Passwordless Enforcement
Configure HYPR to enforce logins without requiring a password as long as HYPR Passwordless client is installed on the workstation. This feature can enable or remove the option to enter a password for workstation login and for workstation unlock.
Passwordless Login Enforcement works provided the user has a valid HYPR pairing. If the user removes all pairings, the password login is enabled again by default.
Passwordless for Windows
These processes require Administrator access to the Windows Group Policy Editor or Registry Editor.
Use HYPR Variables During Installation
Configuration parameters can be set during the manual client installation process. See the article on Manual Installation for HYPR Passwordless for details on how to configure the installation to enforce passwordless unlock and login in your environment.
Smart Card Authentication with the Group Policy Object (GPO)
In a smart card deployment, additional Group Policy settings can be used to enhance ease-of-use or security.
Method 1: GPO
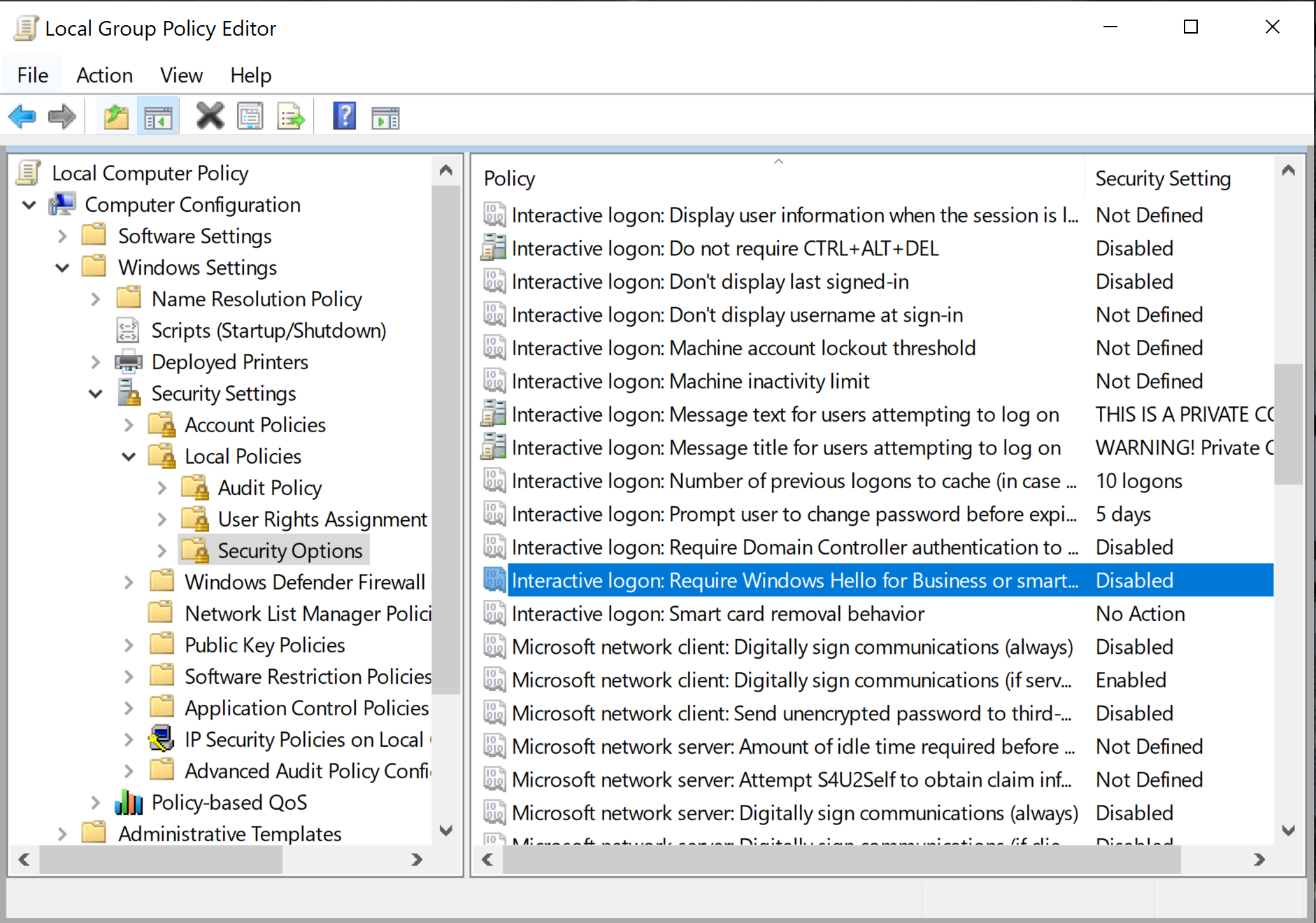
The following smart-card-related Group Policy settings are in the Local Group Policy Editor under Computer Configuration > Windows Settings > Security Settings > Local Policies > Security Options.
| Group Policy Setting and Registry Key | Default | Description |
|---|---|---|
Interactive logon: Require smart cardscforceoption | Disabled | This security policy setting requires users to sign in to a computer by using a smart card. Enabled: Users can sign in to the computer only by using a smart card. Disabled: Users can sign in to the computer by using any method. |
Method 2: Registry Editor
-
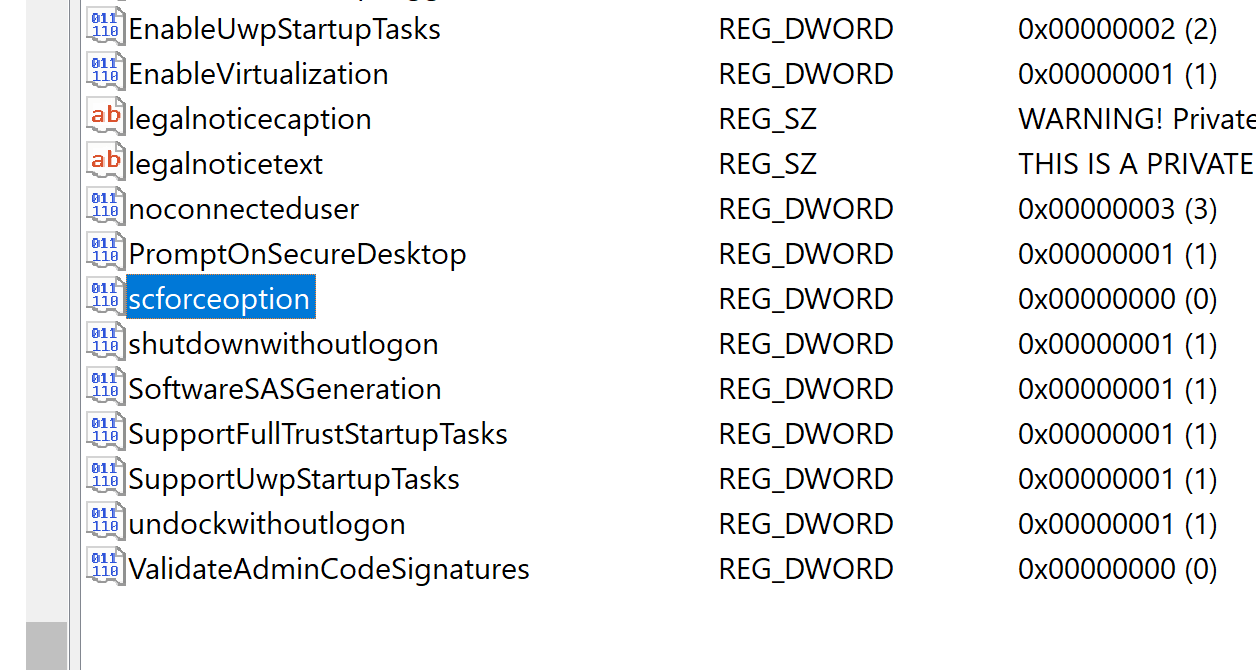
Locate the registry path:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System. -
Look for the registry key
scforceoption. -
Change the value to 1 to Enable or 0 to Disable it.
-
This change will take effect during next session, which is created during log off, switching users, or rebooting.
When you are finished, only a trusted smart card or HYPR Passwordless client can be used to log into the Windows machine.
Disable Password Login Using Registry Editor
-
Check the credential provider and find its CLSID used by last logged on.
-
Open Registry Editor, and then navigate to the key
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\LogonUI -
On the right side, navigate to the String Value
LastLoggedOnProvider, whose data is the CLSID of the credential provider, as shown here: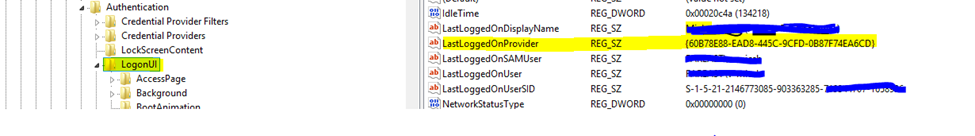
-
-
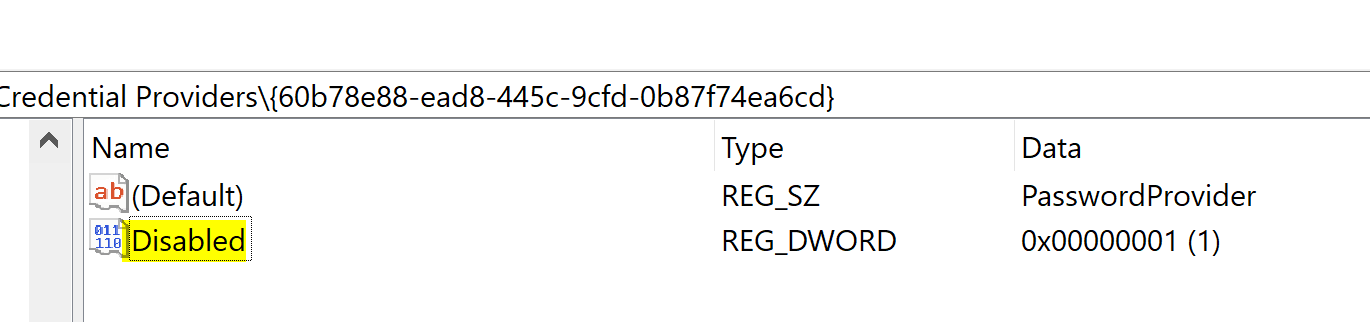
In Registry Editor, navigate to the registry key
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\ CurrentVersion\Authentication\Credential Providers. -
Right-click on the CLSID of the provider, select New -> DWORD (32-bit) Value, then enter the Name Disabled. After that, modify the Data value to 1.
-
The provider will be disabled on the next session which is created during logoff, switching to another user, or reboot.
Password Login will now be disabled on the Windows Logon screen.
Disable Credential Provider Login Using GPOs
-
To hide the default Microsoft Windows credential providers after installation of HYPR Passwordless, a Windows Group Policy setting must be configured using either the local group policy editor (
gpedit.msc) or the group policy management console (gpmc.msc):-
Modify an existing group policy or create a new group policy and go to the Exclude credential providers setting: Computer Configuration | Policies | Administrative Templates | System | Logon | Exclude credential providers
-
Open the Properties of the group policy setting and set the policy to Enabled
-
-
Use the Exclude the following credential providers field to exclude specific credential providers. Enter the comma-separated CLSIDs for multiple credential providers to be excluded from use during the authentication process. HYPR requires the smart card credential provider to be available.
-
On a Windows 10 system with the HYPR Passwordless client installed, Windows Password Provider appears next to the HYPR Logon. Smart Card credential provider can be excluded from the login interface using the following string:
\{8FD7E19C-3BF7-489B-A72C-846AB3678C96\}Credential Provider CLSID Smartcard Reader Selection Provider {1b283861-754f-4022-ad47-a5eaaa618894} Smartcard WinRT Provider {1ee7337f-85ac-45e2-a23c-37c753209769} PicturePasswordLogonProvider {2135f72a-90b5-4ed3-a7f1-8bb705ac276a} GenericProvider {25CBB996-92ED-457e-B28C-4774084BD562} NPProvider {3dd6bec0-8193-4ffe-ae25-e08e39ea4063} CngCredUICredentialProvider {600e7adb-da3e-41a4-9225-3c0399e88c0c} PasswordProvider {60b78e88-ead8-445c-9cfd-0b87f74ea6cd} PasswordProvider/LogonPasswordReset {8841d728-1a76-4682-bb6f-a9ea53b4b3ba} FaceCredentialProvider {8AF662BF-65A0-4D0A-A540-A338A999D36F} Smartcard Credential Provider {8FD7E19C-3BF7-489B-A72C-846AB3678C96} Smartcard Pin Provider {94596c7e-3744-41ce-893e-bbf09122f76a} WinBio Credential Provider {BEC09223-B018-416D-A0AC-523971B639F5} IrisCredentialProvider {C885AA15-1764-4293-B82A-0586ADD46B35} PINLogonProvider {cb82ea12-9f71-446d-89e1-8d0924e1256e} NGC Credential Provider {D6886603-9D2F-4EB2-B667-1971041FA96B} CertCredProvider {e74e57b0-6c6d-44d5-9cda-fb2df5ed7435} WLIDCredentialProvider {F8A0B131-5F68-486c-8040-7E8FC3C85BB6} -
To check for additionally installed third-party credential providers, open the registry and browse to the following location and look for the CLSID:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\Credential ProvidersHidden ConnectionsHiding credential providers via group policy will also affect UAC and Run-as authentication dialog boxes.
Enabling Exclude Credential Provider will allow disabling password-based login on the machine level.
Passwordless for macOS
Passwordless enforcement works for local accounts, but not domain-joined Mac workstations.
The configuration parameter that controls these features (AllowPasswordForPairedUsers for Logins; AllowPasswordUnlockForPairedUsers for Unlocking) must be defined either at installation time or as part of the .plist configuration setting. The parameters are called and enabled by default (set to true). When disabled (false), passwords won't be allowed by paired users.
Also see Configuration Parameters.
If FileVault auto-login is not disabled, it's not possible to achieve a passwordless login experience, as the system will automatically pass the FileVault PIN as the login password. We recommend administrators only enable this setting if FileVault auto-login is disabled.
Administrators should make sure they have recovery mechanisms in place for their users before enabling this feature - an IT controlled local account, or a way to push .plist settings to disable it (e.g., JAMF)
MacOS's Fast User Switching feature can be used to bypass this restriction, as it allows switch to another user, thereafter providing a password. In order to achieve a more complete passwordless experience and remove this risk, administrators are advised to disable this feature either using the local settings (using the command shown here) or through a mobile device manager (MDM) such as JAMF.
defaults write /Library/Preferences/.GlobalPreferences MultipleSessionEnabled -bool 'NO'