Resolving Error 0x00000BB at Login
Background
The HYPR Passwordless client utilizes a Windows credential provider to perform X.509 certificate-based client authentication to log the user in to the Windows desktop without a password. Microsoft documentation refers to this as “smart card logon,” because this type of authentication is typically associated with physical cards such as CAC and PIV cards used by the federal government. In the case of HYPR Passwordless, we have a virtual smart card.
Microsoft Certificate Services must be properly configured to ensure HYPR Passwordless can function properly.
Issue Description
If a client experiences a situation where the HYPR Mobile App is spinning and/or timing out during a desktop authentication, it could be a misconfiguration of the Microsoft Certificate Services. Use the Windows Event Viewer (to launch the Event Viewer, just hit Start, type “Event Viewer” into the search box, and then click the result) on the client desktop to look for the following conditions:
-
Go to Windows Logs > Security and look for error The request is Not Supported and status Reported authentication failure. Status=0xC00000BB
-
The following error may be seen in Kerberos event logs on the Workstation when attempting to launch:
0x10 - KDC_ERR_PADATA_TYPE_NOSUPP: KDC has no support for padata type
Smart card logon is being attempted and the proper certificate cannot be located. This can happen because the wrong certification authority (CA) is being queried or the proper CA cannot be contacted.- Known Error Codes: Status=0xC00000BB or 0x10 - KDC_ERR_PADATA_TYPE_NOSUPP
Steps to Reproduce
Undo the Resolution steps below and try to log on to the desktop with WFA.
Resolution
The following conditions must be met:
-
The Domain Controller certificate must be configured for smart card users; this is a setting in the Domain Controller Authentication certificate template
-
The Domain Controller Authentication certificate must exist on all the domain controllers; if not, you must enroll a new certificate
Verify the Smart Card Is Configured into the Domain Controller Authentication certificate Template
-
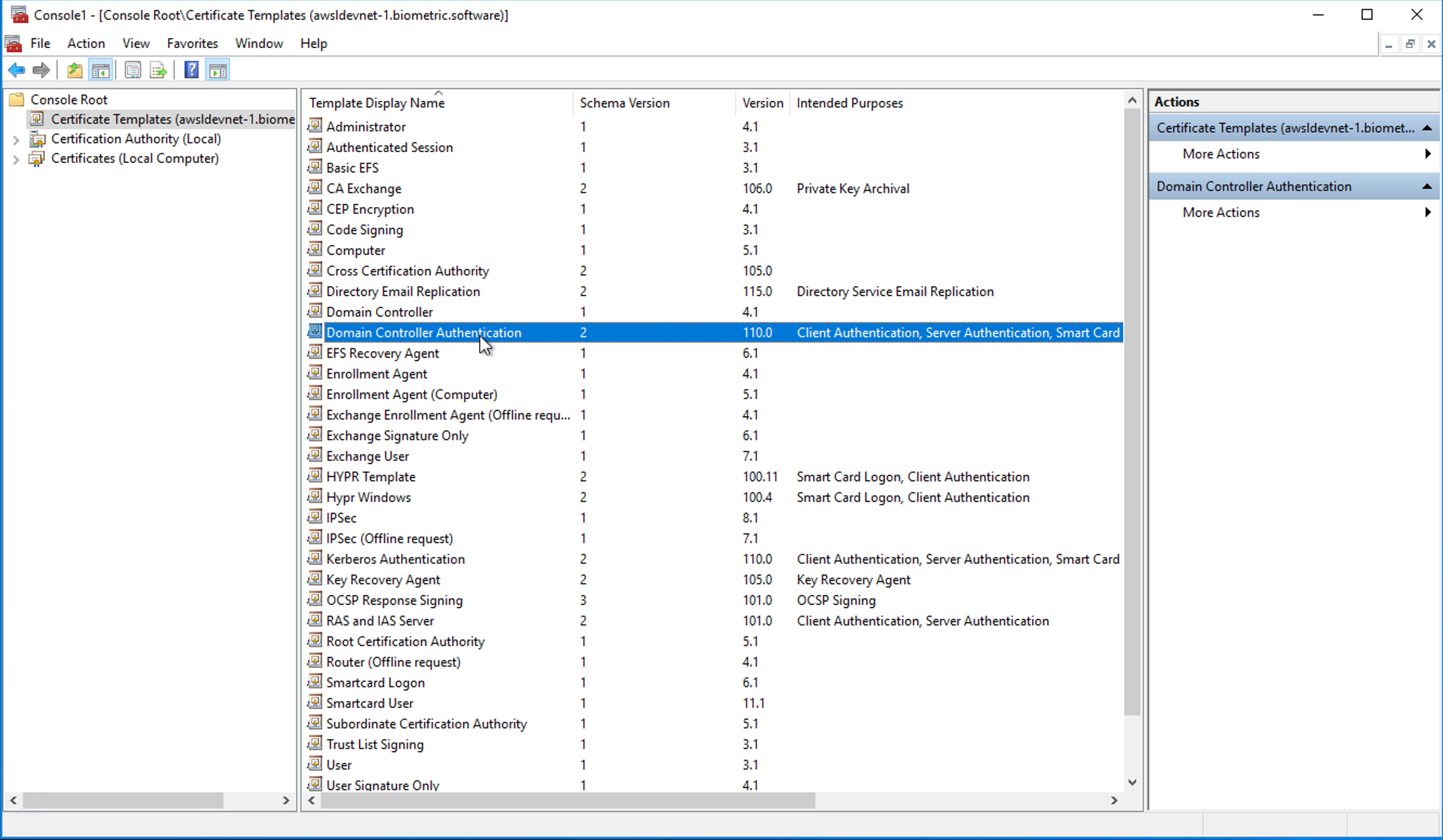
On the domain controller, open mmc and add a new snap-in for the Certificate Templates.
-
Select Certificate Template.
-
Double-click Domain Controller Authentication to open the configuration panel.
-
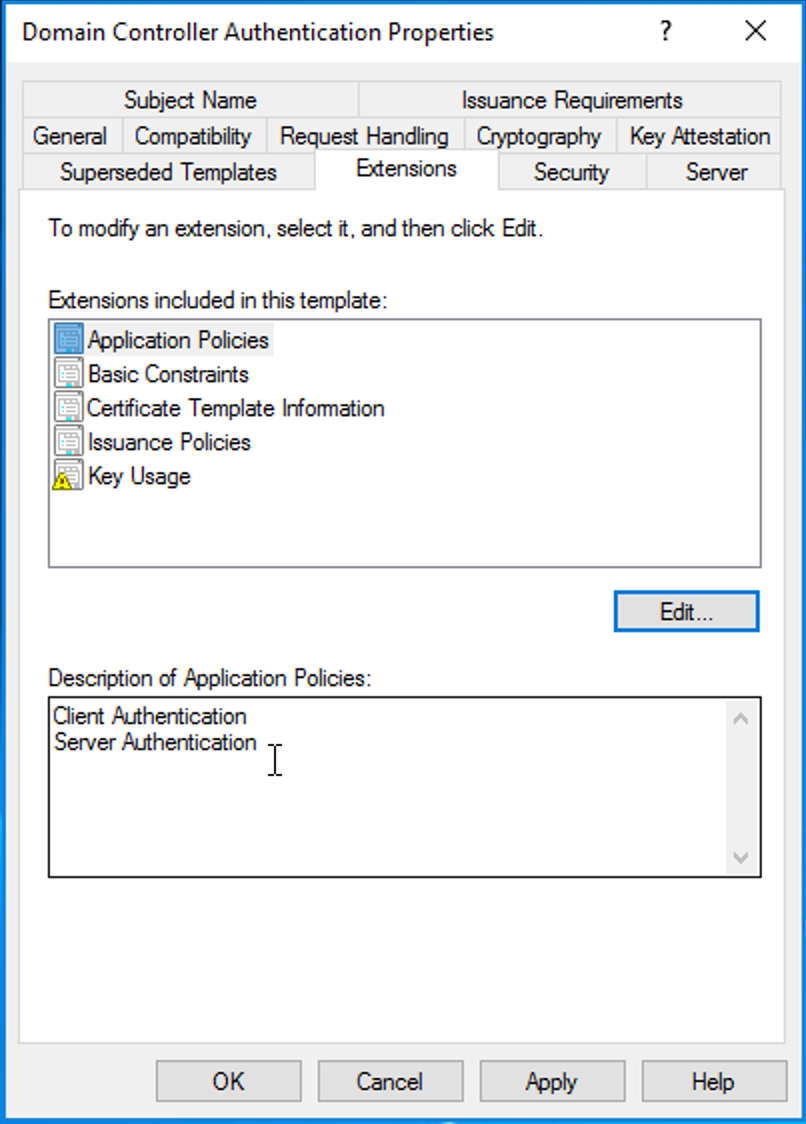
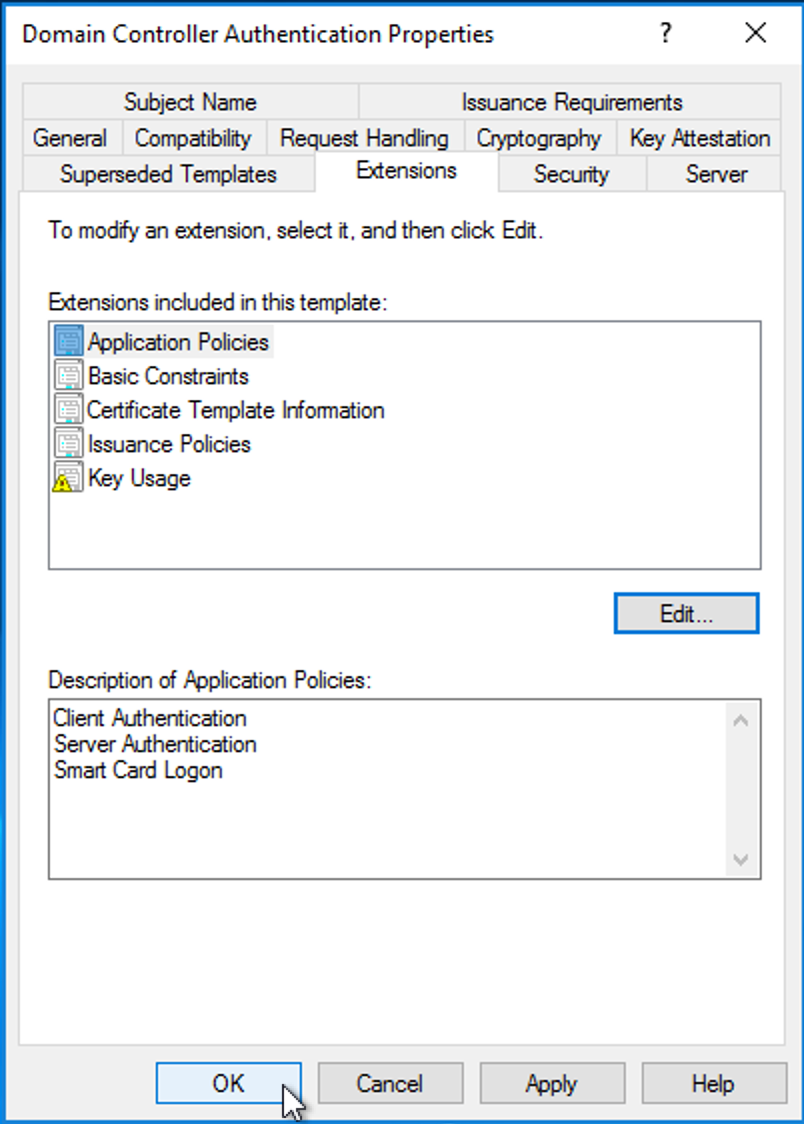
Select the Extensions tab.
-
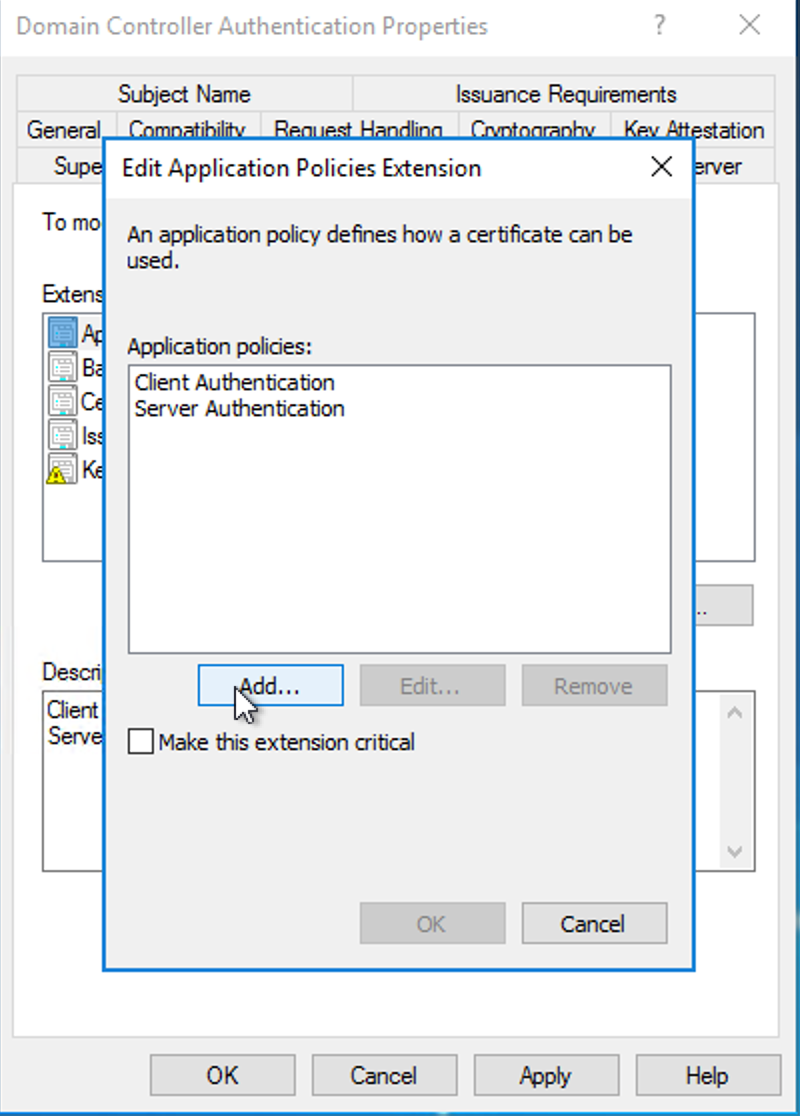
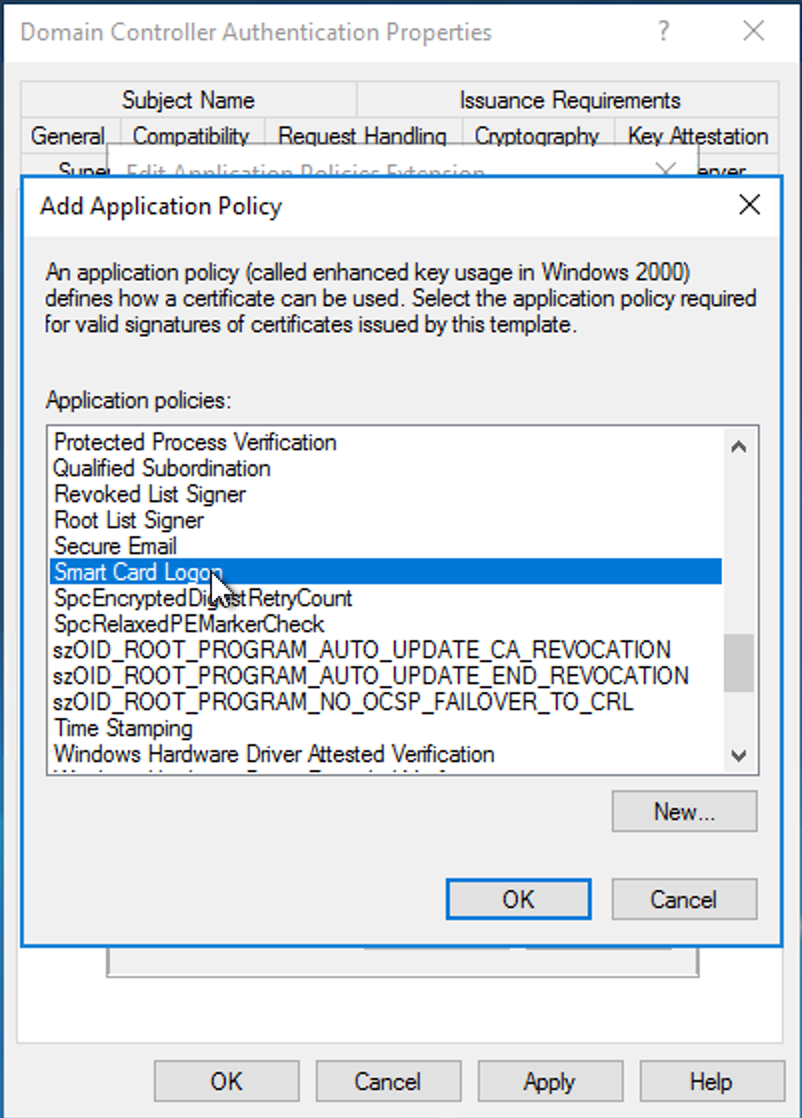
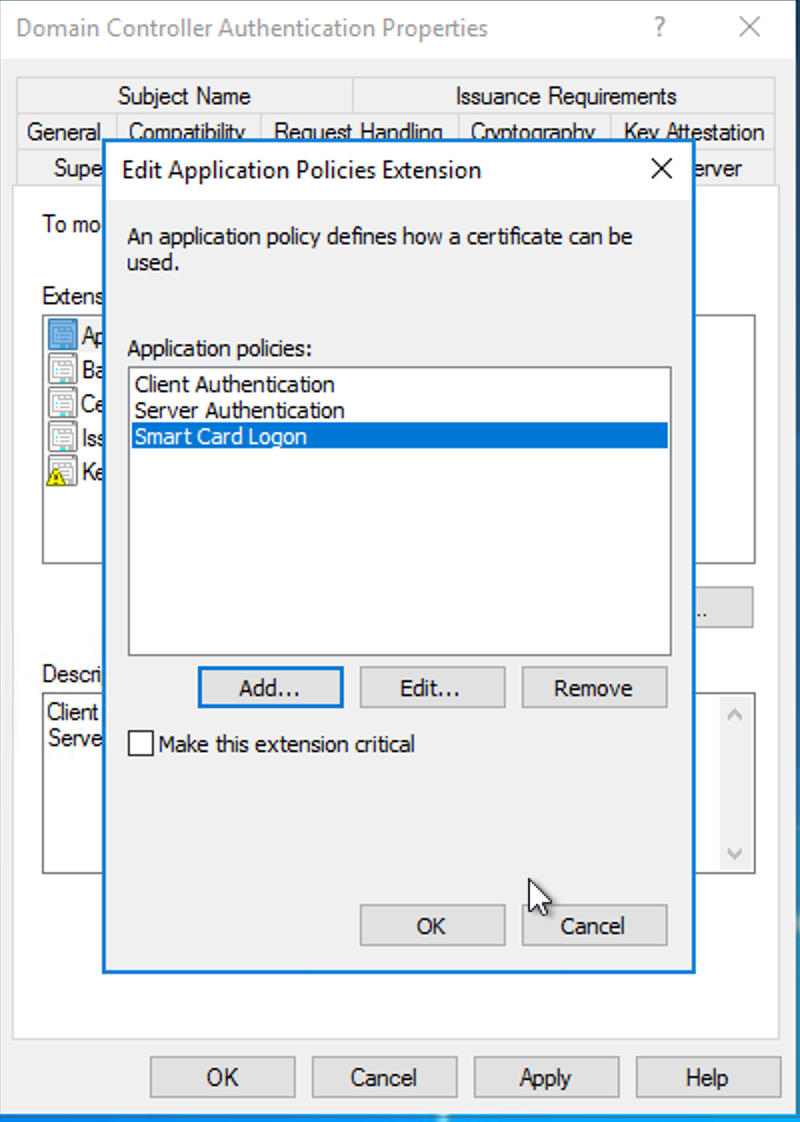
Note whether Description of Application Policies contains Smart Card Logon. If not, click Edit…, then click Add….
-
Select Smart Card Logon, then click OK.
-
Click OK to close the Edit dialog.
-
Click OK to finish.
To Enroll a New Certificate on the Domain Controller
-
On the domain controller, open mmc:
-
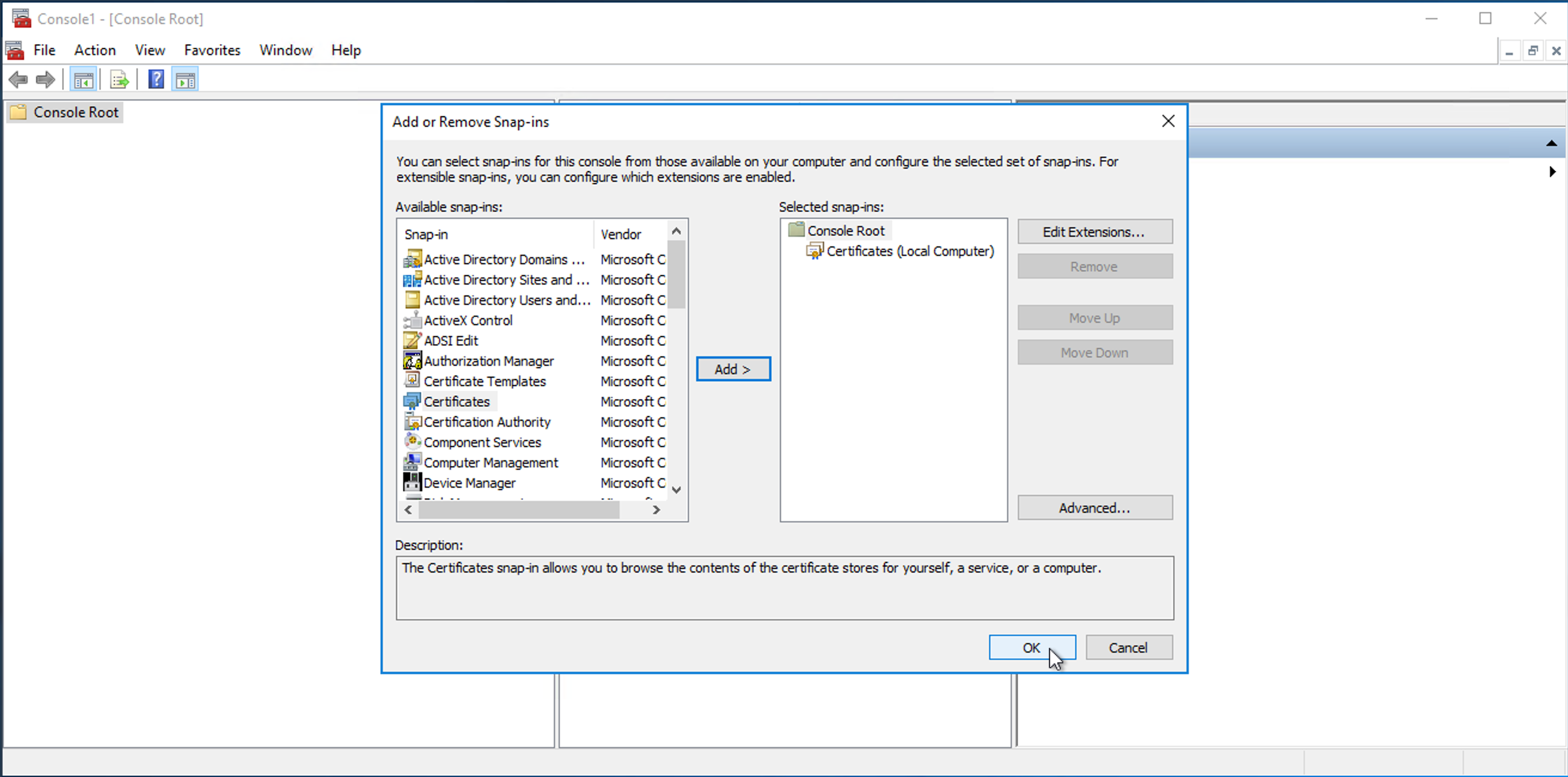
Open File > Add/Remove Snap-in…:
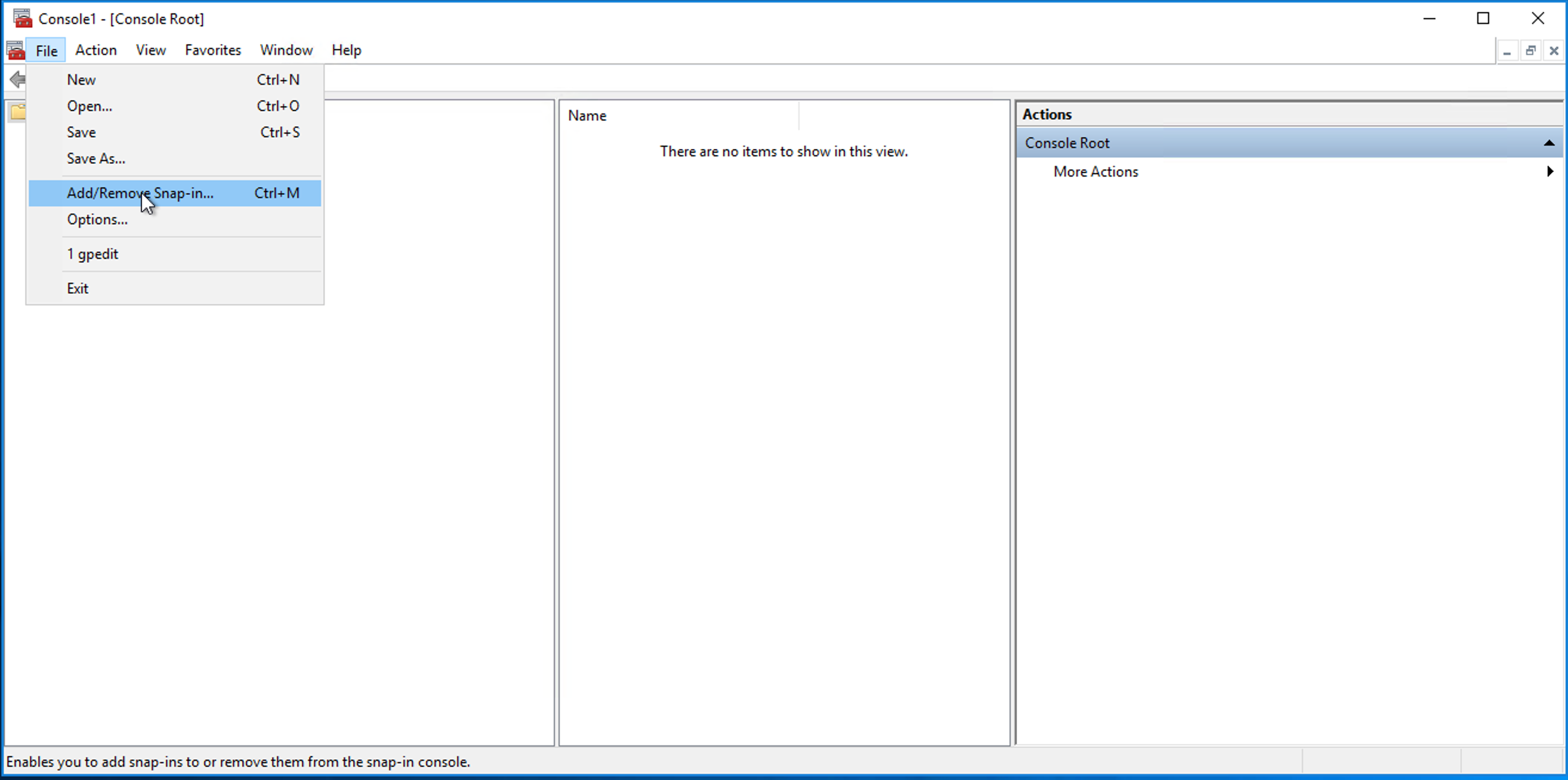
-
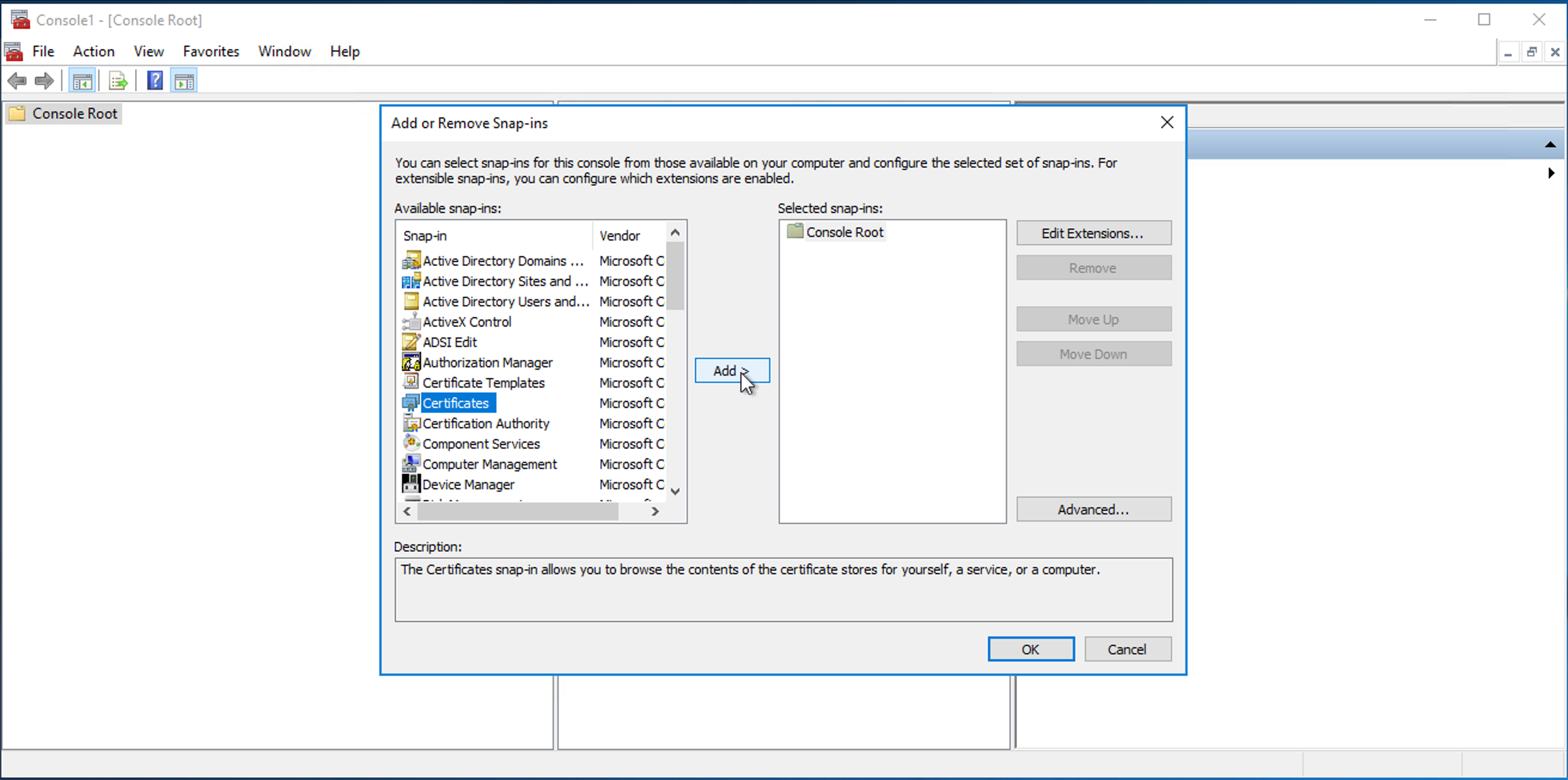
Select Certificates.
-
Click Add, then select Computer account and click Next.
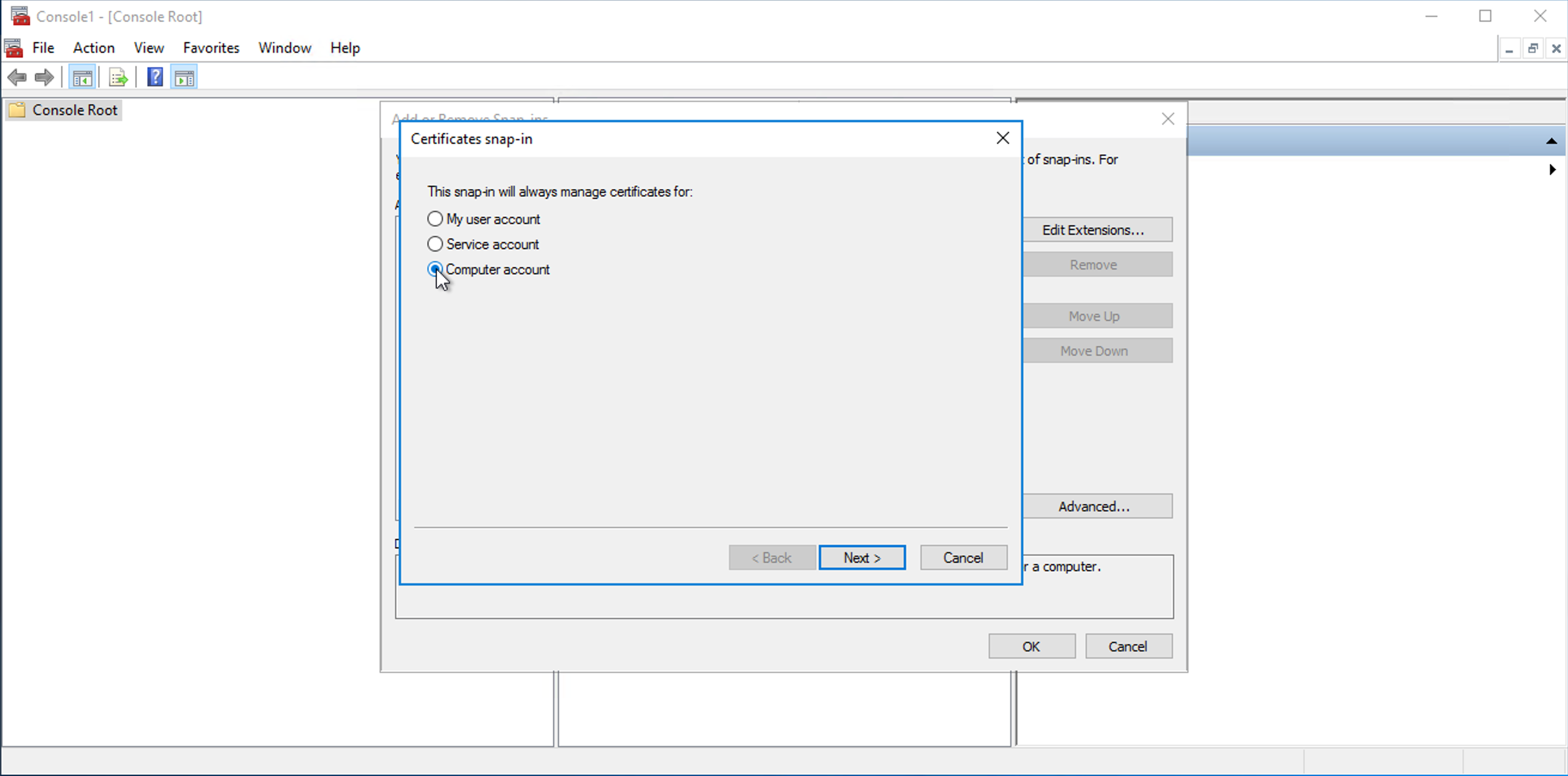
-
Complete the wizard.
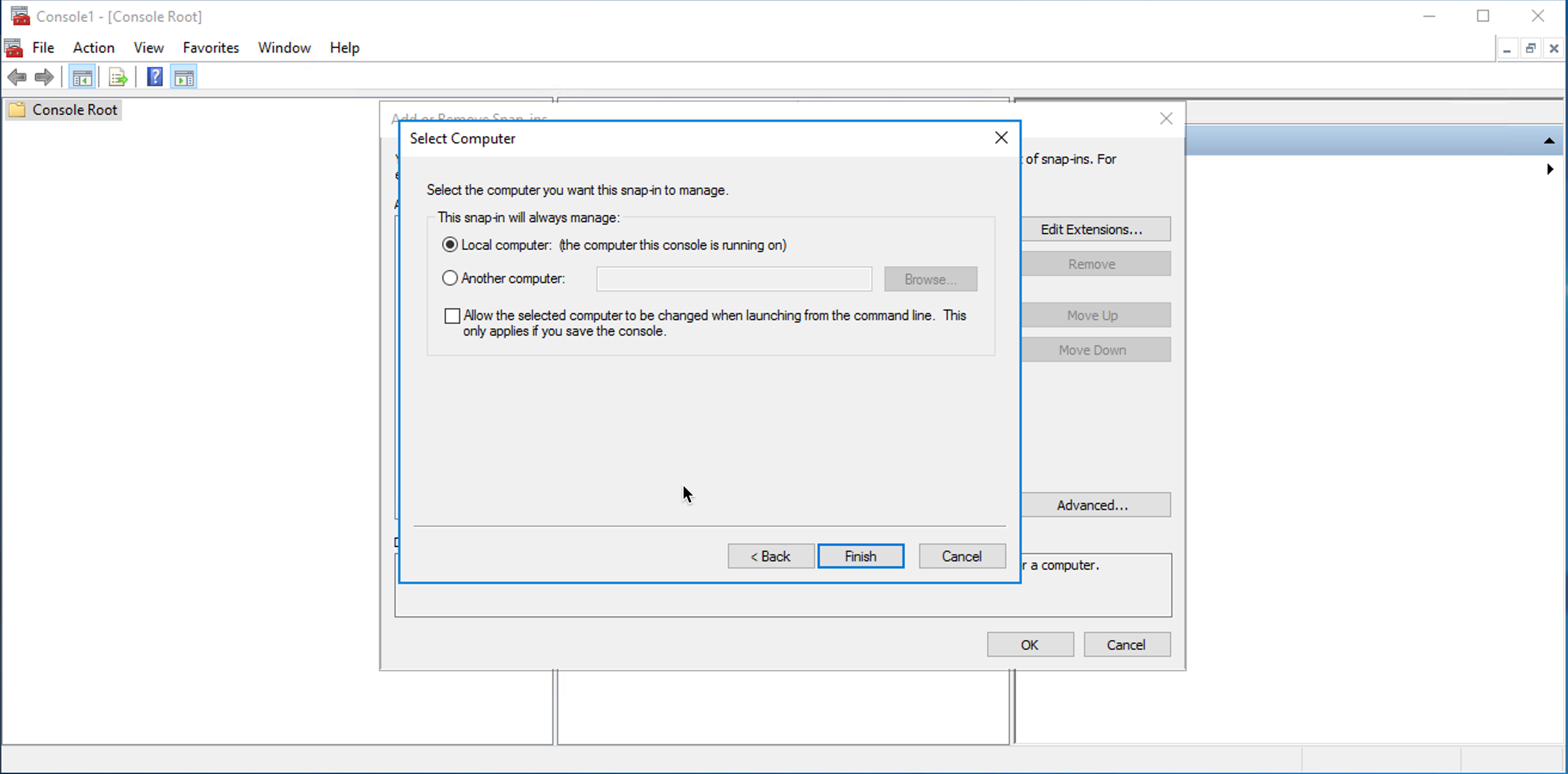
-
Click OK to finish adding the snap-in.
-
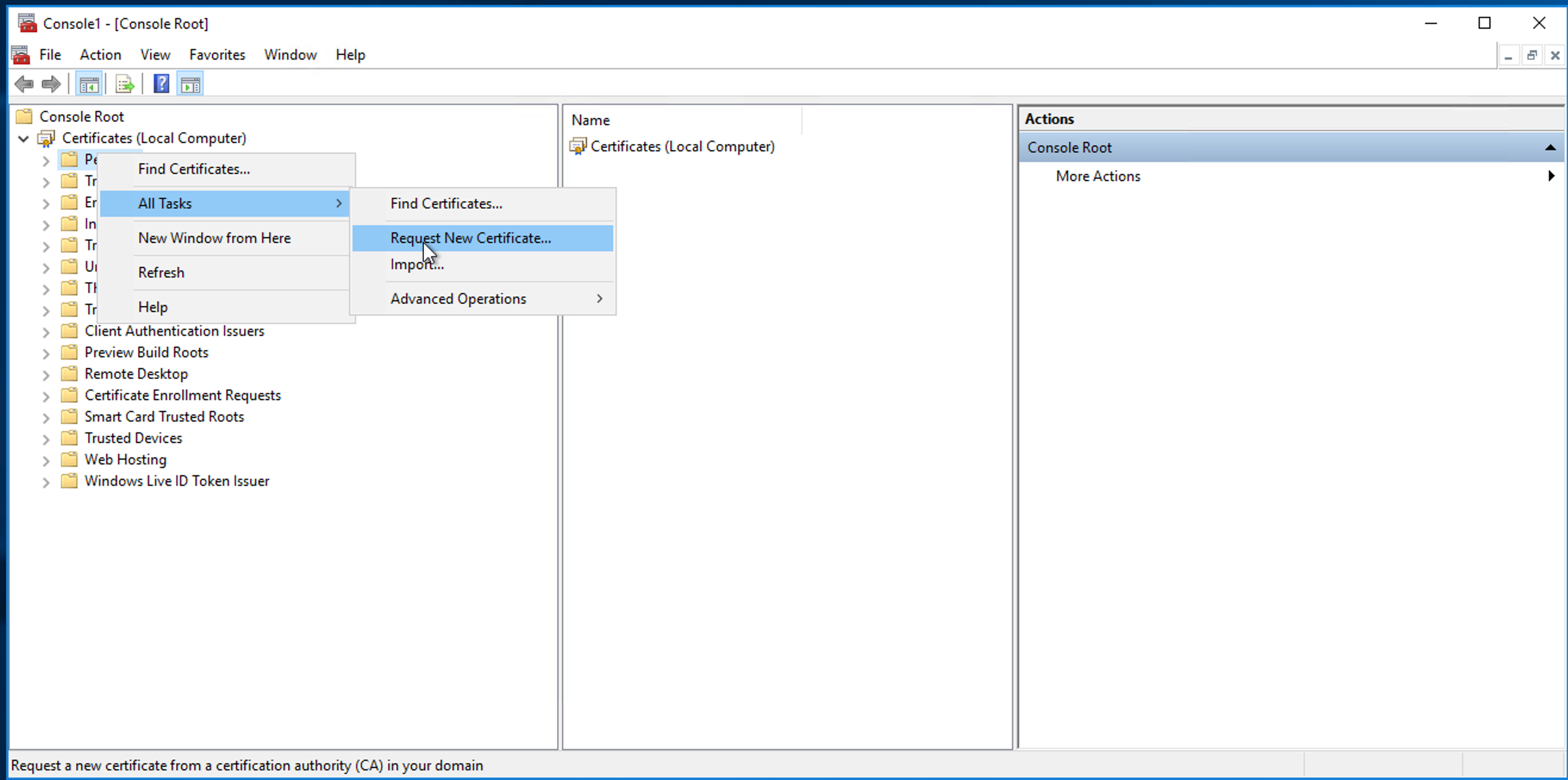
Expand Certificates (Local Computer).
-
Right-click Personal, then expand All Tasks > Request New Certificate.
-
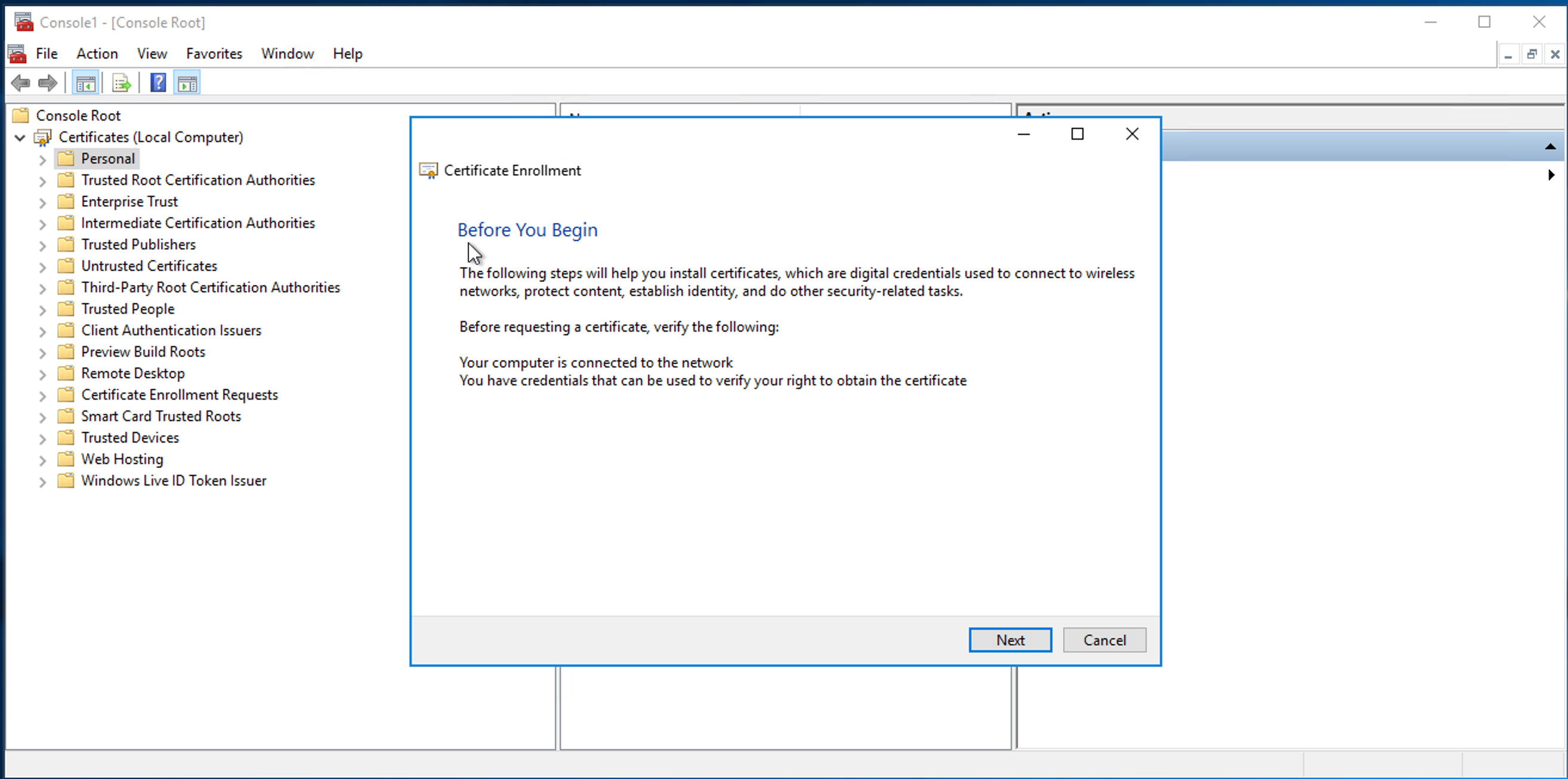
Click Next.
-
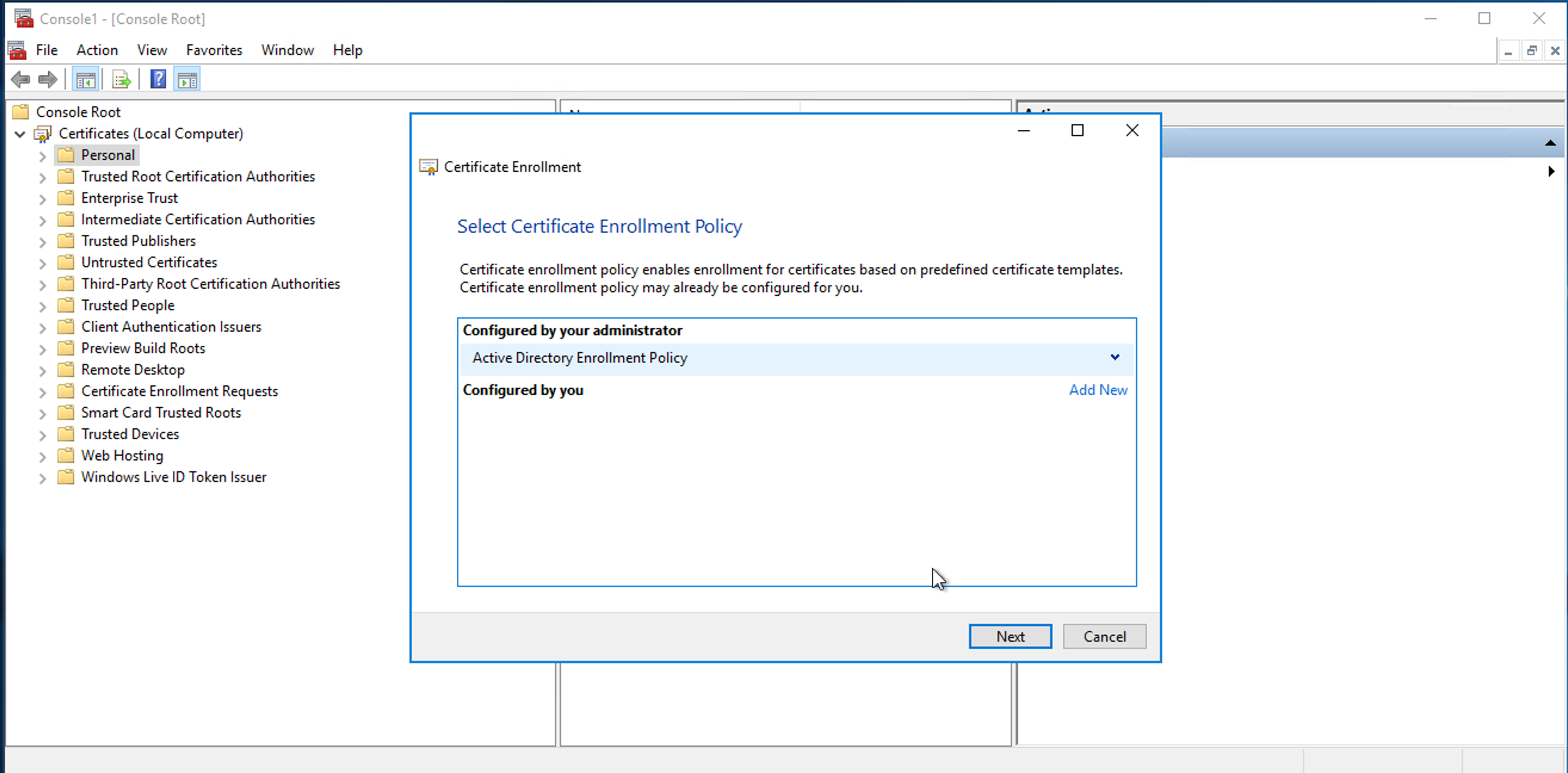
Click Next, then Active Directory Enrollment Policy.
-
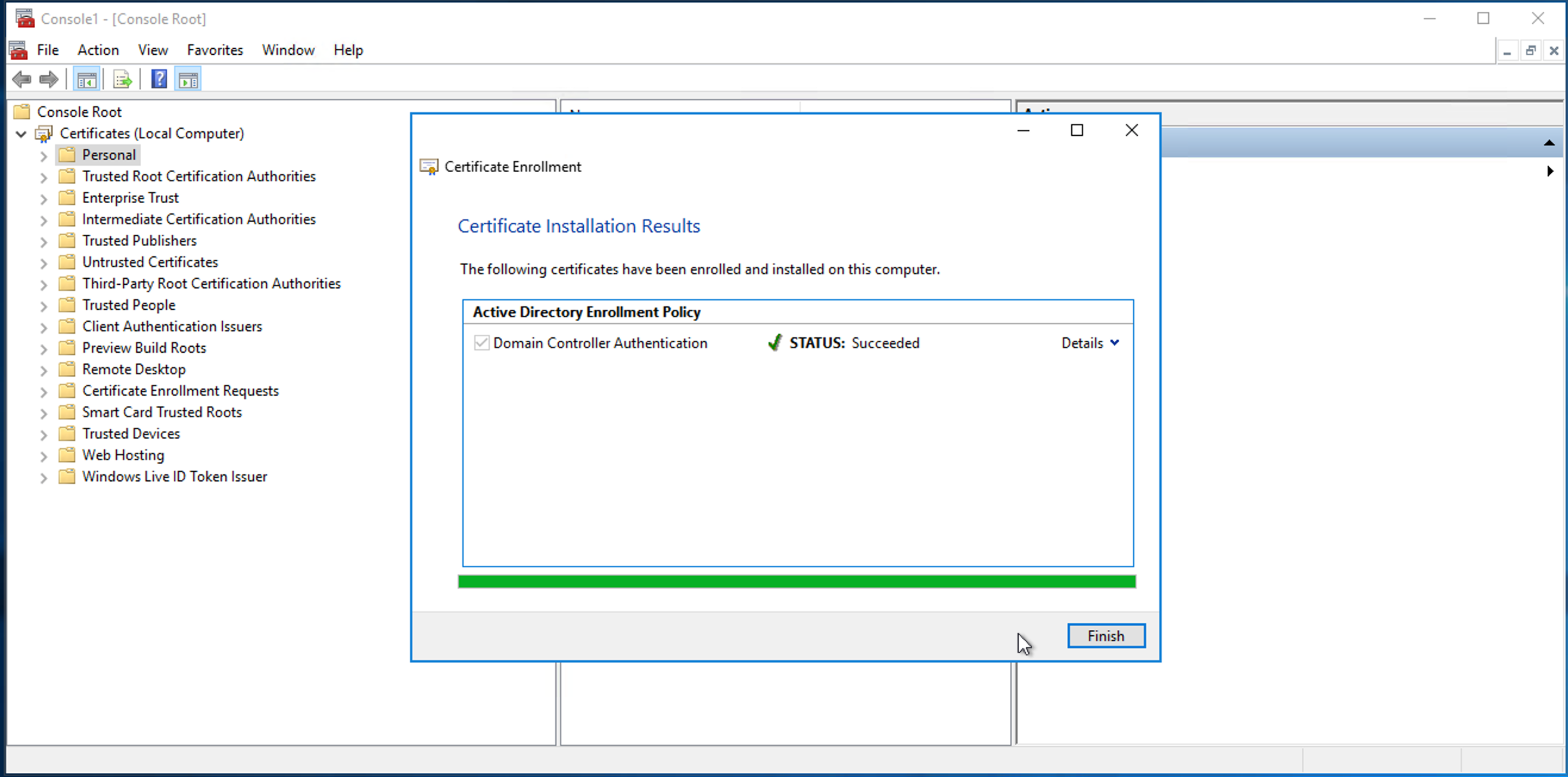
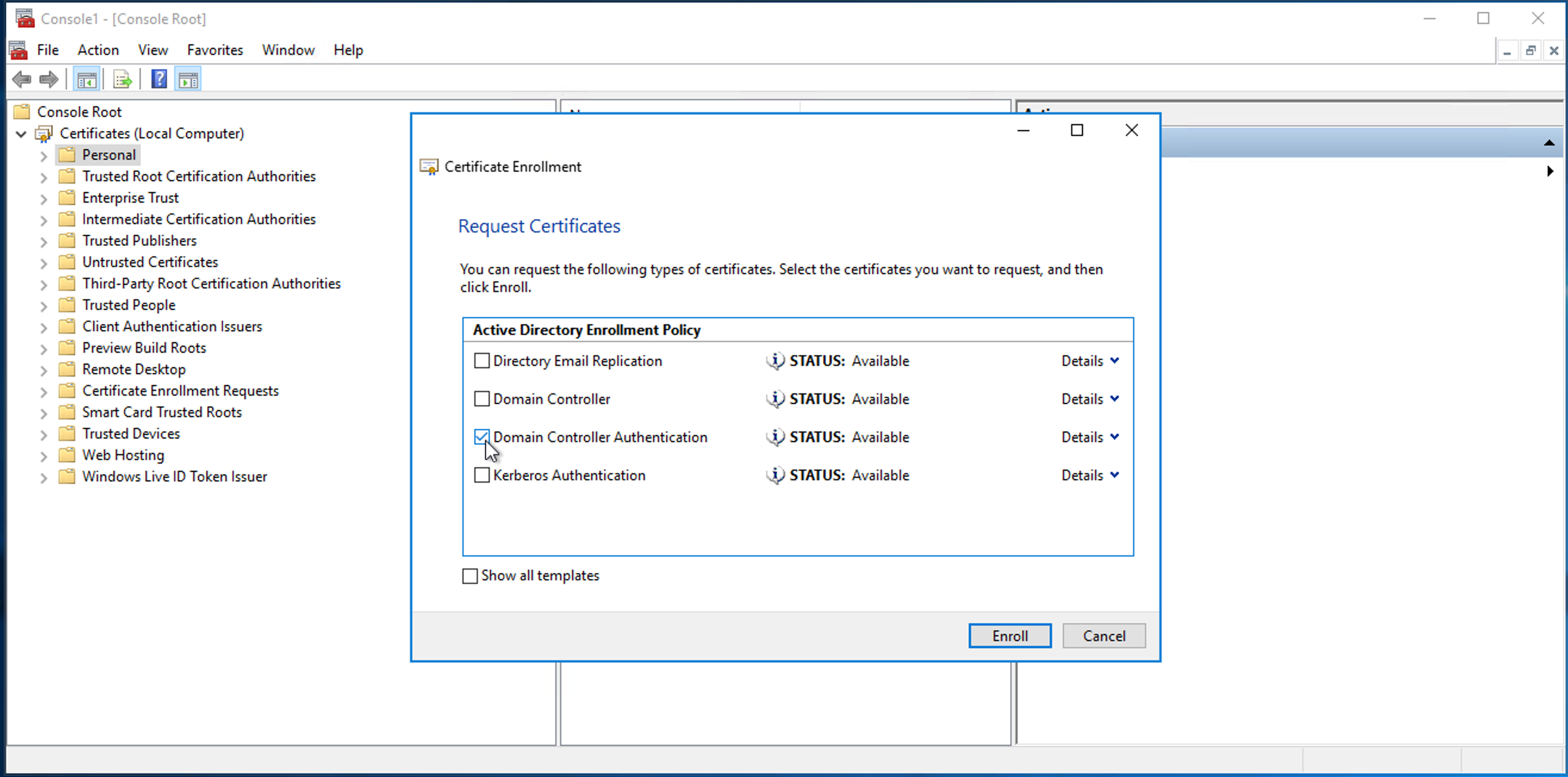
Select Domain Controller Authentication and click Enroll.
-
Click Finish.