FileVault doesn't support the smart card authentication protocol, and it can only be unlocked with a user password. Still, there's an option to require HYPR authentication after the FileVault unlock to ensure that users are always using an MFA solution.
Disable the automatic login option of FileVault by executing the following command:
sudo defaults write /Library/Preferences/com.apple.loginwindow DisableFDEAutoLogin -bool YES
If this is disabled, users will be required to authenticate with HYPR Mobile App after entering the FileVault password.
Updated 4 months ago
