HYPR Linux PAM
Linux pluggable authentication modules (PAM) enable administrators to configure users’ authentication experiences. This document provides a method to require HYPR authentication—including YubiKey compatibility—when connecting via ssh/scp using Linux PAM libraries.
Creating an operational HYPR Linux PAM involves at minimum the following stages:
-
Installation
-
Get the installation files
-
Run the installation
-
-
Configuration
-
HYPR PAM configuration
-
Linux PAM configuration
-
Linux SSH configuration
-
As long as the user in question is added to the Application in question using the HYPR Control Center, the above stages will enable HYPR authentication when ssh or scp is used to or from a device with the HYPR Linux PAM installed.
Other options include:
-
Bypassing HYPR authentication
-
Linux SSH key authentication
-
Linux password authentication
-
Username aliases
-
YubiKey Interoperability
-
Install the YubiKey Linux PAM
-
Configure the YubiKey Linux PAM
-
Making it work with HYPR Linux PAM
-
-
Building the HYPR Linux PAM
-
Build the shared library
-
Integrity checks
-
Installation
HYPR Linux PAM may be installed via standard RPM or DEB packages. It has been tested and found operational on the following platforms:
Be sure to make backups of any files that you edit during the process.
To monitor the logs and progress of tasks while installing HYPR Linux PAM, we suggest opening a second terminal window and keeping it open throughout the entire process with the affected log files open in the window as they are being written.
Get HYPR Linux PAM
Contact HYPR Support to get your own copy of the HYPR Linux PAM.
Run the Installation
Run the following commands to install the package you are using, substituting the version for the download you have obtained:
-
RedHat, CentOS, Fedora, and similar
-
x86_64 architecture:
sudo yum localinstall -y hypr-pam-**x.y-z**.x86_64.rpm -
aarch64 (arm64) architecture:
sudo yum localinstall -y hypr-pam-**x.y-z**.aarch64.rpm
-
-
Ubuntu, Debian, Kali, Mint, and similar
-
x86_64 architecture:
sudo dpkg --install hypr-pam_**x.y-z**\_amd64.deb\ -
aarch64 (arm64) architecture:
sudo dpkg --install hypr-pam_**x.y-z**_arm64.deb
-
-
openSUSE and similar
-
x86_64 architecture:
sudo zypper install hypr-pam-**x.y-z**.x86_64.rpm -
aarch64 (arm64) architecture:
sudo zypper install hypr-pam-**x.y-z**.aarch64.rpm
-
Configuration
The pam_hypr module is a Linux programmable authentication module (PAM) responsible for Linux user authentication via HYPR authentication. It is implemented in the pam_hypr.so shared library created during Build the Shared Library, above.
Configuration consists of three main steps:
-
HYPR PAM Configuration (
/etc/security/pam_hypr.conf). -
Linux PAM Configuration (
/etc/pam.d). -
Linux SSH Configuration (
/etc/ssh/sshd_config).
Configuration Keywords
Below are details of the contents of this pam_hypr.conf configuration file. Each line contains one or more keywords followed by one or more values, each separated by one or more spaces (or tabs). Lines beginning with '#' are ignored completely.
| Keywords | Requirement | Value |
|---|---|---|
auth_access_token | Required | Used for authentication, this HYPR access token is associated with the HYPR application identified by the app_id property in this configuration. Ex: b284ad3f-401c-32f7-813f-12a5c7d9e034 |
api_access_token | Optional | Used only for managing username aliases, this HYPR access token is associated with the HYPR Control Center controlCenterAdmin application. |
api_base_url | Required | The base URL for the HYPR authentication API. Ex: https://hypr.highlandsbank.com |
api_auth_endpoint | Required | The endpoint for the HYPR authentication API. Default value: /rp/api/oob/client/authentication |
app_id | Required | The HYPR authentication API ID. Ex: HYPRDefaultApplication |
poll_max_time_seconds | Optional | The total number of seconds to wait for a user response when doing HYPR authentication response polling. Default value: 60 |
poll_interval_seconds | Optional | The number of seconds to wait between each polling for a user HYPR authentication response. Default value: 2 |
timeout_milliseconds | Optional | The number of milliseconds before timing out to allow for each HYPR authentication service (HTTPS) request. If set to 0 the system default as implemented by libcurl is used. Default value: 20000 (20 seconds) |
login_message | Optional | If enabled the message following this keyword will be displayed on the command line (stdout) on successful connection to the server. Within this message the following variables may be used to generate dynamic content: • %login – The Linux login • %username – The HYPR username • %remotehost – The hostname (or IP address) of the host from which the user is authenticating |
disabled | Optional | Set to true to disable HYPR. authentication. |
disabled login | Optional | If this value is set to a Linux login name, HYPR authentication will be disabled for that login. There is no limit to the number of disabled login lines. For example, disabled login ghopper will allow the Linux user ghopper to login bypassing HYPR authentication and using the normal Linux password authentication instead. To bypass HYPR authentication and allow users access via ssh keys, see Bypassing HYPR Authentication. |
disabled group | Optional | If this value is set to a Linux group name, HYPR authentication will be disabled for all users in that group. There is no limit to the number of disabled login lines. To bypass HYPR authentication and allow users access via ssh keys, see Bypassing HYPR Authentication. |
disabled command | Optional | If this value is set to the name of a command which caused the HYPR authentication PAM to be invoked, then HYPR authentication will be entirely disabled for that command. For example, on some systems, due to the way the Linux PAM configuration is organized (e.g., using /etc/pam.d/common-auth, which may be included by other PAM configuration files), the sudo command may implicitly be defined to use HYPR authentication; if this is not desired, the line disabled command sudo may be placed in pam_hypr.conf to disable HYPR authentication for the sudo command. |
Configuration File Sample
# Configuration file for the HYPR Linux PAM (pam_hypr.so)
#
access_token REDACTED
api_base_url https://highlandsbank.com
api_auth_endpoint /rp/api/oob/client/authentication
app_id fIDO2Local
poll_max_time_seconds 60
poll_interval_seconds 2
timeout_milliseconds 30000
login_message HYPR authentication of %login (%username) from %remotehost: OK
#
# Disable HYPR authentication:
# disabled false
#
# Disable HYPR authentication for specific commands:
# disabled command chsh
#
disabled command sudo
#
# Disable HYPR authentication for specific users/logins:
# disabled login ghopper
#
# Disable HYPR authentication for specific groups:
# disabled group adm
# Ignore HYPR authentication if no username mapping is found:
# on_unmapped_login ignore
# Add a mapping from the Linux user/login name to the HYPR account/user name:
#
username hypr-auth-test-login grace.hopper@hb.com
username jclark joan.clark@highlandsbank.com
username another-linux-user another-hypr-account@hb.com
Linux PAM Configuration
Create a good backup before making configuration changes; keep an alternate shell window open until configuration is verified so changes can be reverted if you lock yourself out.
These Linux system PAM configuration files (/etc/pam.d) may vary significantly between systems, and may have already been subject to some customization by the system administrator(s).
The flexibility afforded by the Linux PAM mechanism, with its ability to stack and branch among various PAM modules, is not dissimilar to a programming language, and comes with both the power and risks associated with such.
Some knowledge of the organization and function of Linux PAM configuration files is assumed. Consult your system or online documentation:
Enable HYPR Authentication for ssh and scp
Follow the instructions below as appropriate for your system.
-
Ubuntu, Debian (
common-auth)-
Add the following line to
/etc/pam.d/common-authbefore the first line containingpam_unix.so:auth [success=3 auth_err=die new_authtok_reqd=ok default=ignore] pam_hypr.so -
Add the following line after the first
pam_deny.soline after the firstpam_unix.soline (referenced above):auth required pam_permit.so -
Linux PAM configuration in
common-authwill most likely result in other commands likesudoinvoking HYPR authentication. HYPR authentication can be disabled forsudoby adding this line inpam_hypr.conf:disabled command sudoNumber Matchsuccess=3signifies the number of lines to skip when HYPR authentication succeeds. The number must equal the number of lines, inclusive, between the firstpam_unix.soline and the firstpam_deny.soline following.
-
-
CentOS, RedHat, Fedora (
sshd)-
Add the following line to
/etc/pam.d/sshdbefore the first occurrence ofauth substack password-auth:auth [success=1 auth_err=die new_authtok_reqd=ok default=ignore] pam_hypr.so -
Add the following line after this same
auth substack password-authinstance:auth required pam_permit.so -
On HYPR authentication failure the above configuration will cause overall authentication (
ssh,scp) failure. If system password authentication is needed as a fallback, change the aboveauth_err=dietoauth_err=ignoreinpam_hypr.so. This can be useful for Troubleshooting.
-
Linux SSH Configuration
Altering ssh core files runs the risk of disabling ssh. Against the contingency that ssh becomes disabled, We recommend connecting via ssh to the server being enabled with the HYPR Linux PAM.
-
Define the following properties in
/etc/ssh/sshd_config, commenting out any pre-existing, conflicting properties of the same name elsewhere in the file, and including in any files included by this file, e.g., in thesshd_config.dsubdirectory.ChallengeResponseAuthentication yes
PubkeyAuthentication no
PasswordAuthentication no
UseDNS no
UsePAM yes -
When changes to this
/etc/ssh/sshd_configfile have been saved, thesshdaemon process (sshd) must be restarted:sudo systemctl restart sshd.serviceSome systems use
ssh.servicerather thansshd.serviceand will require the following format:sudo service ssh restart -
If
sshdis not installed, install it:sudo apt (or sudo yum) install openssh-server
Bypassing HYPR Authentication
Linux SSH Key Authentication
Allow connections via Linux ssh key authentication by adding the following configuration section at the bottom of the /etc/ssh/sshd_config file. The comma-separated list of Linux login names are allowed direct (ssh and scp) ssh key access without HYPR authentication.
Match User ghopper,jclark
PubkeyAuthentication yes
The users ghopper and jclark may ssh into (or scp to/from) the server via ssh keys, if available.
-
If a private
sshkey is loaded (ssh-add) into thessh-agentfor such a user (or if this user specifies thessh -ioption with their privatesshkey file), and; -
if the public
sshkey associated with this privatesshkey is in the serverauthorized_keysfile for this user, and; -
the
authorized_keysfile has 600 or 644 permissions, then; -
the user will be authenticated immediately on
ssh(orscp).
If any of these conditions is not met, HYPR authentication will be invoked.
This can be done for Linux group names rather than login names via an analogous Match Group configuration section, which must be at the end of the authorized_keys file.
Restart the ssh daemon (sshd) for the changes to take effect:
sudo systemctl restart sshd.service
Linux Password Authentication
Bypass HYPR authentication for Linux users and allow them to ssh (or scp) using Linux password authentication instead. Any number of disabled login lines may be included in /etc/security/pam_hypr.conf. For example:
disabled login ghopper
disabled login jclark
The users ghopper and jclark may ssh into (or scp to/from) the service via password authentication, bypassing HYPR authentication.
This can similarly be done for Linux group names rather than login names via analogous disabled group configuration lines.
YubiKey Interoperability (YubiKey Linux PAM)
YubiKeys can be enabled for use with HYPR authentication by using the YubiKey Linux PAM. Follow these instructions to install and configure your YubiKey Linux PAM to work with HYPR authentication via the HYPR Linux PAM. When complete, the use of ssh or scp will challenge the user with HYPR authentication and allow the YubiKey test of user presence (TUP) as a viable method of access.
YubiKey Linux PAM – Installation
Make sure to complete the Installation and the Configuration before proceeding.
Install a working pam_yubico.so shared library into the standard system directory, /usr/lib/security or equivalent.
-
Ubuntu, Debian, and similar
sudo apt install libpam-yubico -
CentOS, Fedora, and similar
sudo yum install pam_yubico -
RedHat 7 and similar
Manually download (viawget) the following packages and install them viarpm.
wget https://dl.fedoraproject.org/pub/epel/7/x86_64/Packages/p/pam_yubico-2.26-1.el7.x86_64.rpm
wget https://dl.fedoraproject.org/pub/epel/7/x86_64/Packages/y/ykclient-2.15-1.el7.x86_64.rpm
wget https://dl.fedoraproject.org/pub/epel/7/x86_64/Packages/y/ykclient-devel-2.15-1.el7.x86_64.rpm
wget https://dl.fedoraproject.org/pub/epel/7/x86_64/Packages/y/ykpers-1.19.0-1.el7.x86_64.rpm
wget https://dl.fedoraproject.org/pub/epel/7/x86_64/Packages/y/ykpers-devel-1.19.0-1.el7.x86_64.rpm
wget https://dl.fedoraproject.org/pub/epel/7/x86_64/Packages/l/libyubikey-1.13-1.el7.x86_64.rpm
wget https://dl.fedoraproject.org/pub/epel/7/x86_64/Packages/l/libyubikey-devel-1.13-1.el7.x86_64.rpm
sudo rpm -i libyubikey-* ykclient-* ykpers-* pam_yubico* -
RedHat 8 and similar
Manually download/install viadnf:
sudo dnf install https://dl.fedoraproject.org/pub/epel/epel-release-latest-8.noarch.rpm
sudo yum install epel-release
sudo yum install pam_yubico -
openSUSE and similar
sudo zypper install pam_yubico -
Kali, Mint, and similar
sudo apt install libpam-yubico
sudo cp /usr/lib/security/pam_yubico.so /usr/lib/x86_64-linux-gnu/security
YubiKey Linux PAM – Configuration
These instructions will configure your YubiKey Linux PAM to work with HYPR authentication via the HYPR Linux PAM. More information on YubiKey Linux PAM configuration can be found here.
-
Ensure your YubiKey is operational.
-
Open a text editor on a computer and click in the text area to give the cursor focus there.
-
Connect the physical YubiKey device to your computer.
-
Touch the contact on the side of the key. This should cause a 44-character string to be generated which looks something like this:
ccccccveebckbvuhthjlhnlvtbunglkhvelbruhhjkbrYubiKeys and VMsUsing a Linux virtual machine (VM), a special setup may be necessary for the VM to recognize a YubiKey device: adding the following properties to the .vmx file:
usb.generic.allowHID = "TRUE"
usb.generic.allowLastHID = "TRUE"See this article on Security Key Testing.
-
-
Get a Yubico API key:
-
Browse to https://upgrade.yubico.com/getapikey
-
Enter your email address in the Email address input box
-
Click to give keyboard focus in the YubiKey OTP input box
-
Connect the physical YubiKey device
-
Touch the contact on the side of the key; a 44-character key fills the input box
-
Check the Terms and Conditions box and click the Get API key button; this generates a Client ID and Secret key
-
Take note of these values to be used later in this configuration (Step 4)
-
-
On the Linux server, create this file (as
sudo):
/etc/yubikey_mappingsAdd a line that looks like this...
ghopper:ccccccveebck…where
ghopperis the Linux login name, andccccccveebck(separated from the login name by a colon) is the first 12 characters output by the YubiKey device (from Step 1, above). This is the fixed, constant value which uniquely identifies your particular YubiKey device. -
Edit the file(s) in
/etc/pam.drepresenting services (commands) for which you want Yubkey-based authentication to be invoked. For example, to enable YubiKey authentication for thesudocommand:-
Edit
/etc/pam.d/sudo, adding this line to the top:auth sufficient pam_yubico.so id=64015 authfile=/etc/yubikey_mappings -
Set the value for the
id(64015 in the above example) to your Client ID from Step 2
-
When invoking the sudo command (using the example from Step 4), something similar to the following displays on the command line:
YubiKey for 'ghopper':
Touch the contacts on your (plugged-in) YubiKey device. And after a brief pause, your sudo command will run successfully.
HYPR and YubiKey Interoperability
-
This example shows the first two lines of the Linux system
/etc/pam.d/sudofile configured for both YubiKey and HYPR authentication:auth sufficient pam_yubico.so id=64098 authfile=/etc/yubikey_mappingsauth sufficient pam_hypr.soWhen executing the
sudocommand, the user will first be prompted for YubiKey authentication. If that succeeds then thesudocommand will be executed; if YubiKey authentication fails, it will fall back to HYPR authentication. If that succeeds thesudocommand will execute; if not, the default Linux password authentication will be invoked. -
This example reverses the above, first trying HYPR authentication, then falling back to YubiKey authentication if that fails:
auth sufficient pam_hypr.soauth sufficient pam_yubico.so id=64098 authfile=/etc/yubikey_mappingsUsing the notes you made in YubiKey Linux PAM—Configuration substitute the
idandauthfilearguments on thepam_yubico.soline above. -
A similar process can be done, by analogy, with other PAM configuration files, e.g.,
/etc/pam.d/sshdor/etc/pam.d/common-auth, as appropriate for your system -
A configuration to require both HYPR and YubiKey authentication might be used.
Testing and Troubleshooting
hypr Utility
Included in the release package for hypr-pam is a command-line utility, hypr, which can be used for basic testing, troubleshooting, and informational purposes. Usage follows.
hypr info
This prints basic information, configuration and otherwise, about the installed hypr-pam.
Example output:
HYPR Linux PAM 1.0.2 / Copyright (c) 2021, HYPR Corporation:
- HYPR Linux PAM library: /usr/lib64/security/pam_hypr.so (OK)
- HYPR Linux PAM stack usages in /etc/pam.d: sshd
- HYPR Linux PAM stack example: /etc/pam.d/hypr-example
- HYPR Linux PAM configuration example: /etc/security/pam_hypr.conf-example
- HYPR Linux PAM configuration: /etc/security/pam_hypr.conf
- HYPR Linux PAM enabled: true
- HYPR Linux PAM access-token: b*******4
- HYPR Linux PAM base-url: https://highlandsbank.com (OK)
- HYPR Linux PAM polling time: 60 seconds
- HYPR Linux PAM polling interval: 2 seconds
- HYPR Linux PAM timeout: 30000 milliseconds
- HYPR Linux PAM endpoint-path: /rp/api/oob/client/authentication
- HYPR Linux PAM app-id: fIDO2Local
- HYPR Linux PAM git repo: git@g.hypr.com:david.michaels/hypr-pam.git
- HYPR Linux PAM git branch: master
- HYPR Linux PAM git commit: 774f1d58e6280c38f17d21605155f26a8a15454f
- HYPR Linux PAM git date: 2021-05-28 07:02:02-0400
- HYPR Linux PAM build date: 2021-05-28 08:18:13-0400
- HYPR Linux PAM build operating system: Red Hat Enterprise Linux 8.3 (Ootpa)
- HYPR Linux PAM build architecture: x86_64
- Operating system: Red Hat Enterprise Linux 8.3 (Ootpa) / rhel -> fedora
- Architecture: x86_64
- SELinux: enabled
- SELinux NIS: enabled
When using x86_64 architecture, the (OK) at the end of the HYPR Linux PAM library line indicates pam_hypr.so can successfully be loaded as a PAM shared library; if there is a problem here, it displays (unloadable). Likewise, the (OK) at the end of the HYPR Linux PAM base-url line indicates the API is reachable.
Command-line options are:
| Option | Description |
|---|---|
--verbose | Prints extra information, and also tries to ping the HYPR authentication service as defined by the api_base_url in the pam_hypr.conf configuration file. |
--noping | Prevents the ping of the HYPR authentication service as defined by the api_base_url in the pam_hypr.conf configuration file. |
hypr auth
Invokes the HYPR authentication process, standalone, outside of any PAM or SSH context. In the absence of configuration-related options, it reads the configuration from the /etc/security/pam_hypr.conf configuration file.
Command-line options are:
| Option | Description |
|---|---|
--login name | Uses the specified login name rather than the current login name of the user invoking this command. |
--username name | Uses the specified HYPR username rather than the username associated with the login name, as defined by the login/username mapping in the pam_hypr.conf file. |
--access-token token | Uses the specified access-token rather than the one defined by access_token in the pam_hypr.conf file. |
--base-url url | Uses the specified base-url rather than the one defined by api_base_ful in the pam_hypr.conf file. |
--app-id id | Uses the specified app-id rather than the one defined by app_id in the pam_hypr.conf file. |
--config file | Uses the specified file as the configuration file from which to read properties for this command rather than using the defined pam_hypr.conf file in /etc/security. |
--verbose | Prints verbose output. |
--debug | Prints full debugging information, including the JSON payload in the requests and responses. |
hypr pam
Invokes the HYPR authentication process in the context of a simple PAM-enabled application, but outside any ssh context. The configuration is read from the installed pam_hypr.conf configuration file in /etc/security.
Example output:
HYPR Linux PAM mini-test command-line application ...
Calling pam_start (app: hypr-example, login: ghopper)
Back from pam_start (0)
Calling pam_authenticate
INFO: HYPR logging to stderr per 'debug' in pam.d config
INFO: HYPR authentication command name: 'hypr-example'
INFO: HYPR authentication cannot get remote host name.
INFO: Reading HYPR config and looking for HYPR username for 'dmichaels' login: /etc/security/pam_hypr.conf
INFO: Successfully read HYPR config: /etc/security/pam_hypr.conf
INFO: HYPR access_token: REDACTED
INFO: HYPR api_base_url: https://highlandsbank.com
INFO: HYPR api_auth_endpoint: /rp/api/oob/client/authentication
INFO: HYPR app_id: fIDO2Local
INFO: HYPR poll_max_time_seconds: 60
INFO: HYPR poll_interval_seconds: 2
INFO: HYPR timeout: 30000 ms
INFO: HYPR username for login (ghopper) found: grace.hopper@hb.com
INFO: HYPR authenticating username: grace.hopper@hb.com
DEBUG: HYPR back from authenticating username: grace.hopper@hb.com
INFO: Done authenticating user: OK
DEBUG: pam_sm_authenticate exit: 0
Back from pam_authenticate (0)
Calling pam_end
Back from pam_end (0)
Running test PAM-enabled authentication app (does nothing but print this line): OK
Troubleshooting
If system password authentication is needed as a fallback while testing or troubleshooting, change the auth_err=die to auth_err=ignore in the file pam_hypr.so. A full description of how to do this can be found under Enable HYPR Authentication or SSH
HYPR Linux PAM logs are in /var/log. The relevant files vary by system:
-
Ubuntu, Debian, and similar
-
auth.log
-
syslog
-
-
CentOS, RHEL, and similar
-
secure
-
messages
-
On systems employing SELinux (CentOS, RedHat, Fedora, and similar), HYPR authentication (HTTPS) API calls may be blocked when invoked by the HYPR Linux PAM from an ssh/scp context. HYPR authentication will appear not to work on ssh/scp and, given the above configuration, normal Linux password authentication will be invoked instead.
To diagnose blocked API calls:
-
Inspect the (
secure) log file for the following:pam_hypr ERROR: Did not authenticate user (null-response) -
Inspect the (
messages) log file for the following:If you want to allow nis to be enabled, you must tell SELinux about this by enabling the 'nis_enabled' boolean.If this message is found, it may be necessary to allow these HTTPS calls explicitly from a PAM and
sshcontext. -
Check the status of the SELinux option
nis_enabledcontrolling this.-
Execute the following:
sudo semanage boolean -l | grep nis_enabledIf
nisis disabled, it will display the following:nis_enabled (off, off) -
If it is disabled, enable it:
sudo setsebool -P nis_enabled 1 -
Execute the above
semanagecommand and it will now yield:is_enabled (on, on)
-
If the semanage and/or setsebool commands are not installed, run the following to install them:
sudo yum install policycoreutils-python-utils
The hypr info command prints the following if the nis_enabled option is disabled:
SELinux: enabled
SELinux NIS: disabled
WARNING: SELinux seems to be in place and NIS is disabled.
Possibly problematic for ssh with HYPR authentication.
Can be enabled using: sudo setsebool -P nis_enabled 1
Can be viewed using: sestatus -b | grep nis_enabled
On some systems the required libcurl.so shared library file may not be found. This will prevent authentication from working. The hypr info command output may include something like this:
- HYPR Linux PAM libcurl: dynamic (not loadable)
- WARNING: Required libcurl.so shared library cannot be found or loaded.
It looks like there is actually one here: /lib64/libcurl.so.4
You can create a symbolic link to it like this:
> sudo ln -s /lib64/libcurl.so.4 /lib64/libcurl.so
Or add this line to your config file: /etc/security/pam_hypr.conf
> libcurl /lib64/libcurl.so.4
As an alternate workaround to the symbolic link, the full path to the libcurl.so file (whatever its name) can be specified in pam_hypr.conf.
Flowchart
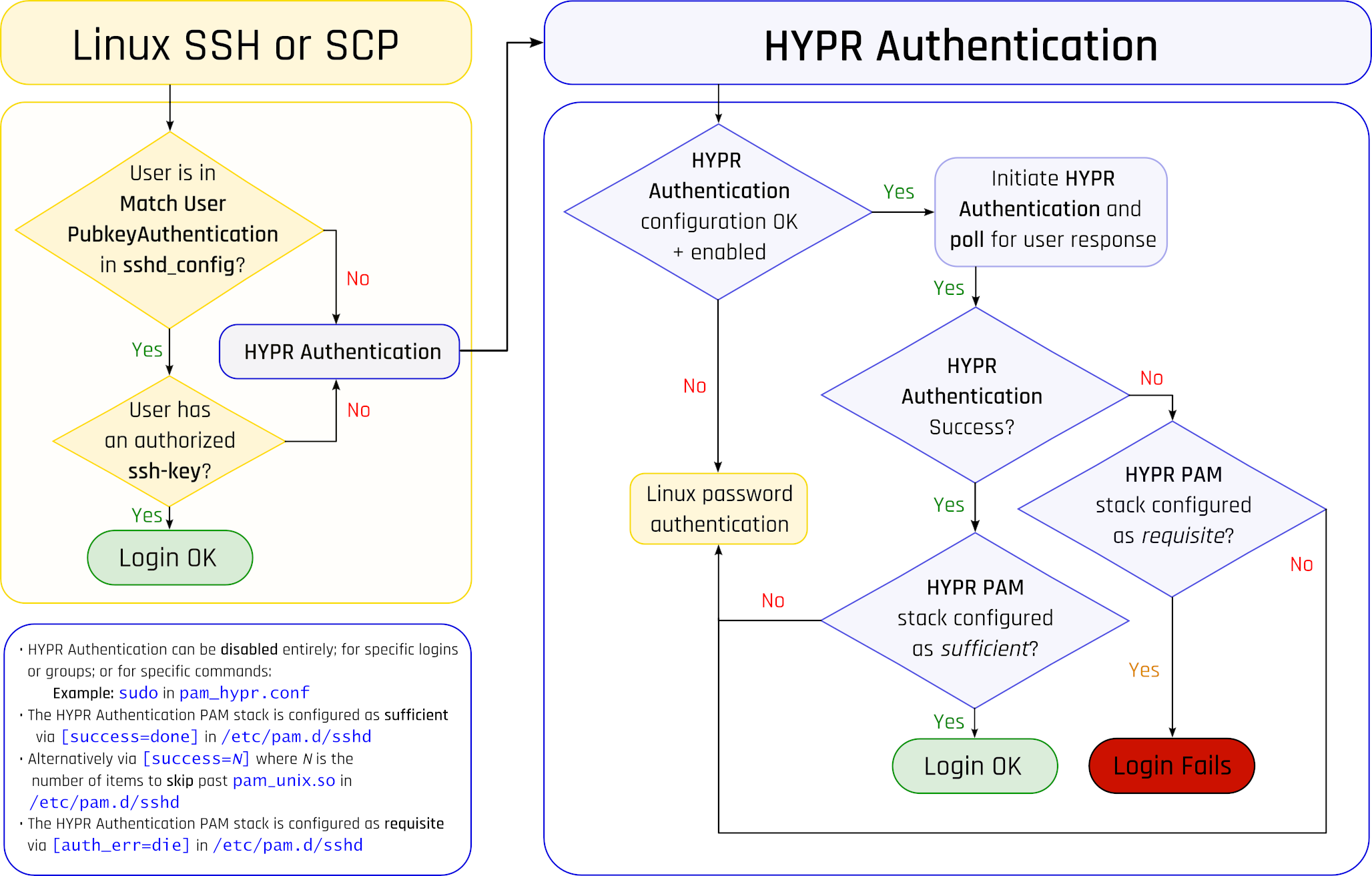
Issues
Centrify Interoperability
During HYPR Linux PAM setup walkthrough with Point72 (on 2021-05-04), HYPR authentication was prevented on ssh when using the hostname. After proper setup, HYPR authentication was not invoked at all; neither was normal Linux password authentication invoked (and no ssh keys were involved). Rather, users were logged in directly. Using the IP address instead, ssh did properly go through the HYPR authentication PAM.
Building the HYPR Linux PAM
To build HYPR Linux PAM from source (under the BSD license):
Building from source (vanilla C) code requires the Linux autotools system, as described below.
The versions listed here may differ from the latest available version. We will represent the filename version in this document with x.y-z where the version belongs.
Before building and installing the HYPR Linux PAM these system dependencies must be satisfied. As always, it’s prudent before any installation to get the latest system updates for your system via sudo apt update or sudo yum update or sudo zypper update, as appropriate.
- **Ubuntu, Debian, Mint, Kali, and similar**
`sudo apt install -y gcc make automake autoconf libtool`
`sudo apt install -y libcurl4-openssl-dev libssl-dev libpam0g-dev`
- **RedHat, CentOS, Fedora, and similar**
`sudo yum install -y gcc make automake autoconf libtool`
`sudo yum install -y libcurl-devel openssl-devel pam-devel`
- **openSUSE and similar**
`sudo zypper install -y gcc make automake autoconf libtool`
`sudo zypper install -y libcurl-devel openssl-devel pam-devel`
Build the Shared Library
-
Copy the HYPR Linux PAM code to the target Linux server
-
Change to the
hypr-pamdirectory and use the standard Linux autotools syntax to build:autoreconf -iv
./configure
make
make prefix=/usr install-
This builds the shared library
pam_hypr.so, then copies it to:-
Ubuntu, Debian and similar
/usr/lib/x86_64-linux-gnu/security -
CentOS, RedHat and similar:
/usr/lib64/security -
openSUSE and similar
/lib64/security
Note the location of this security folder for your OS; it will be referred to in this document as
usr/lib/security. -
-